Scanning and Enumeration:
nmap:
┌──(root💀kali)-[~]
└─# nmap -sC -sV 10.10.10.88
Starting Nmap 7.92 ( https://nmap.org ) at 2022-02-14 20:36 EST
Nmap scan report for 10.10.10.88
Host is up (0.23s latency).
Not shown: 999 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
| http-robots.txt: 5 disallowed entries
| /webservices/tar/tar/source/
| /webservices/monstra-3.0.4/ /webservices/easy-file-uploader/
|_/webservices/developmental/ /webservices/phpmyadmin/
|_http-title: Landing Page
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 17.48 seconds
發現一個端口是打開的:
✎80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
也可以執行nmapAutomator,進行完整的掃瞄
┌──(root💀kali)-[~/Desktop/OSCP]
└─# ./nmapAutomator.sh 10.10.10.88 All 1 ⚙
Running all scans on 10.10.10.88
Host is likely running Linux
---------------------Starting Nmap Quick Scan---------------------
Starting Nmap 7.92 ( https://nmap.org ) at 2022-02-14 20:31 EST
Nmap scan report for 10.10.10.88
Host is up (0.23s latency).
Not shown: 999 closed tcp ports (reset)
PORT STATE SERVICE
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 2.88 seconds
---------------------Starting Nmap Basic Scan---------------------
Starting Nmap 7.92 ( https://nmap.org ) at 2022-02-14 20:31 EST
Nmap scan report for 10.10.10.88
Host is up (0.22s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Landing Page
| http-robots.txt: 5 disallowed entries
| /webservices/tar/tar/source/
| /webservices/monstra-3.0.4/ /webservices/easy-file-uploader/
|_/webservices/developmental/ /webservices/phpmyadmin/
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.34 seconds
----------------------Starting Nmap UDP Scan----------------------
Starting Nmap 7.92 ( https://nmap.org ) at 2022-02-14 20:32 EST
Warning: 10.10.10.88 giving up on port because retransmission cap hit (1).
Nmap scan report for 10.10.10.88
Host is up (0.22s latency).
All 1000 scanned ports on 10.10.10.88 are in ignored states.
Not shown: 727 open|filtered udp ports (no-response), 273 closed udp ports (port-unreach)
Nmap done: 1 IP address (1 host up) scanned in 269.22 seconds
---------------------Starting Nmap Full Scan----------------------
Starting Nmap 7.92 ( https://nmap.org ) at 2022-02-14 20:36 EST
Initiating Parallel DNS resolution of 1 host. at 20:36
Completed Parallel DNS resolution of 1 host. at 20:36, 0.01s elapsed
Initiating SYN Stealth Scan at 20:36
Scanning 10.10.10.88 [65535 ports]
Discovered open port 80/tcp on 10.10.10.88
Warning: 10.10.10.88 giving up on port because retransmission cap hit (1).
SYN Stealth Scan Timing: About 7.08% done; ETC: 20:43 (0:06:47 remaining)
SYN Stealth Scan Timing: About 11.57% done; ETC: 20:45 (0:07:46 remaining)
SYN Stealth Scan Timing: About 15.42% done; ETC: 20:46 (0:08:19 remaining)
SYN Stealth Scan Timing: About 24.78% done; ETC: 20:46 (0:07:48 remaining)
SYN Stealth Scan Timing: About 30.02% done; ETC: 20:46 (0:07:09 remaining)
SYN Stealth Scan Timing: About 34.96% done; ETC: 20:46 (0:06:38 remaining)
SYN Stealth Scan Timing: About 41.55% done; ETC: 20:46 (0:06:04 remaining)
SYN Stealth Scan Timing: About 47.21% done; ETC: 20:46 (0:05:23 remaining)
SYN Stealth Scan Timing: About 53.45% done; ETC: 20:46 (0:04:38 remaining)
SYN Stealth Scan Timing: About 58.87% done; ETC: 20:46 (0:04:08 remaining)
SYN Stealth Scan Timing: About 64.78% done; ETC: 20:46 (0:03:34 remaining)
SYN Stealth Scan Timing: About 70.50% done; ETC: 20:46 (0:02:57 remaining)
SYN Stealth Scan Timing: About 75.94% done; ETC: 20:46 (0:02:24 remaining)
SYN Stealth Scan Timing: About 81.38% done; ETC: 20:46 (0:01:52 remaining)
SYN Stealth Scan Timing: About 86.81% done; ETC: 20:46 (0:01:20 remaining)
SYN Stealth Scan Timing: About 92.29% done; ETC: 20:46 (0:00:47 remaining)
Completed SYN Stealth Scan at 20:47, 634.34s elapsed (65535 total ports)
Nmap scan report for 10.10.10.88
Host is up (0.22s latency).
Not shown: 65530 closed tcp ports (reset)
PORT STATE SERVICE
80/tcp open http
20555/tcp filtered unknown
45167/tcp filtered unknown
50001/tcp filtered unknown
55565/tcp filtered unknown
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 634.45 seconds
Raw packets sent: 69808 (3.072MB) | Rcvd: 69940 (2.815MB)
No new ports
---------------------Starting Nmap Vulns Scan---------------------
Running CVE scan on basic ports
Starting Nmap 7.92 ( https://nmap.org ) at 2022-02-14 20:47 EST
Nmap scan report for 10.10.10.88
Host is up (0.22s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
| vulners:
| cpe:/a:apache:http_server:2.4.18:
| CVE-2021-44790 7.5 https://vulners.com/cve/CVE-2021-44790
| CVE-2021-39275 7.5 https://vulners.com/cve/CVE-2021-39275
| CVE-2021-26691 7.5 https://vulners.com/cve/CVE-2021-26691
| CVE-2017-7679 7.5 https://vulners.com/cve/CVE-2017-7679
| CVE-2017-7668 7.5 https://vulners.com/cve/CVE-2017-7668
| CVE-2017-3169 7.5 https://vulners.com/cve/CVE-2017-3169
| CVE-2017-3167 7.5 https://vulners.com/cve/CVE-2017-3167
| MSF:ILITIES/REDHAT_LINUX-CVE-2019-0211/ 7.2 https://vulners.com/metasploit/MSF:ILITIES/REDHAT_LINUX-CVE-2019-0211/ *EXPLOIT*
| MSF:ILITIES/IBM-HTTP_SERVER-CVE-2019-0211/ 7.2 https://vulners.com/metasploit/MSF:ILITIES/IBM-HTTP_SERVER-CVE-2019-0211/ *EXPLOIT*
| EXPLOITPACK:44C5118F831D55FAF4259C41D8BDA0AB 7.2 https://vulners.com/exploitpack/EXPLOITPACK:44C5118F831D55FAF4259C41D8BDA0AB *EXPLOIT*
| EDB-ID:46676 7.2 https://vulners.com/exploitdb/EDB-ID:46676 *EXPLOIT*
| CVE-2019-0211 7.2 https://vulners.com/cve/CVE-2019-0211
| 1337DAY-ID-32502 7.2 https://vulners.com/zdt/1337DAY-ID-32502 *EXPLOIT*
| MSF:ILITIES/UBUNTU-CVE-2018-1312/ 6.8 https://vulners.com/metasploit/MSF:ILITIES/UBUNTU-CVE-2018-1312/ *EXPLOIT*
| MSF:ILITIES/UBUNTU-CVE-2017-15715/ 6.8 https://vulners.com/metasploit/MSF:ILITIES/UBUNTU-CVE-2017-15715/ *EXPLOIT*
| MSF:ILITIES/SUSE-CVE-2017-15715/ 6.8 https://vulners.com/metasploit/MSF:ILITIES/SUSE-CVE-2017-15715/ *EXPLOIT*
| MSF:ILITIES/REDHAT_LINUX-CVE-2017-15715/ 6.8 https://vulners.com/metasploit/MSF:ILITIES/REDHAT_LINUX-CVE-2017-15715/ *EXPLOIT*
| MSF:ILITIES/ORACLE_LINUX-CVE-2017-15715/ 6.8 https://vulners.com/metasploit/MSF:ILITIES/ORACLE_LINUX-CVE-2017-15715/ *EXPLOIT*
| MSF:ILITIES/ORACLE-SOLARIS-CVE-2017-15715/ 6.8 https://vulners.com/metasploit/MSF:ILITIES/ORACLE-SOLARIS-CVE-2017-15715/ *EXPLOIT*
| MSF:ILITIES/IBM-HTTP_SERVER-CVE-2017-15715/ 6.8 https://vulners.com/metasploit/MSF:ILITIES/IBM-HTTP_SERVER-CVE-2017-15715/ *EXPLOIT*
| MSF:ILITIES/HUAWEI-EULEROS-2_0_SP3-CVE-2018-1312/ 6.8 https://vulners.com/metasploit/MSF:ILITIES/HUAWEI-EULEROS-2_0_SP3-CVE-2018-1312/ *EXPLOIT*
| MSF:ILITIES/HUAWEI-EULEROS-2_0_SP3-CVE-2017-15715/ 6.8 https://vulners.com/metasploit/MSF:ILITIES/HUAWEI-EULEROS-2_0_SP3-CVE-2017-15715/ *EXPLOIT*
| MSF:ILITIES/HUAWEI-EULEROS-2_0_SP2-CVE-2018-1312/ 6.8 https://vulners.com/metasploit/MSF:ILITIES/HUAWEI-EULEROS-2_0_SP2-CVE-2018-1312/ *EXPLOIT*
| MSF:ILITIES/HUAWEI-EULEROS-2_0_SP2-CVE-2017-15715/ 6.8 https://vulners.com/metasploit/MSF:ILITIES/HUAWEI-EULEROS-2_0_SP2-CVE-2017-15715/ *EXPLOIT*
| MSF:ILITIES/HUAWEI-EULEROS-2_0_SP1-CVE-2018-1312/ 6.8 https://vulners.com/metasploit/MSF:ILITIES/HUAWEI-EULEROS-2_0_SP1-CVE-2018-1312/ *EXPLOIT*
| MSF:ILITIES/HUAWEI-EULEROS-2_0_SP1-CVE-2017-15715/ 6.8 https://vulners.com/metasploit/MSF:ILITIES/HUAWEI-EULEROS-2_0_SP1-CVE-2017-15715/ *EXPLOIT*
| MSF:ILITIES/FREEBSD-CVE-2017-15715/ 6.8 https://vulners.com/metasploit/MSF:ILITIES/FREEBSD-CVE-2017-15715/ *EXPLOIT*
| MSF:ILITIES/DEBIAN-CVE-2017-15715/ 6.8 https://vulners.com/metasploit/MSF:ILITIES/DEBIAN-CVE-2017-15715/ *EXPLOIT*
| MSF:ILITIES/CENTOS_LINUX-CVE-2017-15715/ 6.8 https://vulners.com/metasploit/MSF:ILITIES/CENTOS_LINUX-CVE-2017-15715/ *EXPLOIT*
| MSF:ILITIES/APACHE-HTTPD-CVE-2017-15715/ 6.8 https://vulners.com/metasploit/MSF:ILITIES/APACHE-HTTPD-CVE-2017-15715/ *EXPLOIT*
| MSF:ILITIES/AMAZON_LINUX-CVE-2017-15715/ 6.8 https://vulners.com/metasploit/MSF:ILITIES/AMAZON_LINUX-CVE-2017-15715/ *EXPLOIT*
| MSF:ILITIES/ALPINE-LINUX-CVE-2018-1312/ 6.8 https://vulners.com/metasploit/MSF:ILITIES/ALPINE-LINUX-CVE-2018-1312/ *EXPLOIT*
| MSF:ILITIES/ALPINE-LINUX-CVE-2017-15715/ 6.8 https://vulners.com/metasploit/MSF:ILITIES/ALPINE-LINUX-CVE-2017-15715/ *EXPLOIT*
| FDF3DFA1-ED74-5EE2-BF5C-BA752CA34AE8 6.8 https://vulners.com/githubexploit/FDF3DFA1-ED74-5EE2-BF5C-BA752CA34AE8 *EXPLOIT*
| 4810E2D9-AC5F-5B08-BFB3-DDAFA2F63332 6.8 https://vulners.com/githubexploit/4810E2D9-AC5F-5B08-BFB3-DDAFA2F63332 *EXPLOIT*
| MSF:ILITIES/REDHAT_LINUX-CVE-2019-0217/ 6.0 https://vulners.com/metasploit/MSF:ILITIES/REDHAT_LINUX-CVE-2019-0217/ *EXPLOIT*
| MSF:ILITIES/IBM-HTTP_SERVER-CVE-2019-0217/ 6.0 https://vulners.com/metasploit/MSF:ILITIES/IBM-HTTP_SERVER-CVE-2019-0217/ *EXPLOIT*
| 1337DAY-ID-33577 5.8 https://vulners.com/zdt/1337DAY-ID-33577 *EXPLOIT*
| SSV:96537 5.0 https://vulners.com/seebug/SSV:96537 *EXPLOIT*
| MSF:ILITIES/UBUNTU-CVE-2018-1333/ 5.0 https://vulners.com/metasploit/MSF:ILITIES/UBUNTU-CVE-2018-1333/ *EXPLOIT*
| MSF:ILITIES/UBUNTU-CVE-2018-1303/ 5.0 https://vulners.com/metasploit/MSF:ILITIES/UBUNTU-CVE-2018-1303/ *EXPLOIT*
| MSF:ILITIES/UBUNTU-CVE-2017-15710/ 5.0 https://vulners.com/metasploit/MSF:ILITIES/UBUNTU-CVE-2017-15710/ *EXPLOIT*
| MSF:ILITIES/ORACLE-SOLARIS-CVE-2020-1934/ 5.0 https://vulners.com/metasploit/MSF:ILITIES/ORACLE-SOLARIS-CVE-2020-1934/ *EXPLOIT*
| MSF:ILITIES/ORACLE-SOLARIS-CVE-2017-15710/ 5.0 https://vulners.com/metasploit/MSF:ILITIES/ORACLE-SOLARIS-CVE-2017-15710/ *EXPLOIT*
| MSF:ILITIES/IBM-HTTP_SERVER-CVE-2017-15710/ 5.0 https://vulners.com/metasploit/MSF:ILITIES/IBM-HTTP_SERVER-CVE-2017-15710/ *EXPLOIT*
| MSF:ILITIES/IBM-HTTP_SERVER-CVE-2016-8743/ 5.0 https://vulners.com/metasploit/MSF:ILITIES/IBM-HTTP_SERVER-CVE-2016-8743/ *EXPLOIT*
| MSF:ILITIES/HUAWEI-EULEROS-2_0_SP3-CVE-2017-15710/ 5.0 https://vulners.com/metasploit/MSF:ILITIES/HUAWEI-EULEROS-2_0_SP3-CVE-2017-15710/ *EXPLOIT*
| MSF:ILITIES/HUAWEI-EULEROS-2_0_SP2-CVE-2017-15710/ 5.0 https://vulners.com/metasploit/MSF:ILITIES/HUAWEI-EULEROS-2_0_SP2-CVE-2017-15710/ *EXPLOIT*
| MSF:ILITIES/CENTOS_LINUX-CVE-2017-15710/ 5.0 https://vulners.com/metasploit/MSF:ILITIES/CENTOS_LINUX-CVE-2017-15710/ *EXPLOIT*
| MSF:AUXILIARY/SCANNER/HTTP/APACHE_OPTIONSBLEED 5.0 https://vulners.com/metasploit/MSF:AUXILIARY/SCANNER/HTTP/APACHE_OPTIONSBLEED*EXPLOIT*
| EXPLOITPACK:C8C256BE0BFF5FE1C0405CB0AA9C075D 5.0 https://vulners.com/exploitpack/EXPLOITPACK:C8C256BE0BFF5FE1C0405CB0AA9C075D *EXPLOIT*
| EXPLOITPACK:2666FB0676B4B582D689921651A30355 5.0 https://vulners.com/exploitpack/EXPLOITPACK:2666FB0676B4B582D689921651A30355 *EXPLOIT*
| EDB-ID:42745 5.0 https://vulners.com/exploitdb/EDB-ID:42745 *EXPLOIT*
| EDB-ID:40909 5.0 https://vulners.com/exploitdb/EDB-ID:40909 *EXPLOIT*
| 1337DAY-ID-28573 5.0 https://vulners.com/zdt/1337DAY-ID-28573 *EXPLOIT*
| MSF:ILITIES/ORACLE-SOLARIS-CVE-2019-0197/ 4.9 https://vulners.com/metasploit/MSF:ILITIES/ORACLE-SOLARIS-CVE-2019-0197/ *EXPLOIT*
| MSF:ILITIES/UBUNTU-CVE-2018-1302/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/UBUNTU-CVE-2018-1302/ *EXPLOIT*
| MSF:ILITIES/UBUNTU-CVE-2018-1301/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/UBUNTU-CVE-2018-1301/ *EXPLOIT*
| MSF:ILITIES/HUAWEI-EULEROS-2_0_SP2-CVE-2016-4975/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/HUAWEI-EULEROS-2_0_SP2-CVE-2016-4975/ *EXPLOIT*
| MSF:ILITIES/DEBIAN-CVE-2019-10092/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/DEBIAN-CVE-2019-10092/ *EXPLOIT*
| MSF:ILITIES/APACHE-HTTPD-CVE-2020-11985/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/APACHE-HTTPD-CVE-2020-11985/ *EXPLOIT*
| MSF:ILITIES/APACHE-HTTPD-CVE-2019-10092/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/APACHE-HTTPD-CVE-2019-10092/ *EXPLOIT*
| 4013EC74-B3C1-5D95-938A-54197A58586D 4.3 https://vulners.com/githubexploit/4013EC74-B3C1-5D95-938A-54197A58586D *EXPLOIT*
| 1337DAY-ID-33575 4.3 https://vulners.com/zdt/1337DAY-ID-33575 *EXPLOIT*
| MSF:ILITIES/UBUNTU-CVE-2018-1283/ 3.5 https://vulners.com/metasploit/MSF:ILITIES/UBUNTU-CVE-2018-1283/ *EXPLOIT*
| MSF:ILITIES/REDHAT_LINUX-CVE-2018-1283/ 3.5 https://vulners.com/metasploit/MSF:ILITIES/REDHAT_LINUX-CVE-2018-1283/ *EXPLOIT*
| MSF:ILITIES/ORACLE-SOLARIS-CVE-2018-1283/ 3.5 https://vulners.com/metasploit/MSF:ILITIES/ORACLE-SOLARIS-CVE-2018-1283/ *EXPLOIT*
| MSF:ILITIES/IBM-HTTP_SERVER-CVE-2018-1283/ 3.5 https://vulners.com/metasploit/MSF:ILITIES/IBM-HTTP_SERVER-CVE-2018-1283/ *EXPLOIT*
| MSF:ILITIES/HUAWEI-EULEROS-2_0_SP2-CVE-2018-1283/ 3.5 https://vulners.com/metasploit/MSF:ILITIES/HUAWEI-EULEROS-2_0_SP2-CVE-2018-1283/ *EXPLOIT*
| MSF:ILITIES/CENTOS_LINUX-CVE-2018-1283/ 3.5 https://vulners.com/metasploit/MSF:ILITIES/CENTOS_LINUX-CVE-2018-1283/ *EXPLOIT*
|_ PACKETSTORM:152441 0.0 https://vulners.com/packetstorm/PACKETSTORM:152441 *EXPLOIT*
|_http-server-header: Apache/2.4.18 (Ubuntu)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 11.53 seconds
Running Vuln scan on basic ports
Starting Nmap 7.92 ( https://nmap.org ) at 2022-02-14 20:47 EST
Pre-scan script results:
| broadcast-avahi-dos:
| Discovered hosts:
| 224.0.0.251
| After NULL UDP avahi packet DoS (CVE-2011-1002).
|_ Hosts are all up (not vulnerable).
Nmap scan report for 10.10.10.88
Host is up (0.22s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-csrf: Couldn't find any CSRF vulnerabilities.
| http-enum:
|_ /robots.txt: Robots file
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server's resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| http://ha.ckers.org/slowloris/
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
|_http-dombased-xss: Couldn't find any DOM based XSS.
| vulners:
| cpe:/a:apache:http_server:2.4.18:
| CVE-2021-44790 7.5 https://vulners.com/cve/CVE-2021-44790
| CVE-2021-39275 7.5 https://vulners.com/cve/CVE-2021-39275
| CVE-2021-26691 7.5 https://vulners.com/cve/CVE-2021-26691
| CVE-2017-7679 7.5 https://vulners.com/cve/CVE-2017-7679
| CVE-2017-7668 7.5 https://vulners.com/cve/CVE-2017-7668
| CVE-2017-3169 7.5 https://vulners.com/cve/CVE-2017-3169
| CVE-2017-3167 7.5 https://vulners.com/cve/CVE-2017-3167
| MSF:ILITIES/REDHAT_LINUX-CVE-2019-0211/ 7.2 https://vulners.com/metasploit/MSF:ILITIES/REDHAT_LINUX-CVE-2019-0211/ *EXPLOIT*
| MSF:ILITIES/IBM-HTTP_SERVER-CVE-2019-0211/ 7.2 https://vulners.com/metasploit/MSF:ILITIES/IBM-HTTP_SERVER-CVE-2019-0211/ *EXPLOIT*
| EXPLOITPACK:44C5118F831D55FAF4259C41D8BDA0AB 7.2 https://vulners.com/exploitpack/EXPLOITPACK:44C5118F831D55FAF4259C41D8BDA0AB *EXPLOIT*
| EDB-ID:46676 7.2 https://vulners.com/exploitdb/EDB-ID:46676 *EXPLOIT*
| CVE-2019-0211 7.2 https://vulners.com/cve/CVE-2019-0211
| 1337DAY-ID-32502 7.2 https://vulners.com/zdt/1337DAY-ID-32502 *EXPLOIT*
| MSF:ILITIES/UBUNTU-CVE-2018-1312/ 6.8 https://vulners.com/metasploit/MSF:ILITIES/UBUNTU-CVE-2018-1312/ *EXPLOIT*
| MSF:ILITIES/UBUNTU-CVE-2017-15715/ 6.8 https://vulners.com/metasploit/MSF:ILITIES/UBUNTU-CVE-2017-15715/ *EXPLOIT*
| MSF:ILITIES/SUSE-CVE-2017-15715/ 6.8 https://vulners.com/metasploit/MSF:ILITIES/SUSE-CVE-2017-15715/ *EXPLOIT*
| MSF:ILITIES/REDHAT_LINUX-CVE-2017-15715/ 6.8 https://vulners.com/metasploit/MSF:ILITIES/REDHAT_LINUX-CVE-2017-15715/ *EXPLOIT*
| MSF:ILITIES/ORACLE_LINUX-CVE-2017-15715/ 6.8 https://vulners.com/metasploit/MSF:ILITIES/ORACLE_LINUX-CVE-2017-15715/ *EXPLOIT*
| MSF:ILITIES/ORACLE-SOLARIS-CVE-2017-15715/ 6.8 https://vulners.com/metasploit/MSF:ILITIES/ORACLE-SOLARIS-CVE-2017-15715/ *EXPLOIT*
| MSF:ILITIES/IBM-HTTP_SERVER-CVE-2017-15715/ 6.8 https://vulners.com/metasploit/MSF:ILITIES/IBM-HTTP_SERVER-CVE-2017-15715/ *EXPLOIT*
| MSF:ILITIES/HUAWEI-EULEROS-2_0_SP3-CVE-2018-1312/ 6.8 https://vulners.com/metasploit/MSF:ILITIES/HUAWEI-EULEROS-2_0_SP3-CVE-2018-1312/ *EXPLOIT*
| MSF:ILITIES/HUAWEI-EULEROS-2_0_SP3-CVE-2017-15715/ 6.8 https://vulners.com/metasploit/MSF:ILITIES/HUAWEI-EULEROS-2_0_SP3-CVE-2017-15715/ *EXPLOIT*
| MSF:ILITIES/HUAWEI-EULEROS-2_0_SP2-CVE-2018-1312/ 6.8 https://vulners.com/metasploit/MSF:ILITIES/HUAWEI-EULEROS-2_0_SP2-CVE-2018-1312/ *EXPLOIT*
| MSF:ILITIES/HUAWEI-EULEROS-2_0_SP2-CVE-2017-15715/ 6.8 https://vulners.com/metasploit/MSF:ILITIES/HUAWEI-EULEROS-2_0_SP2-CVE-2017-15715/ *EXPLOIT*
| MSF:ILITIES/HUAWEI-EULEROS-2_0_SP1-CVE-2018-1312/ 6.8 https://vulners.com/metasploit/MSF:ILITIES/HUAWEI-EULEROS-2_0_SP1-CVE-2018-1312/ *EXPLOIT*
| MSF:ILITIES/HUAWEI-EULEROS-2_0_SP1-CVE-2017-15715/ 6.8 https://vulners.com/metasploit/MSF:ILITIES/HUAWEI-EULEROS-2_0_SP1-CVE-2017-15715/ *EXPLOIT*
| MSF:ILITIES/FREEBSD-CVE-2017-15715/ 6.8 https://vulners.com/metasploit/MSF:ILITIES/FREEBSD-CVE-2017-15715/ *EXPLOIT*
| MSF:ILITIES/DEBIAN-CVE-2017-15715/ 6.8 https://vulners.com/metasploit/MSF:ILITIES/DEBIAN-CVE-2017-15715/ *EXPLOIT*
| MSF:ILITIES/CENTOS_LINUX-CVE-2017-15715/ 6.8 https://vulners.com/metasploit/MSF:ILITIES/CENTOS_LINUX-CVE-2017-15715/ *EXPLOIT*
| MSF:ILITIES/APACHE-HTTPD-CVE-2017-15715/ 6.8 https://vulners.com/metasploit/MSF:ILITIES/APACHE-HTTPD-CVE-2017-15715/ *EXPLOIT*
| MSF:ILITIES/AMAZON_LINUX-CVE-2017-15715/ 6.8 https://vulners.com/metasploit/MSF:ILITIES/AMAZON_LINUX-CVE-2017-15715/ *EXPLOIT*
| MSF:ILITIES/ALPINE-LINUX-CVE-2018-1312/ 6.8 https://vulners.com/metasploit/MSF:ILITIES/ALPINE-LINUX-CVE-2018-1312/ *EXPLOIT*
| MSF:ILITIES/ALPINE-LINUX-CVE-2017-15715/ 6.8 https://vulners.com/metasploit/MSF:ILITIES/ALPINE-LINUX-CVE-2017-15715/ *EXPLOIT*
| FDF3DFA1-ED74-5EE2-BF5C-BA752CA34AE8 6.8 https://vulners.com/githubexploit/FDF3DFA1-ED74-5EE2-BF5C-BA752CA34AE8 *EXPLOIT*
| CVE-2021-40438 6.8 https://vulners.com/cve/CVE-2021-40438
| CVE-2020-35452 6.8 https://vulners.com/cve/CVE-2020-35452
| CVE-2018-1312 6.8 https://vulners.com/cve/CVE-2018-1312
| CVE-2017-15715 6.8 https://vulners.com/cve/CVE-2017-15715
| 4810E2D9-AC5F-5B08-BFB3-DDAFA2F63332 6.8 https://vulners.com/githubexploit/4810E2D9-AC5F-5B08-BFB3-DDAFA2F63332 *EXPLOIT*
| CVE-2021-44224 6.4 https://vulners.com/cve/CVE-2021-44224
| CVE-2019-10082 6.4 https://vulners.com/cve/CVE-2019-10082
| CVE-2017-9788 6.4 https://vulners.com/cve/CVE-2017-9788
| MSF:ILITIES/REDHAT_LINUX-CVE-2019-0217/ 6.0 https://vulners.com/metasploit/MSF:ILITIES/REDHAT_LINUX-CVE-2019-0217/ *EXPLOIT*
| MSF:ILITIES/IBM-HTTP_SERVER-CVE-2019-0217/ 6.0 https://vulners.com/metasploit/MSF:ILITIES/IBM-HTTP_SERVER-CVE-2019-0217/ *EXPLOIT*
| CVE-2019-0217 6.0 https://vulners.com/cve/CVE-2019-0217
| CVE-2020-1927 5.8 https://vulners.com/cve/CVE-2020-1927
| CVE-2019-10098 5.8 https://vulners.com/cve/CVE-2019-10098
| 1337DAY-ID-33577 5.8 https://vulners.com/zdt/1337DAY-ID-33577 *EXPLOIT*
| CVE-2016-5387 5.1 https://vulners.com/cve/CVE-2016-5387
| SSV:96537 5.0 https://vulners.com/seebug/SSV:96537 *EXPLOIT*
| MSF:ILITIES/UBUNTU-CVE-2018-1333/ 5.0 https://vulners.com/metasploit/MSF:ILITIES/UBUNTU-CVE-2018-1333/ *EXPLOIT*
| MSF:ILITIES/UBUNTU-CVE-2018-1303/ 5.0 https://vulners.com/metasploit/MSF:ILITIES/UBUNTU-CVE-2018-1303/ *EXPLOIT*
| MSF:ILITIES/UBUNTU-CVE-2017-15710/ 5.0 https://vulners.com/metasploit/MSF:ILITIES/UBUNTU-CVE-2017-15710/ *EXPLOIT*
| MSF:ILITIES/ORACLE-SOLARIS-CVE-2020-1934/ 5.0 https://vulners.com/metasploit/MSF:ILITIES/ORACLE-SOLARIS-CVE-2020-1934/ *EXPLOIT*
| MSF:ILITIES/ORACLE-SOLARIS-CVE-2017-15710/ 5.0 https://vulners.com/metasploit/MSF:ILITIES/ORACLE-SOLARIS-CVE-2017-15710/ *EXPLOIT*
| MSF:ILITIES/IBM-HTTP_SERVER-CVE-2017-15710/ 5.0 https://vulners.com/metasploit/MSF:ILITIES/IBM-HTTP_SERVER-CVE-2017-15710/ *EXPLOIT*
| MSF:ILITIES/IBM-HTTP_SERVER-CVE-2016-8743/ 5.0 https://vulners.com/metasploit/MSF:ILITIES/IBM-HTTP_SERVER-CVE-2016-8743/ *EXPLOIT*
| MSF:ILITIES/HUAWEI-EULEROS-2_0_SP3-CVE-2017-15710/ 5.0 https://vulners.com/metasploit/MSF:ILITIES/HUAWEI-EULEROS-2_0_SP3-CVE-2017-15710/ *EXPLOIT*
| MSF:ILITIES/HUAWEI-EULEROS-2_0_SP2-CVE-2017-15710/ 5.0 https://vulners.com/metasploit/MSF:ILITIES/HUAWEI-EULEROS-2_0_SP2-CVE-2017-15710/ *EXPLOIT*
| MSF:ILITIES/CENTOS_LINUX-CVE-2017-15710/ 5.0 https://vulners.com/metasploit/MSF:ILITIES/CENTOS_LINUX-CVE-2017-15710/ *EXPLOIT*
| MSF:AUXILIARY/SCANNER/HTTP/APACHE_OPTIONSBLEED 5.0 https://vulners.com/metasploit/MSF:AUXILIARY/SCANNER/HTTP/APACHE_OPTIONSBLEED*EXPLOIT*
| EXPLOITPACK:C8C256BE0BFF5FE1C0405CB0AA9C075D 5.0 https://vulners.com/exploitpack/EXPLOITPACK:C8C256BE0BFF5FE1C0405CB0AA9C075D *EXPLOIT*
| EXPLOITPACK:2666FB0676B4B582D689921651A30355 5.0 https://vulners.com/exploitpack/EXPLOITPACK:2666FB0676B4B582D689921651A30355 *EXPLOIT*
| EDB-ID:42745 5.0 https://vulners.com/exploitdb/EDB-ID:42745 *EXPLOIT*
| EDB-ID:40909 5.0 https://vulners.com/exploitdb/EDB-ID:40909 *EXPLOIT*
| CVE-2021-34798 5.0 https://vulners.com/cve/CVE-2021-34798
| CVE-2021-33193 5.0 https://vulners.com/cve/CVE-2021-33193
| CVE-2021-26690 5.0 https://vulners.com/cve/CVE-2021-26690
| CVE-2020-1934 5.0 https://vulners.com/cve/CVE-2020-1934
| CVE-2019-17567 5.0 https://vulners.com/cve/CVE-2019-17567
| CVE-2019-0220 5.0 https://vulners.com/cve/CVE-2019-0220
| CVE-2019-0196 5.0 https://vulners.com/cve/CVE-2019-0196
| CVE-2018-17199 5.0 https://vulners.com/cve/CVE-2018-17199
| CVE-2018-17189 5.0 https://vulners.com/cve/CVE-2018-17189
| CVE-2018-1333 5.0 https://vulners.com/cve/CVE-2018-1333
| CVE-2018-1303 5.0 https://vulners.com/cve/CVE-2018-1303
| CVE-2017-9798 5.0 https://vulners.com/cve/CVE-2017-9798
| CVE-2017-15710 5.0 https://vulners.com/cve/CVE-2017-15710
| CVE-2016-8743 5.0 https://vulners.com/cve/CVE-2016-8743
| CVE-2016-8740 5.0 https://vulners.com/cve/CVE-2016-8740
| CVE-2016-4979 5.0 https://vulners.com/cve/CVE-2016-4979
| 1337DAY-ID-28573 5.0 https://vulners.com/zdt/1337DAY-ID-28573 *EXPLOIT*
| MSF:ILITIES/ORACLE-SOLARIS-CVE-2019-0197/ 4.9 https://vulners.com/metasploit/MSF:ILITIES/ORACLE-SOLARIS-CVE-2019-0197/ *EXPLOIT*
| CVE-2019-0197 4.9 https://vulners.com/cve/CVE-2019-0197
| MSF:ILITIES/UBUNTU-CVE-2018-1302/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/UBUNTU-CVE-2018-1302/ *EXPLOIT*
| MSF:ILITIES/UBUNTU-CVE-2018-1301/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/UBUNTU-CVE-2018-1301/ *EXPLOIT*
| MSF:ILITIES/HUAWEI-EULEROS-2_0_SP2-CVE-2016-4975/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/HUAWEI-EULEROS-2_0_SP2-CVE-2016-4975/ *EXPLOIT*
| MSF:ILITIES/DEBIAN-CVE-2019-10092/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/DEBIAN-CVE-2019-10092/ *EXPLOIT*
| MSF:ILITIES/APACHE-HTTPD-CVE-2020-11985/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/APACHE-HTTPD-CVE-2020-11985/ *EXPLOIT*
| MSF:ILITIES/APACHE-HTTPD-CVE-2019-10092/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/APACHE-HTTPD-CVE-2019-10092/ *EXPLOIT*
| CVE-2020-11985 4.3 https://vulners.com/cve/CVE-2020-11985
| CVE-2019-10092 4.3 https://vulners.com/cve/CVE-2019-10092
| CVE-2018-1302 4.3 https://vulners.com/cve/CVE-2018-1302
| CVE-2018-1301 4.3 https://vulners.com/cve/CVE-2018-1301
| CVE-2018-11763 4.3 https://vulners.com/cve/CVE-2018-11763
| CVE-2016-4975 4.3 https://vulners.com/cve/CVE-2016-4975
| CVE-2016-1546 4.3 https://vulners.com/cve/CVE-2016-1546
| 4013EC74-B3C1-5D95-938A-54197A58586D 4.3 https://vulners.com/githubexploit/4013EC74-B3C1-5D95-938A-54197A58586D *EXPLOIT*
| 1337DAY-ID-33575 4.3 https://vulners.com/zdt/1337DAY-ID-33575 *EXPLOIT*
| MSF:ILITIES/UBUNTU-CVE-2018-1283/ 3.5 https://vulners.com/metasploit/MSF:ILITIES/UBUNTU-CVE-2018-1283/ *EXPLOIT*
| MSF:ILITIES/REDHAT_LINUX-CVE-2018-1283/ 3.5 https://vulners.com/metasploit/MSF:ILITIES/REDHAT_LINUX-CVE-2018-1283/ *EXPLOIT*
| MSF:ILITIES/ORACLE-SOLARIS-CVE-2018-1283/ 3.5 https://vulners.com/metasploit/MSF:ILITIES/ORACLE-SOLARIS-CVE-2018-1283/ *EXPLOIT*
| MSF:ILITIES/IBM-HTTP_SERVER-CVE-2018-1283/ 3.5 https://vulners.com/metasploit/MSF:ILITIES/IBM-HTTP_SERVER-CVE-2018-1283/ *EXPLOIT*
| MSF:ILITIES/HUAWEI-EULEROS-2_0_SP2-CVE-2018-1283/ 3.5 https://vulners.com/metasploit/MSF:ILITIES/HUAWEI-EULEROS-2_0_SP2-CVE-2018-1283/ *EXPLOIT*
| MSF:ILITIES/CENTOS_LINUX-CVE-2018-1283/ 3.5 https://vulners.com/metasploit/MSF:ILITIES/CENTOS_LINUX-CVE-2018-1283/ *EXPLOIT*
| CVE-2018-1283 3.5 https://vulners.com/cve/CVE-2018-1283
| CVE-2016-8612 3.3 https://vulners.com/cve/CVE-2016-8612
|_ PACKETSTORM:152441 0.0 https://vulners.com/packetstorm/PACKETSTORM:152441 *EXPLOIT*
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 356.87 seconds
---------------------Recon Recommendations----------------------
Web Servers Recon:
gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -l -t 30 -e -k -x .html,.php -u http://10.10.10.88:80 -o recon/gobuster_10.10.10.88_80.txt
nikto -host 10.10.10.88:80 | tee recon/nikto_10.10.10.88_80.txt
Which commands would you like to run?
All (Default), gobuster, nikto, Skip <!>
Running Default in (1) s:
---------------------Running Recon Commands----------------------
Starting gobuster scan
Error: unknown shorthand flag: 'l' in -l
Finished gobuster scan
=========================
Starting nikto scan
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.10.88
+ Target Hostname: 10.10.10.88
+ Target Port: 80
+ Start Time: 2022-02-14 20:53:47 (GMT-5)
---------------------------------------------------------------------------
+ Server: Apache/2.4.18 (Ubuntu)
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Cookie PHPSESSID created without the httponly flag
+ Entry '/webservices/monstra-3.0.4/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ "robots.txt" contains 5 entries which should be manually viewed.
+ Apache/2.4.18 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Server may leak inodes via ETags, header found with file /, inode: 2a0e, size: 565becf5ff08d, mtime: gzip
+ Allowed HTTP Methods: OPTIONS, GET, HEAD, POST
+ OSVDB-3233: /icons/README: Apache default file found.
+ 7881 requests: 0 error(s) and 10 item(s) reported on remote host
+ End Time: 2022-02-14 21:24:43 (GMT-5) (1856 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
Finished nikto scan
=========================
---------------------Finished all Nmap scans---------------------
Completed in 52 minute(s) and 57 second(s)
gobuster:
┌──(root💀kali)-[~]
└─# gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u 10.10.10.88 -t 100
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.10.88
[+] Method: GET
[+] Threads: 100
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2022/02/14 21:54:58 Starting gobuster in directory enumeration mode
===============================================================
/webservices (Status: 301) [Size: 316] [--> http://10.10.10.88/webservices/]
/server-status (Status: 403) [Size: 299]
===============================================================
2022/02/14 22:03:20 Finished
===============================================================
User-agent: *
Disallow: /webservices/tar/tar/source/
Disallow: /webservices/monstra-3.0.4/
Disallow: /webservices/easy-file-uploader/
Disallow: /webservices/developmental/
Disallow: /webservices/phpmyadmin/
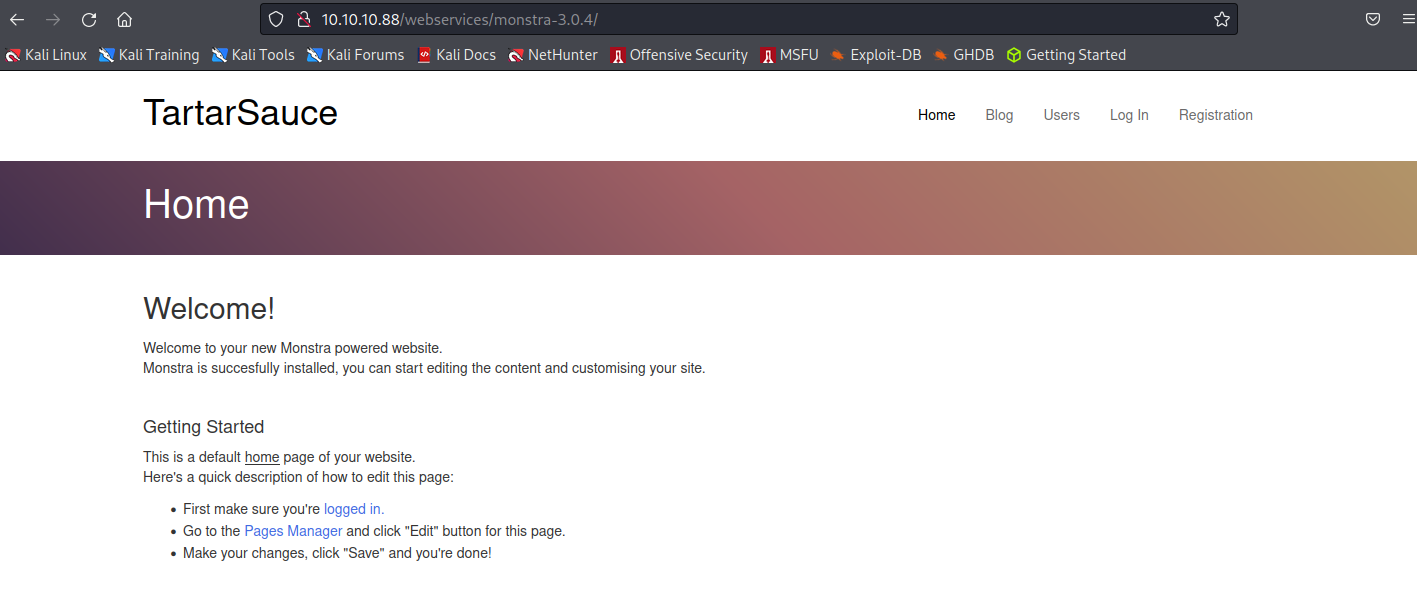
當中只有/webservices/monstra-3.0.4/是真實並且可以訪問的頁面
這是叫做Monstra的CMS,版本號是3.0.4
searchsploit Monstra 3.0.4
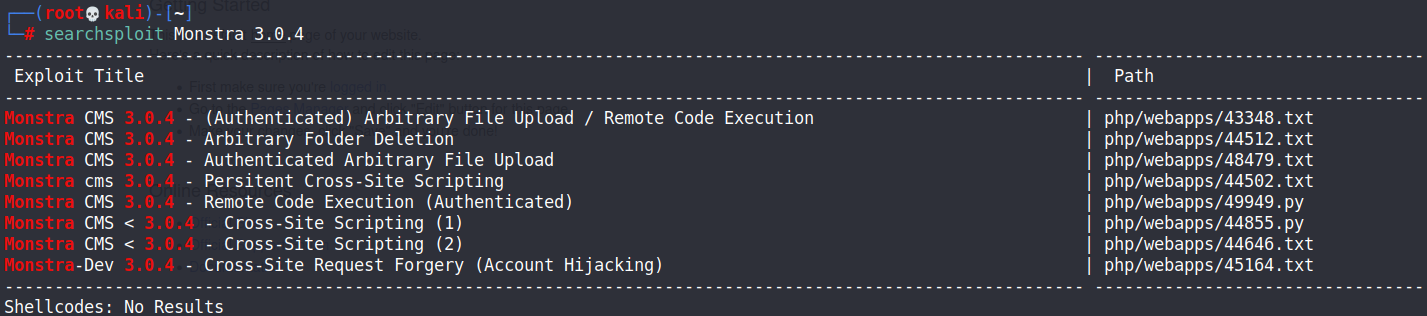
3.0.4這個版本有RCE的漏洞存在,可以嘗試看看Monstra CMS 3.0.4 – (Authenticated) Arbitrary File Upload / Remote Code Execution
使用之前要先找到登入CMS的帳號密碼,簡單測試一下 admin/admin